Question: a) Identify and discuss the algorithm shown in Figure 1. Which keys should be used in the red text boxes labelled as key 1 and
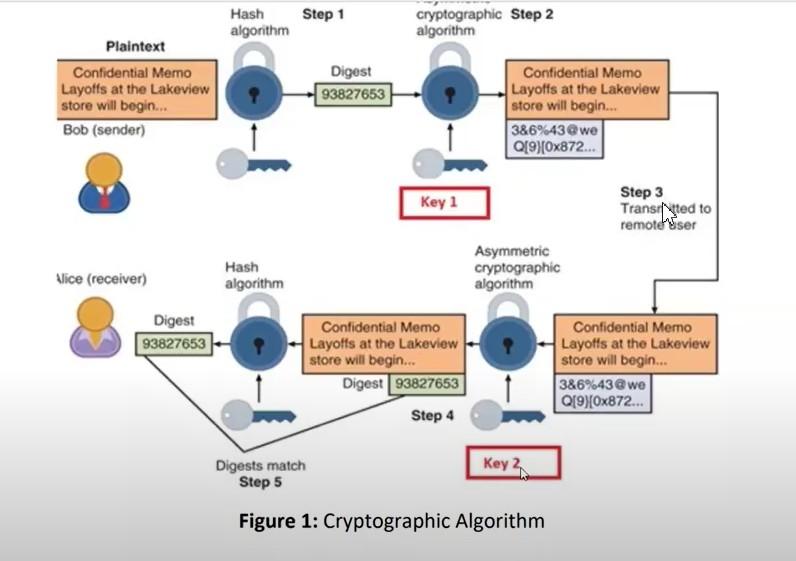
a) Identify and discuss the algorithm shown in Figure 1. Which keys should be used in the red text boxes labelled as key 1 and key 2? Now, if Bob also wants to send the encrypted message to Alice, which encryption technique should be used? Identify the keys used to encrypt and decrypt the memo. Hash algorithm Step 1 cryptographic Step 2 algorithm Plaintext Confidential Memo Layoffs at the Lakeview store will begin... Bob (sender) Digest 93827653 Confidential Memo Layoffs at the Lakeview store will begin... 386%43@we Q[9][0x872... Key 1 Step 3 Transisted to remotesser Alice (receiver) Hash algorithm Asymmetric cryptographic algorithm Digest 93827653 Confidential Memo Layoffs at the Lakeview store will begin... Digest 93827653 Confidential Memo Layoffs at the Lakeview store will begin... 386%43@we Q[9)[0x872... Step 4 Digests match Step 5 Key 2 Figure 1: Cryptographic Algorithm
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


