Question: c. Consider the function foobar depicted below. Let us assume its input x is represented by a symbolic value and that foobar is explored using
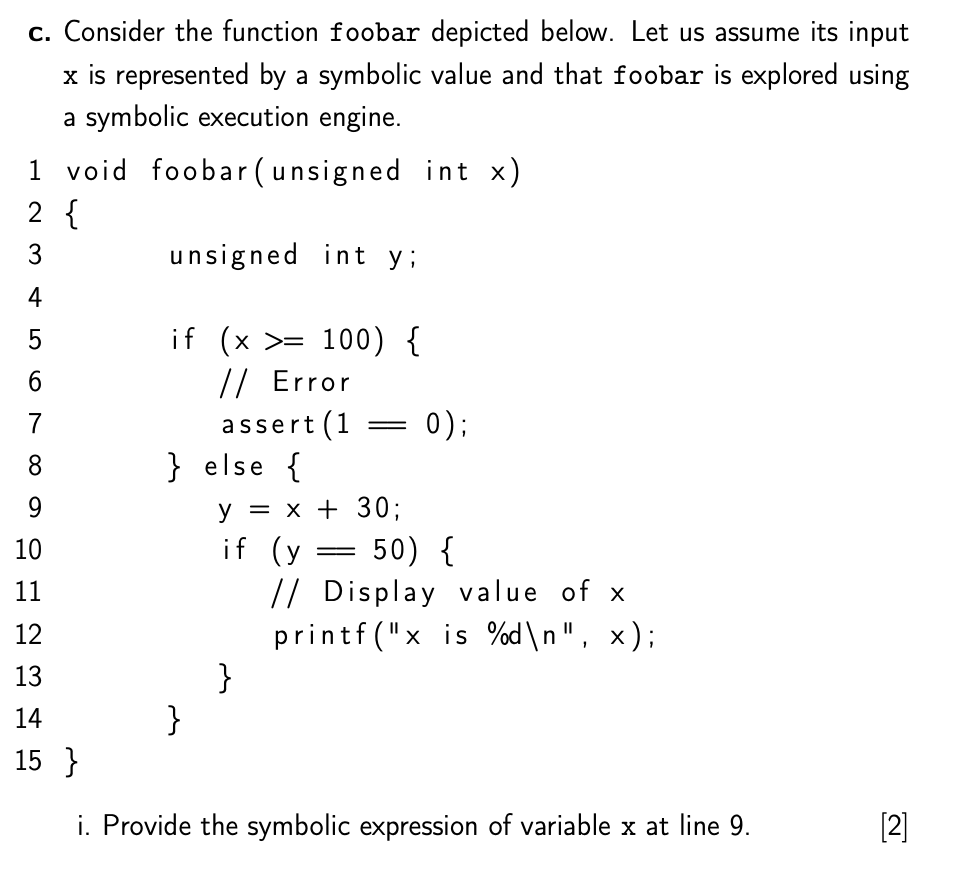

c. Consider the function foobar depicted below. Let us assume its input x is represented by a symbolic value and that foobar is explored using a symbolic execution engine. 1 void foobar (unsigned int x) 2 { 3 unsigned int y; 4 5 if (x >= 100) { 6 // Error 7 assert (1 0); } else { 9 y = x + 30; 10 50) { 11 // Display value of x 12 printf("x is %d ", x); 13 } 14 } 15 } 8 if (y 9 i. Provide the symbolic expression of variable x at line 9. [2] ii. Provide the full path condition at line 11. [2] iii. Provide the list of line numbers which cause state forking. [2] iv. A SAT/SMT solver is queried to produce a concrete input for reach- ing line 11. Give the correct solution. [2] d. Vulnerabilities, exploitation, and mitigation techniques. i. Explain what exploitation technique(s) DEP (or NX) prevents. ii. Explain why taint analysis is useful in exploit generation. [1] [2] iii. Explain what heap spraying is and which exploit mitigation it tries to circumvent. [2] iv. Explain what a write-4 exploit primitive is and how it can be used to a execute code. [2] v. Explain what a use-after-free vulnerability is and how attackers can take advantage of it. [] [2]
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


