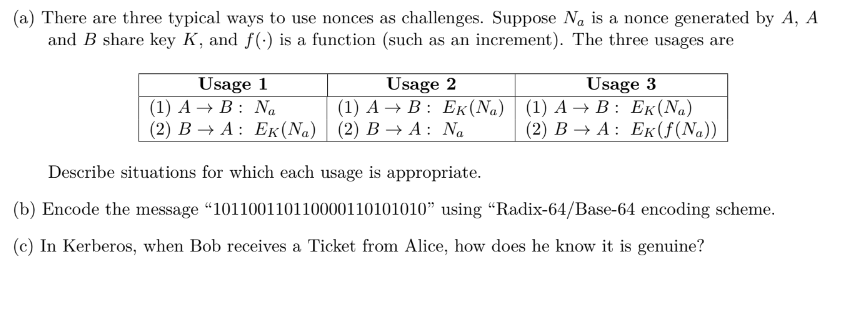
Question: ( a ) There are three typical ways to use nonces as challenges. Suppose N a is a nonce generated by A , A and
a There are three typical ways to use nonces as challenges. Suppose is a nonce generated by
and share key and is a function such as an increment The three usages are
Describe situations for which each usage is appropriate.
b Encode the message using "RadixBase encoding scheme.
c In Kerberos, when Bob receives a Ticket from Alice, how does he know it is genuine?
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


