Question: Based on the research that I attached please I need the abstract and conclusion 1 Introduction An intrusion detection system or IDS is a device
Based on the research that I attached please I need the abstract and conclusion



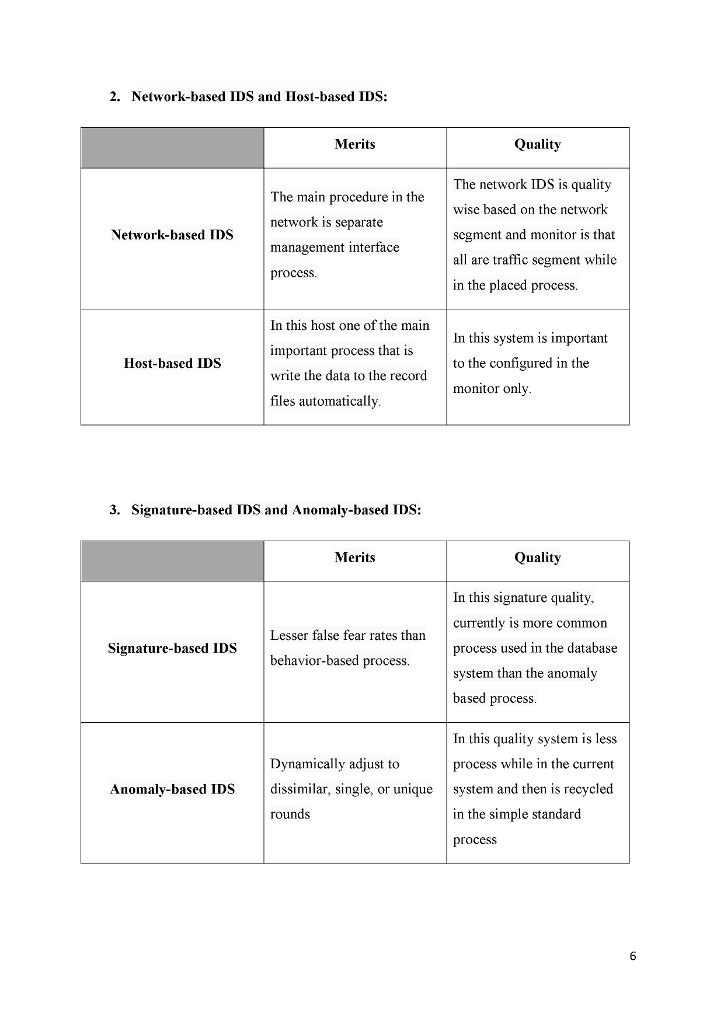
1 Introduction An intrusion detection system or IDS is a device or software which detects the unauthorized or false activities or policy violation activities in the system or in the network. Any such false or unauthorized activities are recorded and will send to the system administrator or network administrator or to the STEM system. STEM is a security information and event management which recognizes false activities and filter's the malicious alarm activities and gives true malicious alarms 2 The available systems of intrusion detection I. Passive and active of IDS Active Intrusion Detection Systems used for give or providing real, time measures in response to an attack. Active intrusion detection systems (IDS) which is known as intrusion detection and prevention system(IDPS). It used to automatically block suspected that attacks with is no need requirements of permission that from operator Where as a passive TD provides detail description of potential vulnerabilities and attacks to the system. The passive TDS system basically analyzes network traffic activity. A passive TD requires special permission from operator and is not capable of performing any protective or corrective measures on its own 2. Network Intrusion detection systems (NIDS) and Host Intrusion detection Systems(HIDS) Whereas when we talk about Network Intrusion Detection Systems (NIDS) it usually consists of a sensor with a Network Interface Card and a separate management interface. The IDS is placed along a network boundary and measures all traffic on that boundary Some software applications and Host lntrusion Detection Systems (HIDS) software are being installed on workstations which are to be monitoredregularly. Also, the concept of log files are used to monitor operating system. Basically, the use of host Intrusion detection systems S) can only on the particular system that on which agents are installed and it will cannot watch and monitor the network entire. HostBased.IDS systems are used towatch and monitor all intrusion attempts on loaded server
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


