Question: Answer all for a thumbs up QUESTION 1 A rootkit uses a directed broadcast to create a flood of network traffic for the victim computer.
Answer all for a thumbs up 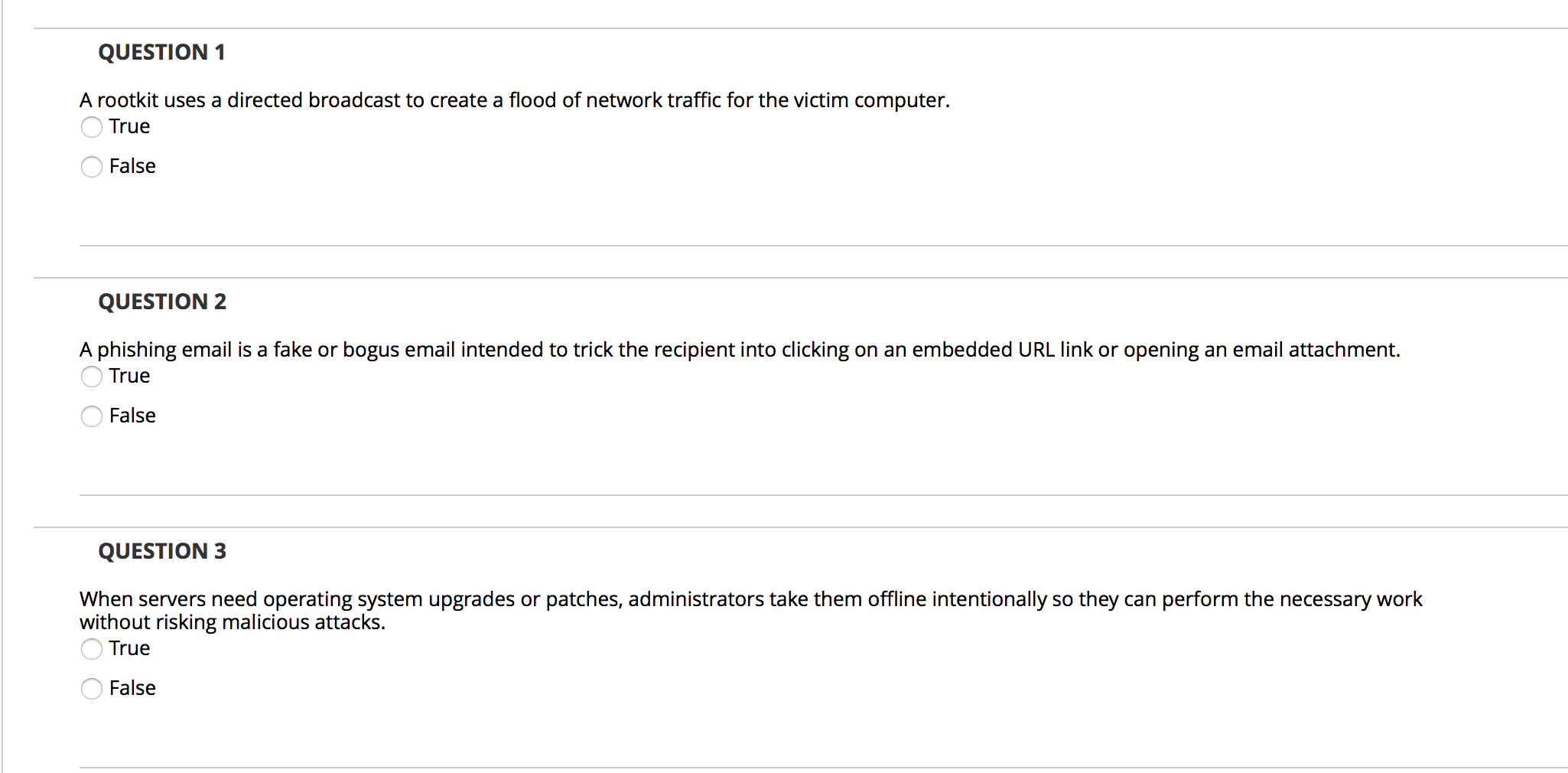
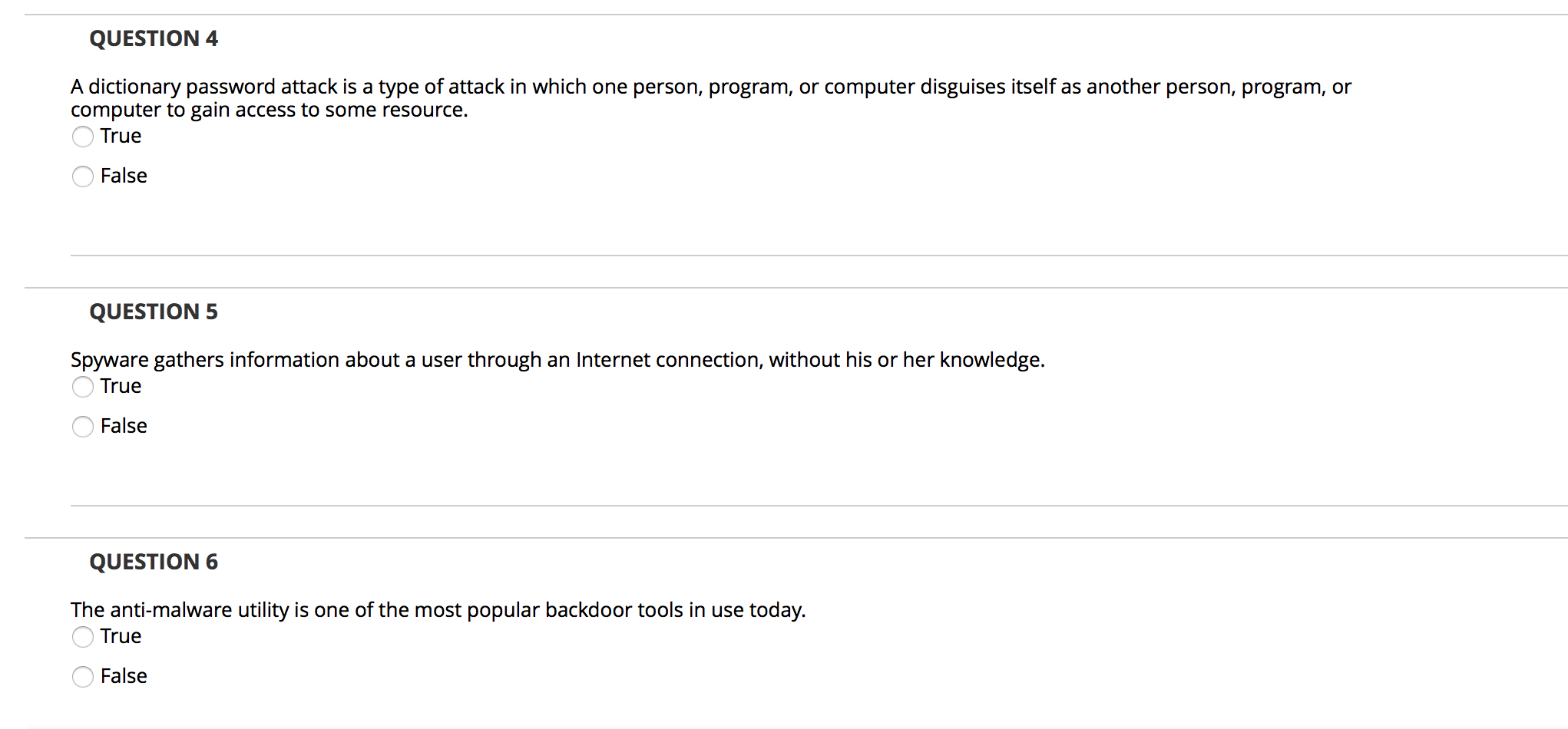
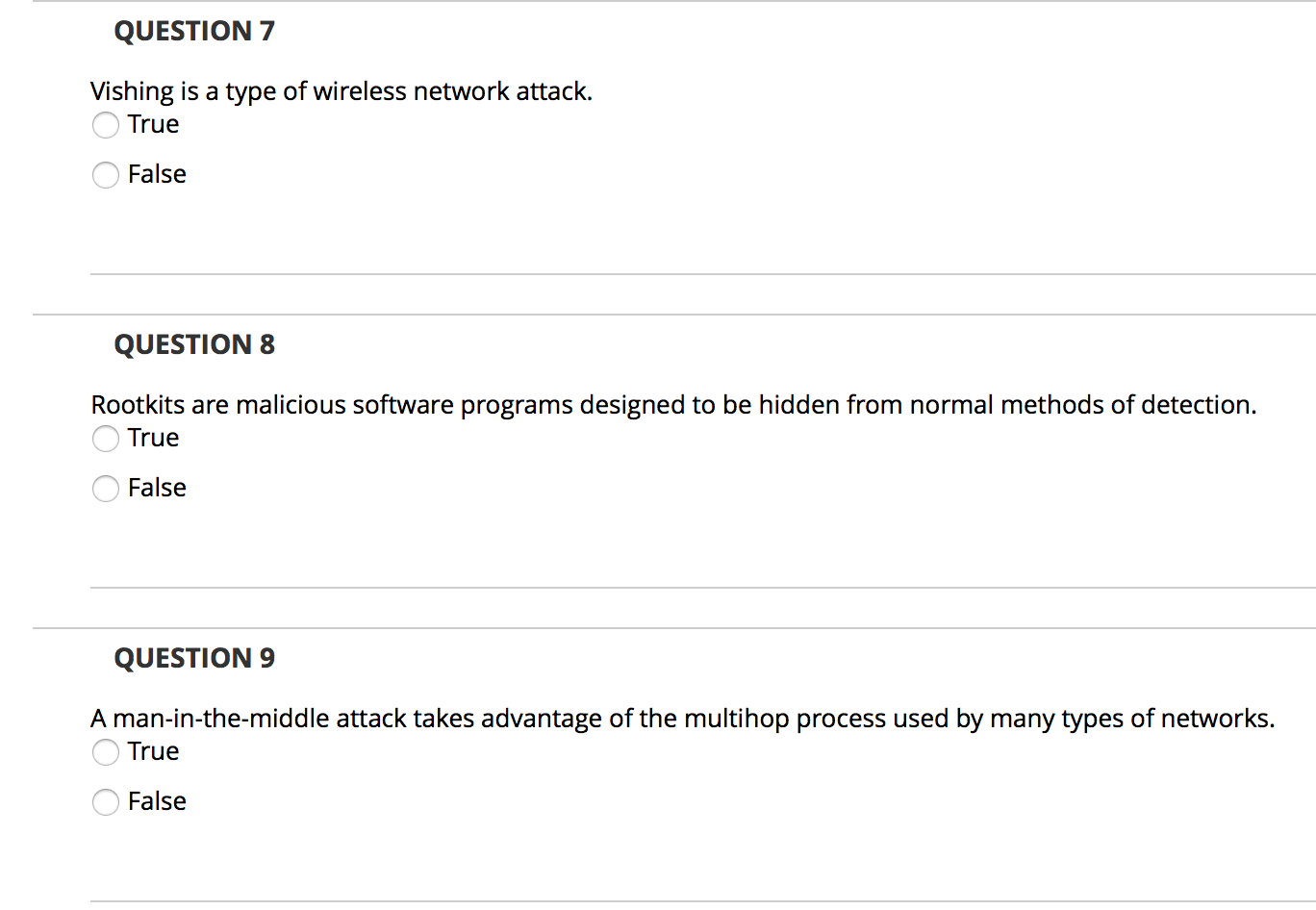
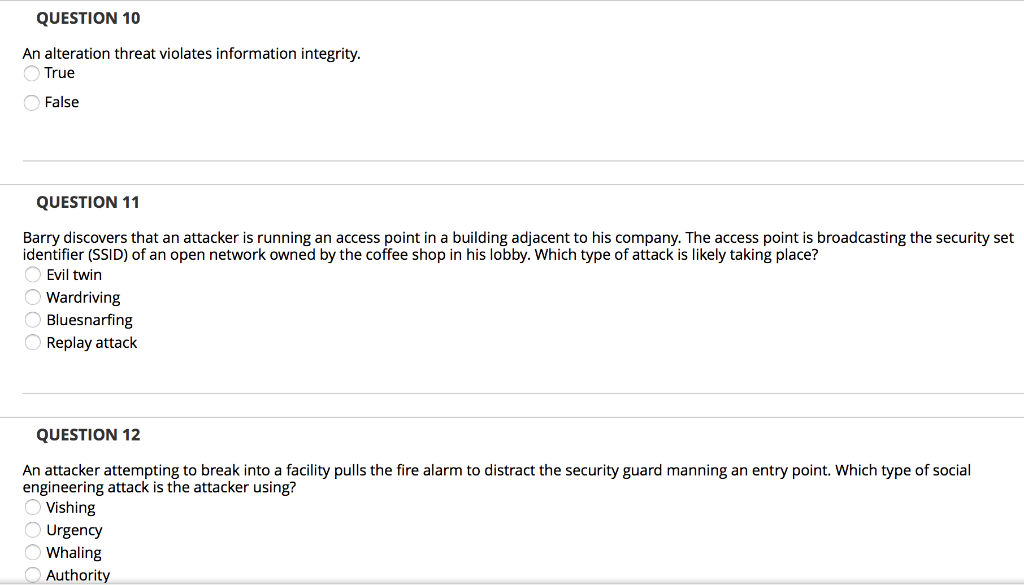
QUESTION 1 A rootkit uses a directed broadcast to create a flood of network traffic for the victim computer. True False QUESTION 2 A phishing email is a fake or bogus email intended to trick the recipient into clicking on an embedded URL link or opening an email attachment. True False QUESTION 3 When servers need operating system upgrades or patches, administrators take them offline intentionally so they can perform the necessary work without risking malicious attacks. True False QUESTION 4 A dictionary password attack is a type of attack in which one person, program, or computer disguises itself as another person, program, or computer to gain access to some resource. True False QUESTION 5 Spyware gathers information about a user through an Internet connection, without his or her knowledge. True False QUESTION 6 The anti-malware utility is one of the most popular backdoor tools in use today. True False QUESTION 7 Vishing is a type of wireless network attack. True False QUESTION 8 Rootkits are malicious software programs designed to be hidden from normal methods of detection. True False QUESTION 9 A man-in-the-middle attack takes advantage of the multihop process used by many types of networks. True False QUESTION 10 An alteration threat violates information integrity. True False QUESTION 11 Barry discovers that an attacker is running an access point in a building adjacent to his company. The access point is broadcasting the security set identifier (SSID) of an open network owned by the coffee shop in his lobby. Which type of attack is likely taking place? Evil twin Wardriving Bluesnarfing Replay attack QUESTION 12 An attacker attempting to break into a facility pulls the fire alarm to distract the security guard manning an entry point. Which type of social engineering attack is the attacker using? Vishing Urgency Whaling Authority QUESTION 13 Maria's company recently experienced a major system outage due to the failure of a critical component. During that time period, the company did not register any sales through its online site. Which type of loss did the company experience as a result of lost sales? Replacement cost Opportunity cost Manpower cost Cost of good sold QUESTION 14 Which control is not designed to combat malware? Firewalls Antivirus software Awareness and education efforts Quarantine computers QUESTION 15 In which type of attack does the attacker attempt to take over an existing connection between two systems? Man-in-the-middle attack URL hijacking Session hijacking Typosquatting QUESTION 16 Florian recently purchased a set of domain names that are similar to those of legitimate websites and used the newly purchased sites to host malware. Which type of attack is Florian using? Cross-site scripting Session hijacking SQL injection Typosquatting QUESTION 17 Which type of denial of service attack exploits the existence of software flaws to disrupt a service? SYN flood attack Smurf attack Logic attack Flooding attack QUESTION 18 Which password attack is typically used specifically against password files that contain cryptographic hashes? Brute-force attacks Dictionary attacks Birthday attacks O Social engineering attacks QUESTION 19 Users throughout Alison's organization have been receiving unwanted commercial messages over the organization's instant messaging program. What type of attack is taking place? Spam Phishing Social engineering Spim QUESTION 20 Which type of attack involves the creation of some deception in order to trick unsuspecting users? O Interception Interruption Fabrication Modification
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


