Question: Can someone provide a written explanation using the image provided please? Specifically, define guidance on where and how to modify the existing DevOps process to
Can someone provide a written explanation using the image provided please? Specifically, define guidance on where and how to modify the existing DevOps process to automate enforcement of the standards in this policy. Use the DevSecOps diagram and provide an explanation using that diagram as context.
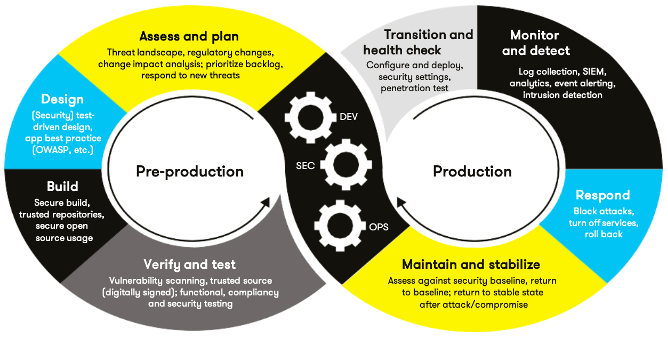
Assess and plan Transition and Monitor Threat landscape, regulatory changes, health check and detect change impact analysis: prioritize backlog. Configure and deploy. respond to new threats security settings, Log collection, SIEM, penetration test analytics, event alerting, Design Intrusion detection (Security] test- DEV driven design, app best practice [OWASP, etc.) Pre-production SEC Production Build Respond Secure build, trusted repositories, Block attacks, secure open OPS turn off services, source usage roll back Verify and test Maintain and stabilize Vulnerability scanning, trusted source Assess against security baseline, return [digitally signed); functional, compliance to baseline; return to stable state and security testing after attack/compromise
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


