Question: Computer Science/ Cryptology Please Label Each Answers Alphabeticaly A. Explain precisely how and where Alice is authenticated. What prevents a replay attack? B. If Trudy
Computer Science/ Cryptology
Please Label Each Answers Alphabeticaly
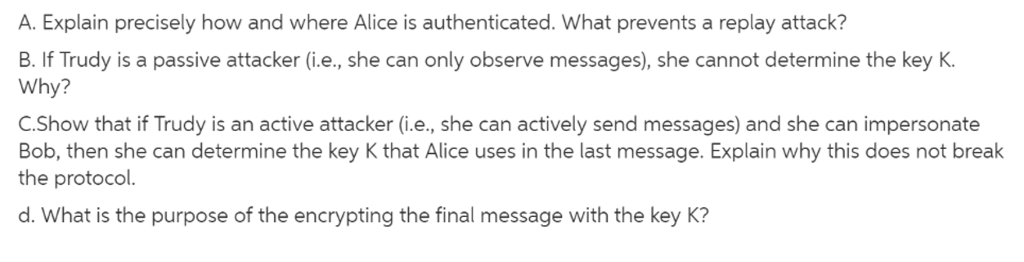
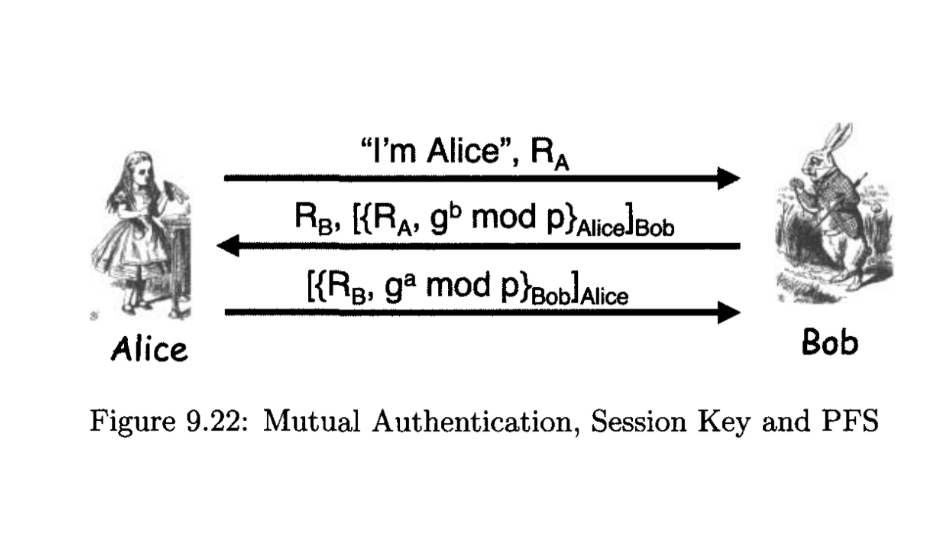
A. Explain precisely how and where Alice is authenticated. What prevents a replay attack? B. If Trudy is a passive attacker (i.e., she can only observe messages), she cannot determine the key K Why? C.Show that if Trudy is an active attacker (i.e., she can actively send messages and she can impersonate Bob, then she can determine the key K that Alice uses in the last message. Explain why this does not break the protocol. d. What is the purpose of the encrypting the final message with the key K
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


