Question: Black Box Case Study A black-box case study. You may use assumptions, but don't forget to state/elaborate your assumptions in the answer. Say there is
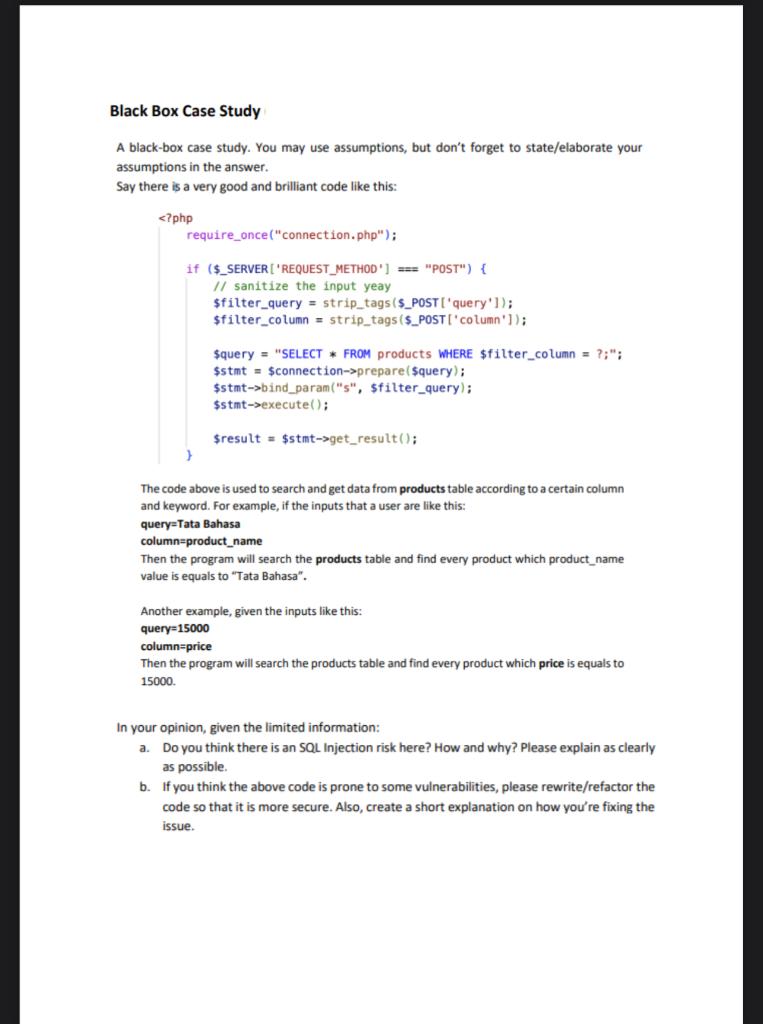
Black Box Case Study A black-box case study. You may use assumptions, but don't forget to state/elaborate your assumptions in the answer. Say there is a very good and brilliant code like this: The code above is used to search and get data from products table according to a certain column and keyword. For example, if the inputs that a user are like this: query=Tata Bahasa column=product_name Then the program will search the products table and find every product which product_name value is equals to "Tata Bahasa". Another example, given the inputs like this: query 15000 column=price Then the program will search the products table and find every product which price is equals to 15000. In your opinion, given the limited information: a. Do you think there is an SQL Injection risk here? How and why? Please explain as clearly as possible. b. If you think the above code is prone to some vulnerabilities, please rewrite/refactor the code so that it is more secure. Also, create a short explanation on how you're fixing the issue
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


