Question: choice correct answer only Which one below cannot be an element of an extended access list? Question 1 Not yet answered Marked out of 1.00


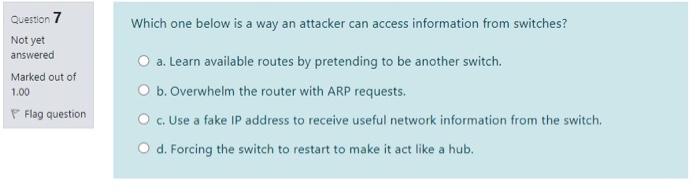
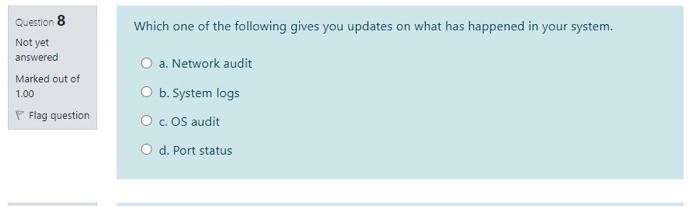
Which one below cannot be an element of an extended access list? Question 1 Not yet answered Marked out of 1.00 Remove flag O a. Socket number O b. Source host address c. Protocol O d. Destination network address Which methodology of network Security assessment scans open ports to determine accessible hosts and network services? Question 2 Not yet answered Marked out of 1.00 Remove flag a. Network probing b. Exploitation of vulnerabilities c. Reconnaissance O d. Investigation of vulnerabilities Question 7 Not yet answered Marked out of 1.00 Flag question Which one below is a way an attacker can access information from switches? a. Learn available routes by pretending to be another switch. O b. Overwhelm the router with ARP requests. Use a fake IP address to receive useful network information from the switch. O d. Forcing the switch to restart to make it act like a hub. Which one of the following gives you updates on what has happened in your system. Question 8 Not yet answered Marked out of 1.00 O a. Network audit O b. System logs OcOS audit Flag question O d. Port status
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


