Question: Comment out the system(command) statement, and uncomment the execve ( ) statement; the program will use execve () to invoke the command. Recompile the program.
Comment out the system(command) statement, and uncomment the execve() statement; the program will use execve() to invoke the command. Recompile the program. Make it a root-owned Set-UID again. Does your attack from Step 1 still work?
Question: Please describe and explain the behaviour change?

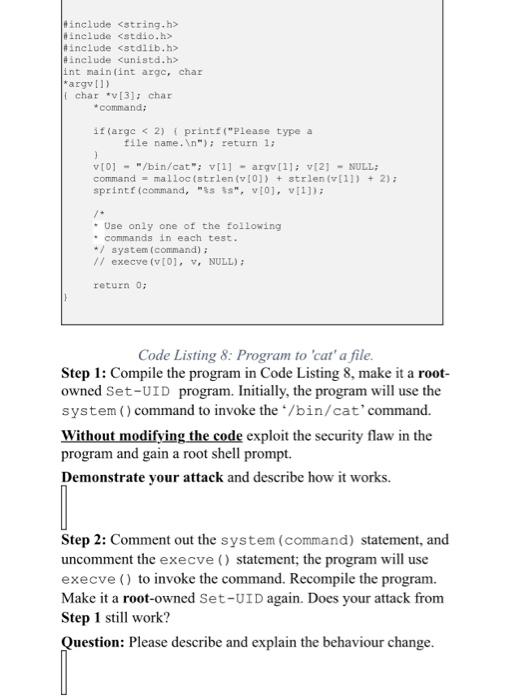
Step 2: Comment out the system (command) statement, and uncomment the execve () statement; the program will use execve() to invoke the command. Recompile the program. Make it a root-owned Set-UID again. Does your attack from Step 1 still work? Question: Please describe and explain the behaviour change. #include
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


