Question: Computer Science. cryptology Please answer each and label each answer by alphabet A. Explain precisely how and where Alice is authenticated. What prevents a replay
Computer Science. cryptology
Please answer each and label each answer by alphabet
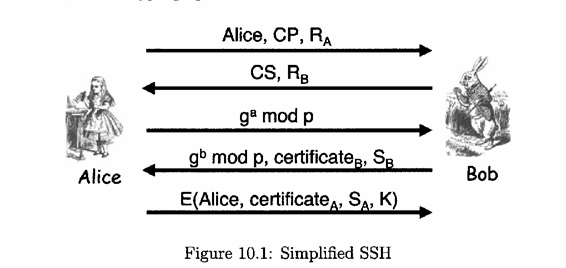
A. Explain precisely how and where Alice is authenticated. What prevents a replay attack?
B. If Trudy is a passive attacker (i.e., she can only observe messages), she cannot determine the key K. Why?
C.Show that if Trudy is an active attacker (i.e., she can actively send messages) and she can impersonate Bob, then she can determine the key K that Alice uses in the last message. Explain why this does not break the protocol.
d. What is the purpose of the encrypting the final message with the key K?
Alice Alice, CP, RA CS, RB ga mod p gb mod p. certificate Sp E(Alice, certificateA, SA, K) Figure 10.1: Simplified SSH Bob
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


