Question: Authentication is completed when the sender Multiple Choice use the sender's public key to successfuly decrypt a message encrypted by the sender's private key
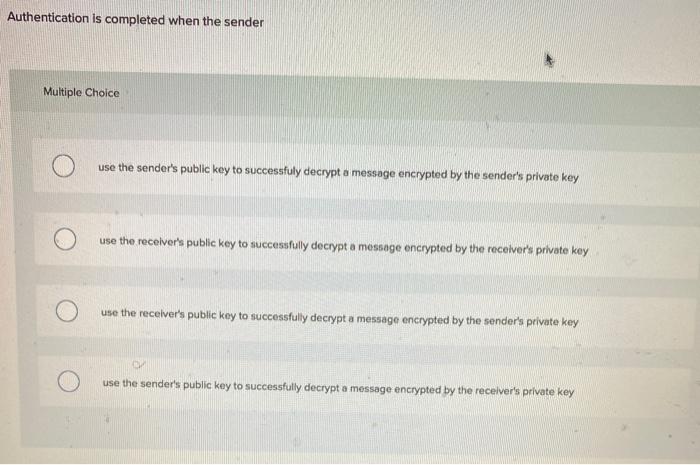
Authentication is completed when the sender Multiple Choice use the sender's public key to successfuly decrypt a message encrypted by the sender's private key use the receiver's public key to successfully decrypt a message encrypted by the receiver's private key use the receiver's public key to successfully decrypt a message encrypted by the sender's private key use the sender's public key to successfully decrypt a message encrypted by the receiver's private key
Step by Step Solution
3.62 Rating (163 Votes )
There are 3 Steps involved in it
The detailed answer for the above question is provided below The correct answer is use th... View full answer

Get step-by-step solutions from verified subject matter experts


