Question: Analysis Skills (Develop a Secure Network): From the following case study identify the vulnerability, threat, risk and countermeasures (controls) and fill the following table. Check
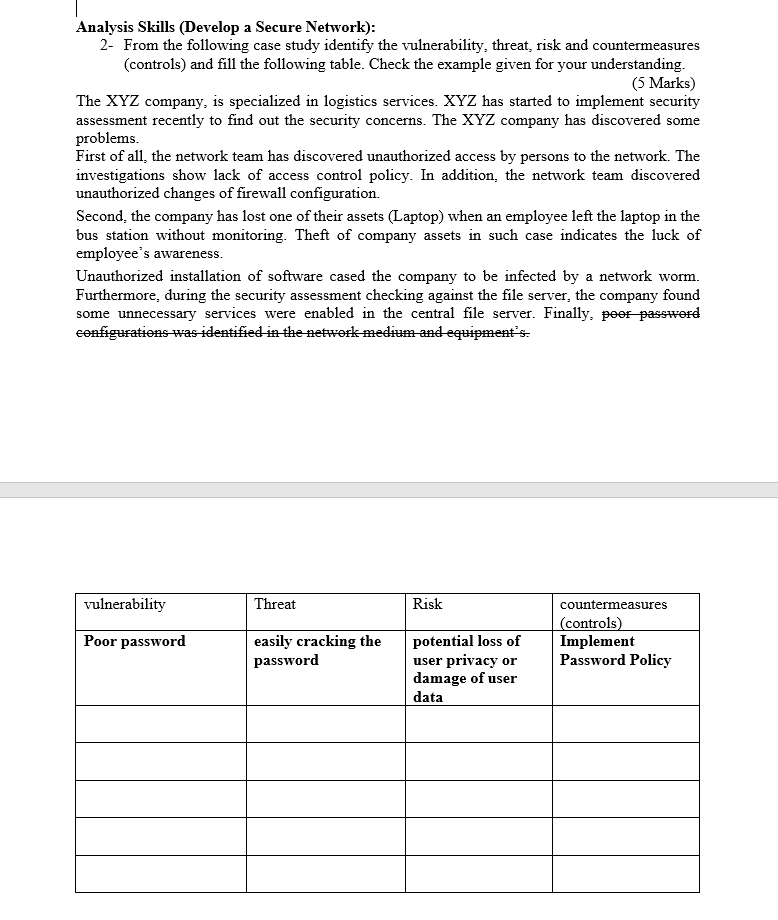
Analysis Skills (Develop a Secure Network):
- From the following case study identify the vulnerability, threat, risk and countermeasures (controls) and fill the following table. Check the example given for your understanding.
The XYZ company, is specialized in logistics services. XYZ has started to implement security assessment recently to find out the security concerns. The XYZ company has discovered some problems.
First of all, the network team has discovered unauthorized access by persons to the network. The investigations show lack of access control policy. In addition, the network team discovered unauthorized changes of firewall configuration.
Second, the company has lost one of their assets (Laptop) when an employee left the laptop in the bus station without monitoring. Theft of company assets in such case indicates the luck of employees awareness.
Unauthorized installation of software cased the company to be infected by a network worm. Furthermore, during the security assessment checking against the file server, the company found some unnecessary services were enabled in the central file server. Finally, poor password configurations was identified in the network medium and equipments.
Analysis Skills (Develop a Secure Network): 2- From the following case study identify the vulnerability, threat, risk and countermeasures (controls) and fill the following table. Check the example given for your understanding. (5 Marks) The XYZ company, is specialized in logistics services. XYZ has started to implement security assessment recently to find out the security concerns. The XYZ company has discovered some problems. First of all, the network team has discovered unauthorized access by persons to the network. The investigations show lack of access control policy. In addition, the network team discovered unauthorized changes of firewall configuration. Second, the company has lost one of their assets (Laptop) when an employee left the laptop in the bus station without monitoring. Theft of company assets in such case indicates the luck of employee's awareness. Unauthorized installation of software cased the company to be infected by a network worm. Furthermore, during the security assessment checking against the file server, the company found some unnecessary services were enabled in the central file server. Finally, peor password configurations was identified in the network medium and equipment's. vulnerability Threat Risk Poor password countermeasures (controls) Implement Password Policy easily cracking the password potential loss of user privacy or damage of user data Analysis Skills (Develop a Secure Network): 2- From the following case study identify the vulnerability, threat, risk and countermeasures (controls) and fill the following table. Check the example given for your understanding. (5 Marks) The XYZ company, is specialized in logistics services. XYZ has started to implement security assessment recently to find out the security concerns. The XYZ company has discovered some problems. First of all, the network team has discovered unauthorized access by persons to the network. The investigations show lack of access control policy. In addition, the network team discovered unauthorized changes of firewall configuration. Second, the company has lost one of their assets (Laptop) when an employee left the laptop in the bus station without monitoring. Theft of company assets in such case indicates the luck of employee's awareness. Unauthorized installation of software cased the company to be infected by a network worm. Furthermore, during the security assessment checking against the file server, the company found some unnecessary services were enabled in the central file server. Finally, peor password configurations was identified in the network medium and equipment's. vulnerability Threat Risk Poor password countermeasures (controls) Implement Password Policy easily cracking the password potential loss of user privacy or damage of user data
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


