Question: Below are two examples of code fragments, indicated by numbers 1 and 2. a) The above two pieces of code are examples of metamorphic software.
Below are two examples of code fragments, indicated by numbers 1 and 2.
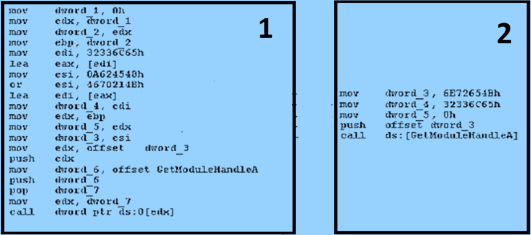
a) The above two pieces of code are examples of metamorphic software. What is metamorphic software? Explain why metamorphic software is needed.
b) From the SRE (Software Reverse Engineering) point of view, can it be interpreted as "A metamorphic piece of code may also have code obfuscation"? Discuss.
1 2 | ip mov mov anov mov lea mov Or lea word 1, ON ctx, chord 1 hor_2, edhe ebp, word 2 odi, 32336C65h eax, [edi] esi, OAG 24540h esi, 46702118h edi, [eax] thrord_1, cdi ex, ebp + 01 5, tx chord 3, csi edx, offset therord_? cx dord_6, offset CetModuleHandler dword 6 chron? ex, dword ? chord ptr ds: 0[ex] ILOV mov puch call chord_3, 6E726548h chords, 32336C65h cwords, on offset crord_3 ds: [Gel ModuleHandleA] mov mov MOV mov MOV push mov push MOV call
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


