Question: BOB ALICE MD Hash Function message No Yes Same? discard You Hash Function Insecure medium MD message Study the MD scheme that is shown in
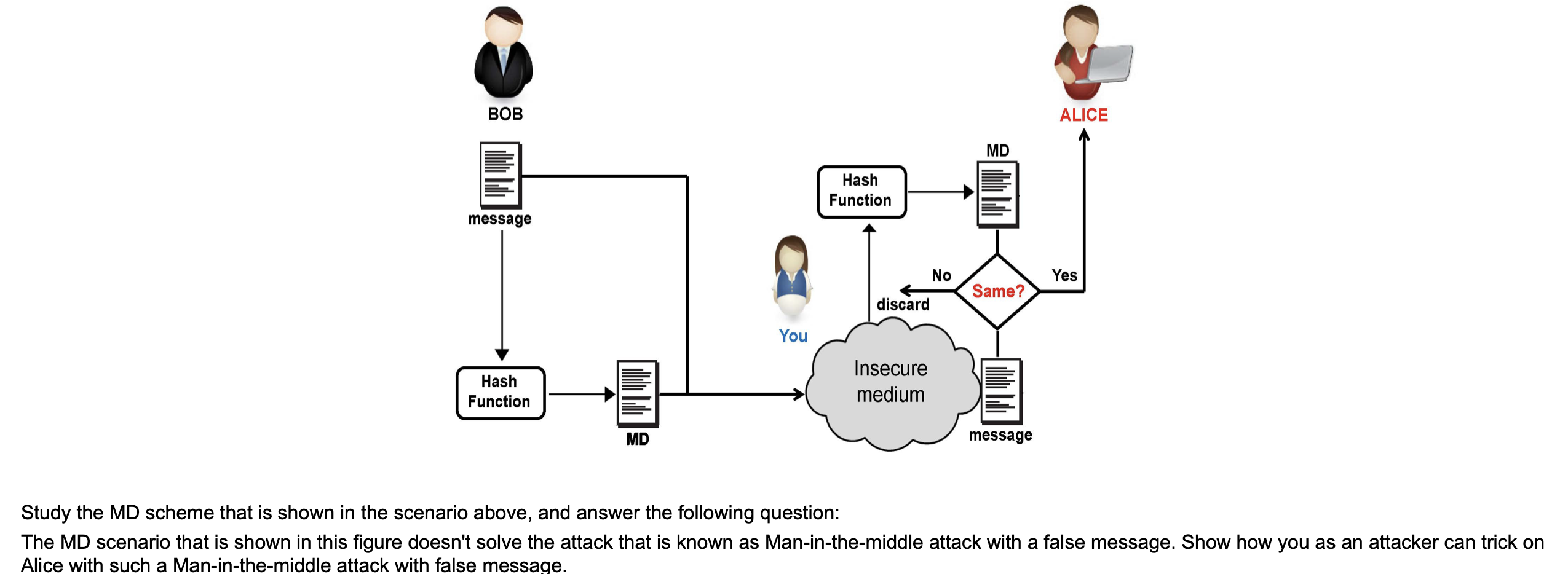
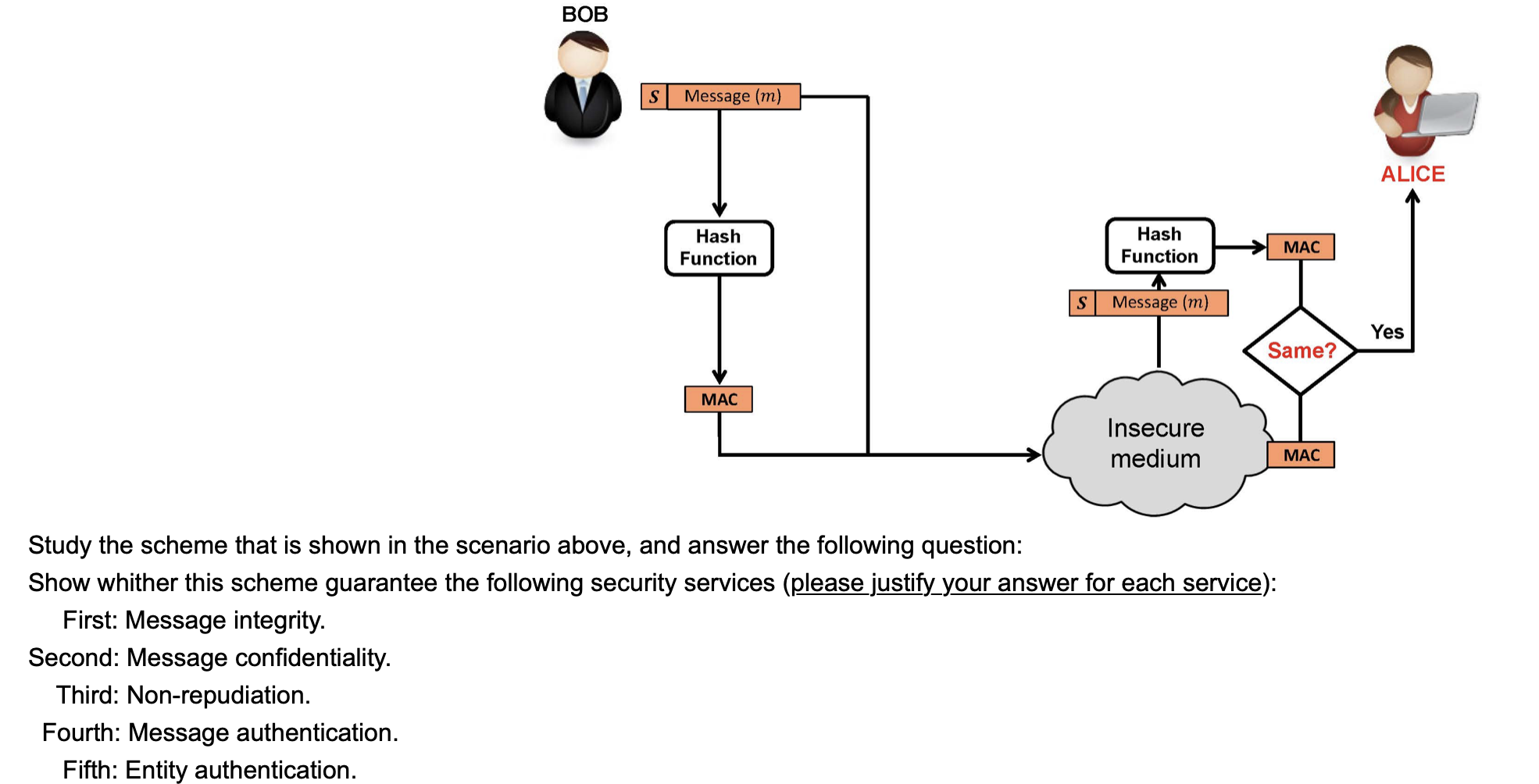
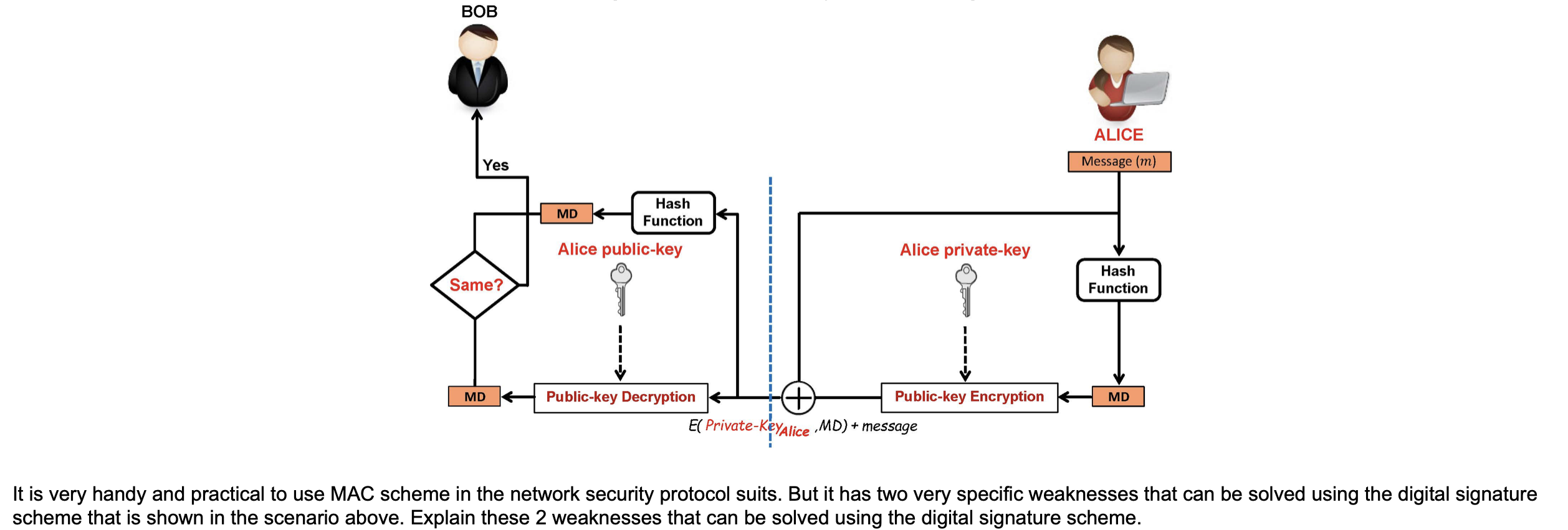
BOB ALICE MD Hash Function message No Yes Same? discard You Hash Function Insecure medium MD message Study the MD scheme that is shown in the scenario above, and answer the following question: The MD scenario that is shown in this figure doesn't solve the attack that is known as Man-in-the-middle attack with a false message. Show how you as an attacker can trick on Alice with such a Man-in-the-middle attack with false message. a BOB S Message (m) ALICE Hash Function Hash Function MAC S Message (m) Yes Same? MAC Insecure medium MAC Study the scheme that is shown in the scenario above, and answer the following question: Show whither this scheme guarantee the following security services (please justify_your answer for each service): First: Message integrity. Second: Message confidentiality. Third: Non-repudiation. Fourth: Message authentication. Fifth: Entity authentication. BOB ALICE Yes Message (m) MD Hash Function Alice public-key Alice private-key Same? Hash Function MD MD Public-key Decryption Public-key Encryption El Private-keyAlice ,MD) + message It is very handy and practical to use MAC scheme in the network security protocol suits. But it has two very specific weaknesses that can be solved using the digital signature scheme that is shown in the scenario above. Explain these 2 weaknesses that can be solved using the digital signature scheme
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


