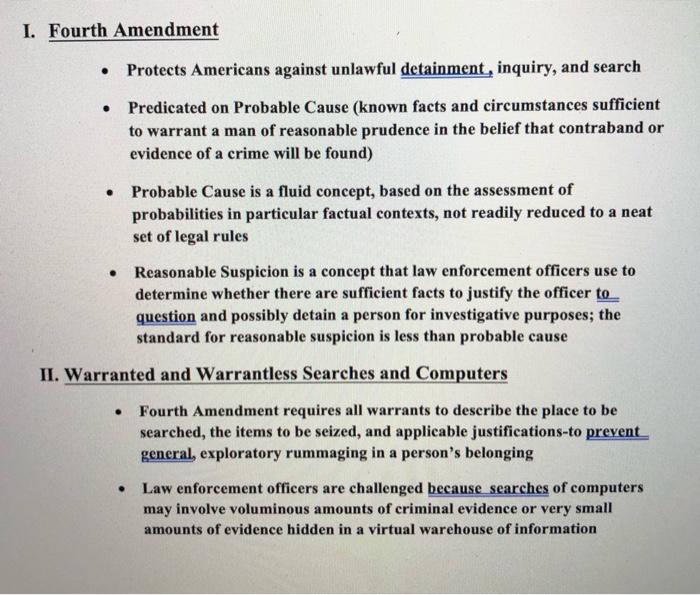
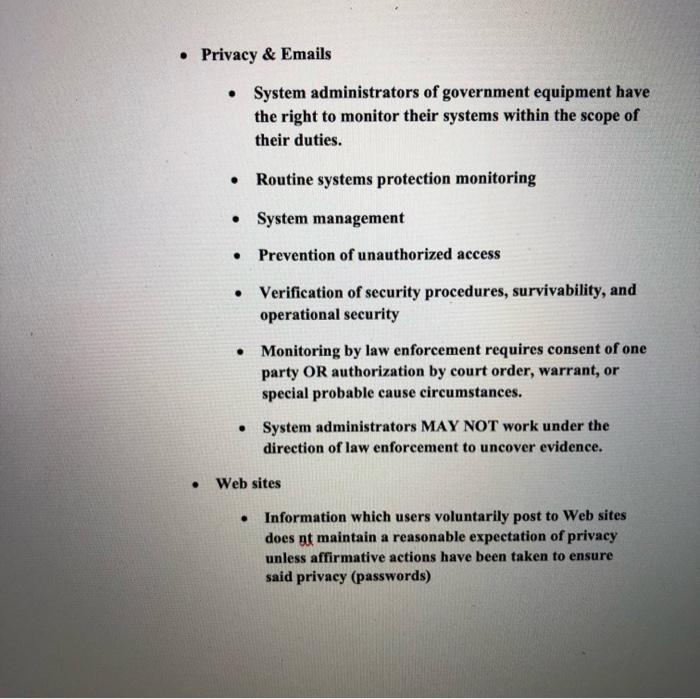
Question: After reading the lecture notes answer the following questions. 1. Describe the circumstances where a search warrant may be waived prior to a search. 2.



Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


