Question: a) Demonstrate how you can construct an Iterative Hash h function using the Merkle- Damgard Design. Use as your compression function , AES with 512-bit
a) Demonstrate how you can construct an Iterative Hash h function using the Merkle- Damgard Design. Use as your compression function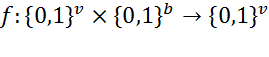 , AES with 512-bit keys. Explain what the values of v and b will be in your compression function and where in the block cipher (AES) are you using the blocks of the message you want to hash.
, AES with 512-bit keys. Explain what the values of v and b will be in your compression function and where in the block cipher (AES) are you using the blocks of the message you want to hash.
b) Using the iterative hash function you just create above, show how a digest for a 1536- bit long message will be produced.
c) Finally explain how you can use the Hash function h you created above in order to generate a MAC. What is the name of the main security property we care about in MACs and how is it defined?
d) Explain whether and why the following construction for a MAC is good: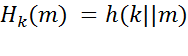 where:
where: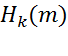 the MAC of message m using secret key k and h the Hash function you create in the first step of this question. (|| is the symbol for string concatenation).
the MAC of message m using secret key k and h the Hash function you create in the first step of this question. (|| is the symbol for string concatenation).
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


