Question: Answer all for a thumbs up! QUESTION 1 Deterrent controls identify that a threat has landed in your system. True False QUESTION 2 While running
 Answer all for a thumbs up!
Answer all for a thumbs up!
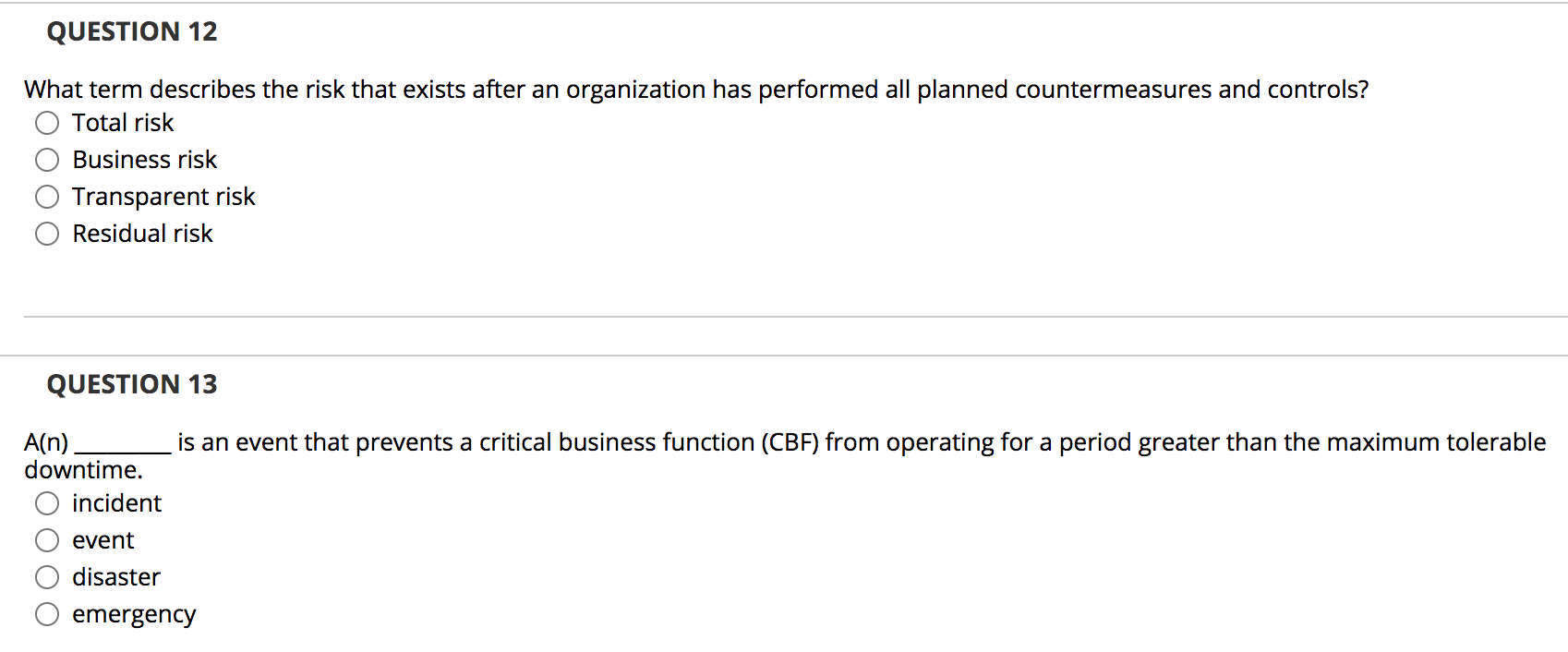
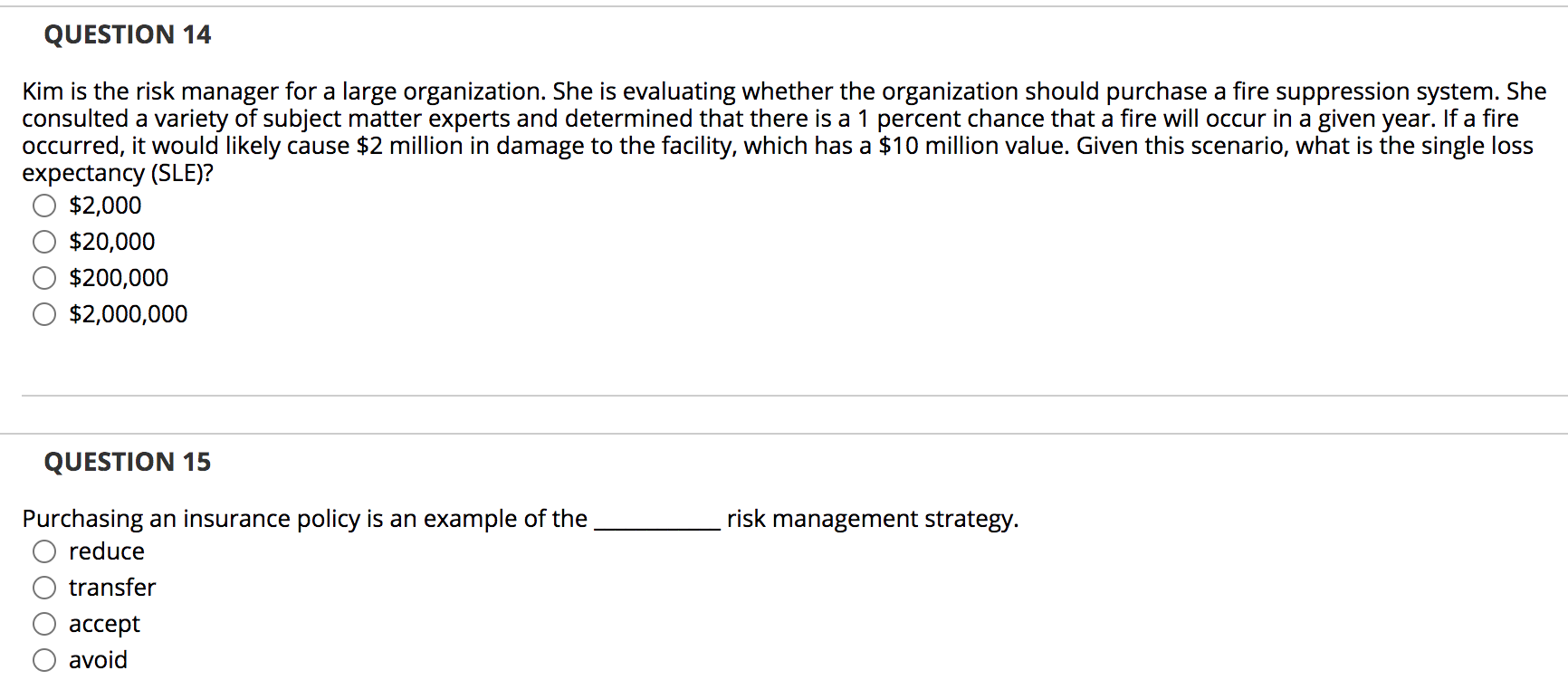
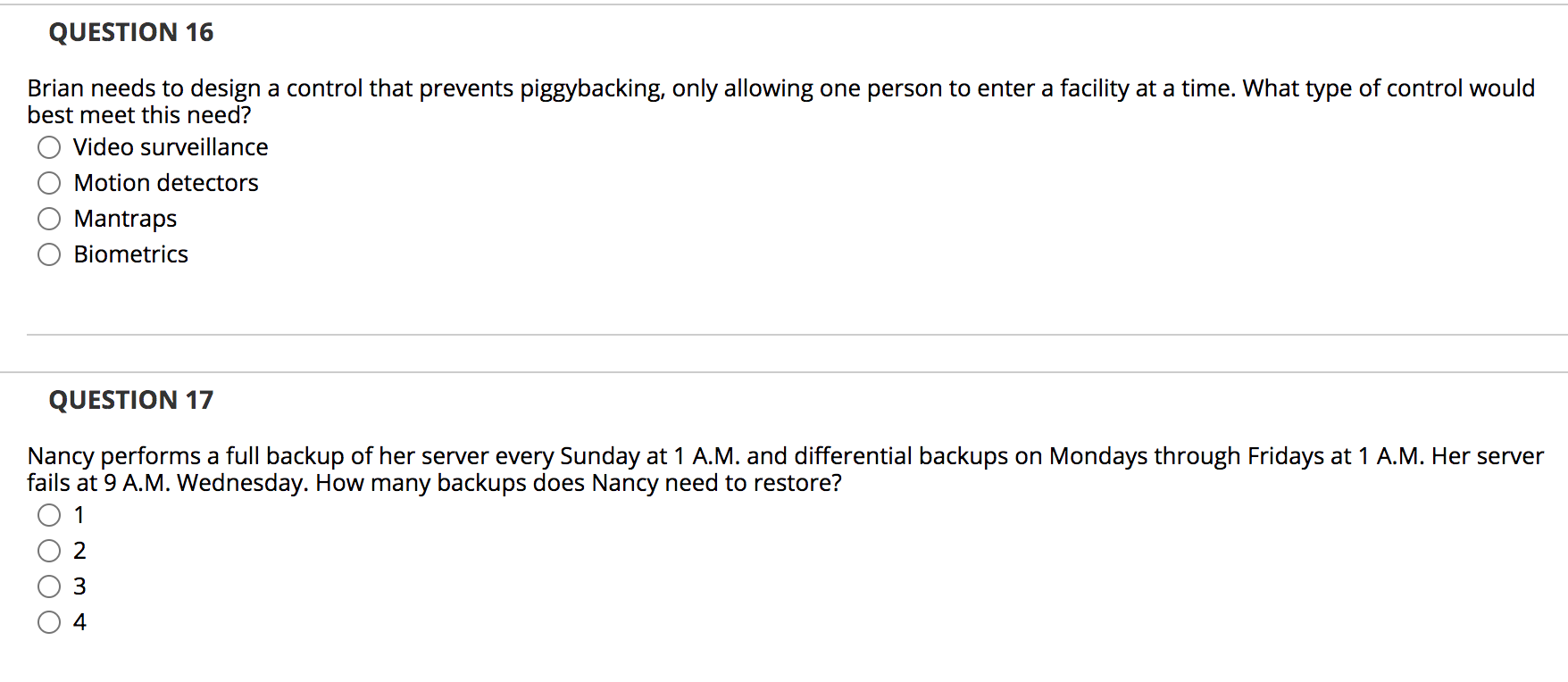
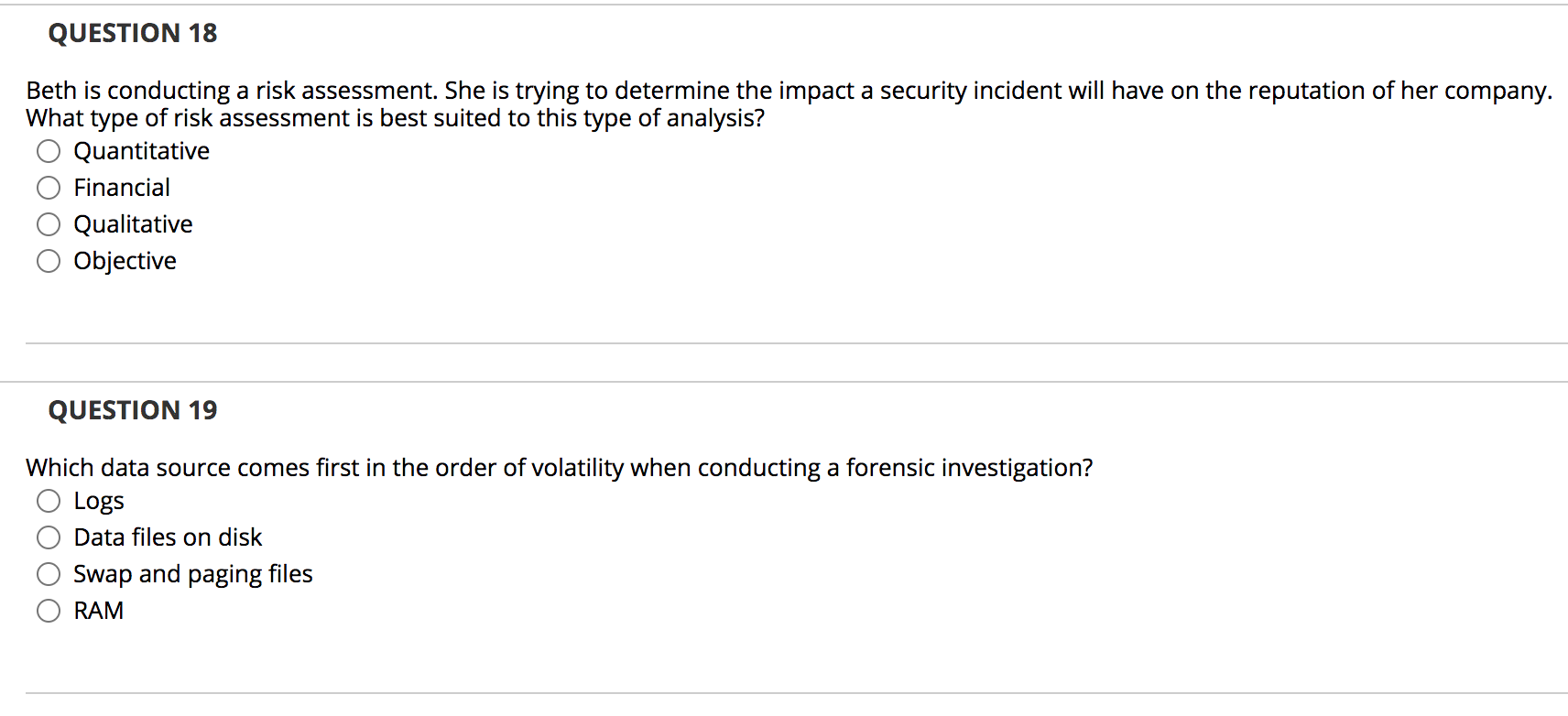
QUESTION 1 Deterrent controls identify that a threat has landed in your system. True False QUESTION 2 While running business operations at an alternate site, you must continue to make backups of data and systems. True False QUESTION 3 A business impact analysis (BIA) details the steps to recover from a disruption and restore the infrastructure necessary for normal business operations. True False QUESTION 4 A structured walk-through test is a review of a business continuity plan to ensure that contact numbers are current and that the plan reflects the company's priorities and structure. True False QUESTION 5 Organizations should seek a balance between the utility and cost of various risk True anagement options. False QUESTION 6 With adequate security controls and defenses, an organization can oftenreduce its risk to zero. True False QUESTION 7 In remote journaling, a system writes a log of online transactions to an offsite location. True False QUESTION 8 Examples of major disruptions include extreme weather, application failure, and criminal activity. True False QUESTION 9 A control limits or constrains behavior. True False QUESTION 10 Administrative controls develop and ensure compliance with policy and procedures. True False QUESTION 11 Kim is the risk manager for a large organization. She is evaluating whether the organization should purchase a fire suppression system. She consulted a variety of subject matter experts and determined that there is a 1 percent chance that a fire will occur in a given year. If a fire occurred, it would likely cause $2 million in damage to the facility, which has a $10 million value. Given this scenario, what is the annualized loss expectancy (ALE)? $2,000 $20,000 $200,000 $2,000,000 QUESTION 12 What term describes the risk that exists after an organization has performed all planned countermeasures and controls? O Total risk Business risk Transparent risk Residual risk QUESTION 13 A(n) is an event that prevents a critical business function (CBF) from operating for a period greater than the maximum tolerable downtime. O incident event disaster emergency QUESTION 14 Kim is the risk manager for a large organization. She is evaluating whether the organization should purchase a fire suppression system. She consulted a variety of subject matter experts and determined that there is a 1 percent chance that a fire will occur in a given year. If a fire occurred, it would likely cause $2 million in damage to the facility, which has a $10 million value. Given this scenario, what is the single loss expectancy (SLE)? $2,000 $20,000 $200,000 $2,000,000 QUESTION 15 risk management strategy. Purchasing an insurance policy is an example of the O reduce transfer accept avoid QUESTION 16 Brian needs to design a control that prevents piggybacking, only allowing one person to enter a facility at a time. What type of control would best meet this need? Video surveillance Motion detectors Mantraps Biometrics QUESTION 17 Nancy performs a full backup of her server every Sunday at 1 A.M. and differential backups on Mondays through Fridays at 1 A.M. Her server fails at 9 A.M. Wednesday. How many backups does Nancy need to restore? 1 2 3 4 QUESTION 18 Beth is conducting a risk assessment. She is trying to determine the impact a security incident will have on the reputation of her company. What type of risk assessment is best suited to this type of analysis? Quantitative Financial Qualitative Objective QUESTION 19 Which data source comes first in the order of volatility when conducting a forensic investigation? O Logs Data files on disk Swap and paging files RAM QUESTION 20 Alan is the security manager for a mid-sized business. The company has suffered several serious data losses when mobile devices were stolen. Alan decides to implement full disk encryption on all mobile devices. What risk response did Alan take? Reduce Transfer Accept Avoid
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


