Question: Alright, so it's been a while since I've had a network class, and I've completely forgotten how to configure these ACL rules, especially regarding the
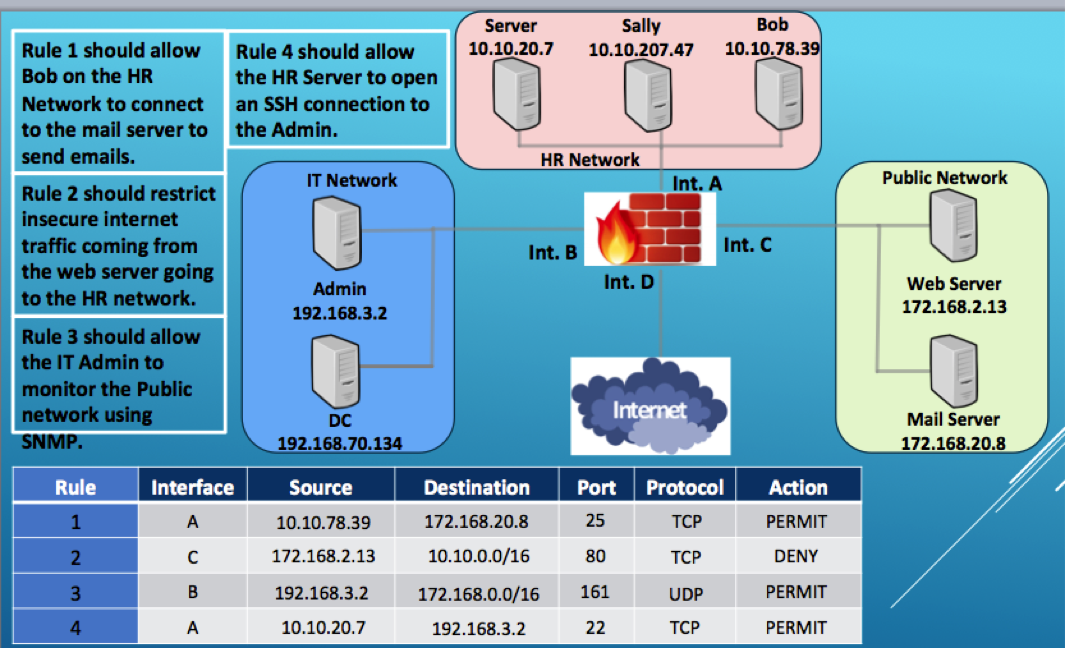
Alright, so it's been a while since I've had a network class, and I've completely forgotten how to configure these ACL rules, especially regarding the destination subnet for what this question is asking me to do.
Can you please explain and show me, a fast and simple way to recognize when I would need to translate the IP to resemble what it's listed as in Rule 2. For example, why is there a /16 and why are the 0s added? And when I would I know when to add the / and when I should not?
Thanks in advance.
Server 10.10.20.7 Sally 10.10.207.47 Bob 10.10.78.39 Rule 4 should allow the HR Server to open an SSH connection to the Admin. HR Network Rule 1 should allow Bob on the HR Network to connect to the mail server to send emails. Rule 2 should restrict insecure internet traffic coming from the web server going to the HR network. IT Network Int. A Public Network Int. B Int. C Int. D Admin 192.168.3.2 Web Server 172.168.2.13 Rule 3 should allow the IT Admin to monitor the Public network using SNMP. Internet DC Mail Server 172.168.20.8 192.168.70.134 Source Action Rule 1 Interface Destination 172.168.20.8 10.10.0.0/16 Protocol TCP 10.10.78.39 PERMIT Port 25 80 161 22 TCP DENY 172.168.2.13 192.168.3.2 10.10.20.7 3 PERMIT 172.168.0.0/16 192.168.3.2 UDP TCP . PERMIT
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


