Question: CISC 3310 MWO 37. In order to avoid bubbles, Fig. 3 shows a pipeline passing data from an add instruction in the EX stage to
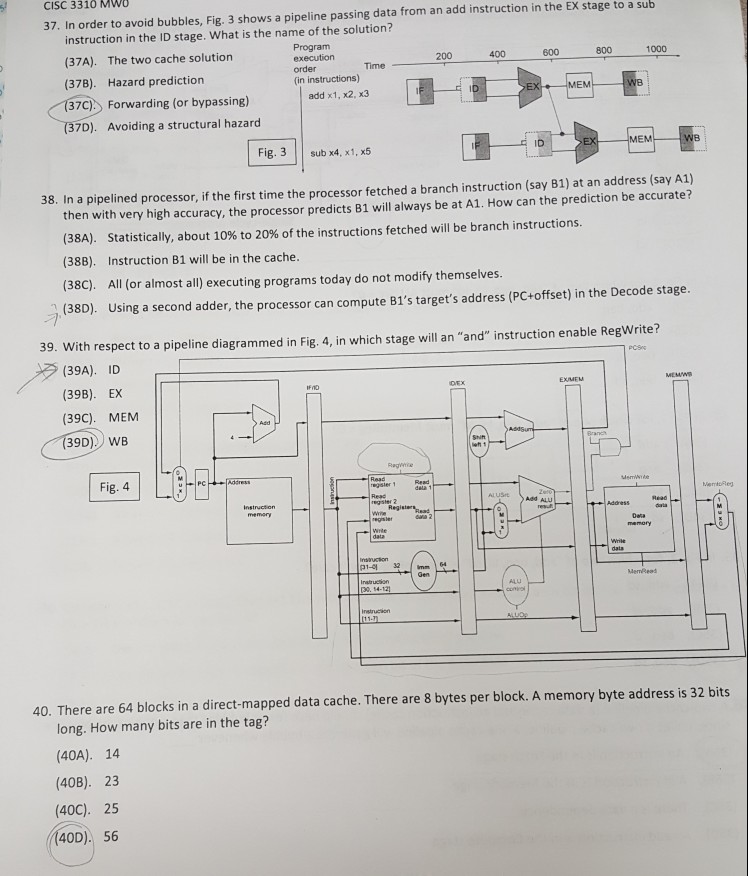
CISC 3310 MWO 37. In order to avoid bubbles, Fig. 3 shows a pipeline passing data from an add instruction in the EX stage to a sub instruction in the ID stage. What is the name of the solution? (37A). The two cache solution (37B). Hazard prediction 37C) Forwarding (or bypassing) Program executionTime order (in instructions) 200 400 600 800 1000 EM add x1, x2, x3 7D). Avoiding a structural hazard Fig. 3 ub x4, x1, x5 ID EM 38. In a pipelined processor, if the first time the processor fetched a branch instruction (say 81) at an address (say A1) then with very high accuracy, the processor predicts B1 will always be at A1. How can the prediction be accurate? (384). Statistically, about 10% to 20% of the instructions fetched will be branch instructions (38B). Instruction B1 will be in the cache. (38C) All (or almost all) executing programs today do not modify themselves (38D). Using a second adder, the processor can compute B1's target's address (PC+offset) in the Decode stage. 39. With respect to a pipeline diagrammed in Fig. 4, in which stage will an "and" instruction enable RegWrite? (39A). ID (39B). EX (39C). MEM (39D)WB Fig. 4 (30. 14- 40. There are 64 blocks in a direct-mapped data cache. There are 8 bytes per block. A memory byte address is 32 bits long. How many bits are in the tag? (40A). 14 (40B). 23 (40C). 25 40D). 56
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


