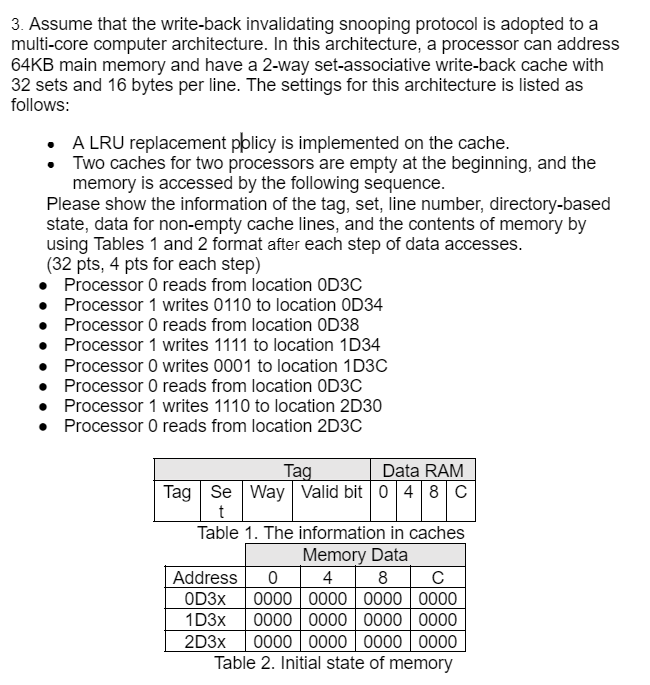
Question: Assume that the write - back invalidating snooping protocol is adopted to a multi - core computer architecture. In this architecture, a processor can address
Assume that the writeback invalidating snooping protocol is adopted to a
multicore computer architecture. In this architecture, a processor can address
main memory and have a way setassociative writeback cache with
sets and bytes per line. The settings for this architecture is listed as
follows:
A LRU replacement pplicy is implemented on the cache.
Two caches for two processors are empty at the beginning, and the
memory is accessed by the following sequence.
Please show the information of the tag, set, line number, directorybased
state, data for nonempty cache lines, and the contents of memory by
using Tables and format after each step of data accesses.
pts pts for each step
Processor reads from location ODC
Processor writes to location OD
Processor reads from location OD
Processor writes to location D
Processor writes to location DC
Processor reads from location ODC
Processor writes to location D
Processor reads from location DC
Table The information in caches
Table Initial state of memory
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


