Question: Complete the following table, indicating which ITGC process (manage change process, manage access process or manage IT operations process) will address the stated risk, using
Complete the following table, indicating which ITGC process (manage change process, manage access process or manage IT operations process) will address the stated risk, using the example underlying cause provided.
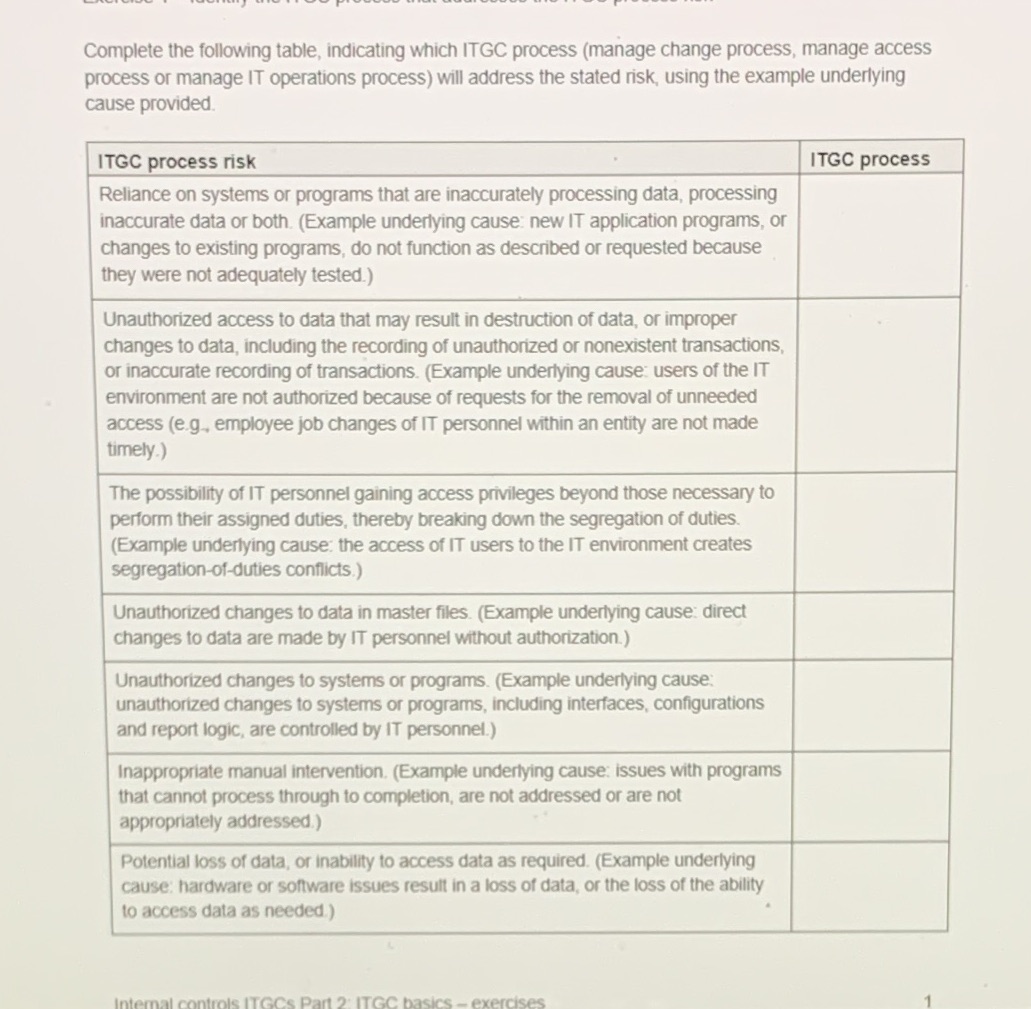
Complete the following table, indicating which ITGC process (manage change process, manage access process or manage IT operations process) will address the stated risk, using the example underlying cause provided. ITGC process risk ITGC process Reliance on systems or programs that are inaccurately processing data, processing inaccurate data or both. (Example underlying cause: new IT application programs, or changes to existing programs, do not function as described or requested because they were not adequately tested.) Unauthorized access to data that may result in destruction of data, or improper changes to data, including the recording of unauthorized or nonexistent transactions, or inaccurate recording of transactions. (Example underlying cause: users of the IT environment are not authorized because of requests for the removal of unneeded access (e.g., employee job changes of IT personnel within an entity are not made timely.) The possibility of IT personnel gaining access privileges beyond those necessary to perform their assigned duties, thereby breaking down the segregation of duties. (Example underlying cause: the access of IT users to the IT environment creates segregation-of-duties conflicts.) Unauthorized changes to data in master files. (Example underlying cause: direct changes to data are made by IT personnel without authorization.) Unauthorized changes to systems or programs. (Example underlying cause: unauthorized changes to systems or programs, including interfaces, configurations and report logic, are controlled by IT personnel.) Inappropriate manual intervention. (Example underlying cause: issues with programs that cannot process through to completion, are not addressed or are not appropriately addressed.) Potential loss of data, or inability to access data as required. (Example underlying cause: hardware or software issues result in a loss of data, or the loss of the ability to access data as needed.)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


