Question: (COMPUTER SCIENCE QUESTION)(CYBERSECURITY) (I JUST NEED THE INFORMATION FLOW DIAGRAM IN A FORMAT I CAN COPY AND PASTE IN MY REPORT ) Information Flow Diagram
(COMPUTER SCIENCE QUESTION)(CYBERSECURITY) (I JUST NEED THE INFORMATION FLOW DIAGRAM IN A FORMAT I CAN COPY AND PASTE IN MY REPORT )
Information Flow Diagram
[Provide connectivity diagram or system input and output flowchart to delineate the scope of this risk assessment effort].
DETAILS OF RISK ASSESMENT( I just need the information flow diagram )
You have been hired as an IT administrator to implement, manage, and administer a new IT project This company has been growing and they are now creating an online presence in order to bring their store online, as well as to replace and modernize their paper-based accounting and inventory management system to a digital automated system. The Boss has been meeting with the vendor representatives and has received proposals and quotes for solutions The Vendor provides a software platform that promises to provide for every need, including public website, sales and ecommerce, as well as accounting and inventory management. The Vendor has also provided consultation services on implementation of their software, however customer is ultimately responsible for the hardware and infrastructure
Business objectives
Jack of All Trades Merchant CMS software platform is to provide: CMS based customer facing public internet website www..com Active Online store (store..com) Order processing Automation Payment processing Automation Inventory and product tracking Automation Accounting and Inventory solution Combines the accounting and inventory from the online store with the existing warehouse and sales operations Provides the warehouse with tools for Online and offline Inventory management and tracking, and sales order fulfilment Provides sales department with tools to process and place orders, and keep track of customer sales and data, as well as margins and commissions Provides accounting department with detailed reports of inventory, sales revenue, and provides tools for financial management related to the products and goods
Additional Proposed Requirements for AWS
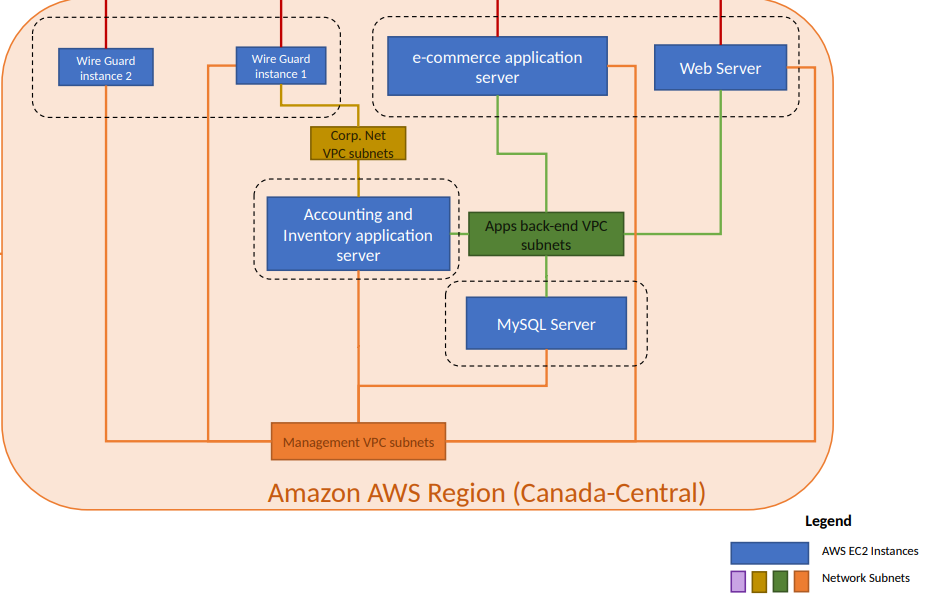 AWS Control Panel (AWS IAM account) only accessible by IT Admin and via 2FA (AWS Root Account to be locked away) Wireguard servers with strong encryption keys for VPN connection to the cloud infrastructure All internal users required to access the internal application server are issues a personal Wireguard profile and encryption key Wireguard access is logged Only IT Admin has Wireguard (VPN) access to management VPC Subnet. A separate AWS EC2 instance is provisioned for this (Wiregaurd Instance 2). Management VPC Subnet AWS Security Group setting applied to subnet to only allow SSH traffic from local subnet, and all other types of traffic are blocked (no internet traffic) Internet traffic may be forwarded in order to install updates and upgrades on back-end servers, but all incoming ports are denied from public internet (including SSH). Application Back-end VPC Subnet Only MySQL traffic is allowed from local subnet. All other traffic is blocked. Corporate Net VPC Subnet Accounting and Inventory application server is accessible via Wireguard to corporate users. Required TCP/UDP ports for the application are allowed over the local subnet only. All incoming from 0.0.0.0/0 are blocked. Security Groups for Internet facing servers Internet Security Group 1 is for webservers: HTTPS traffic from 0.0.0.0/0 is allowed. All other incoming traffic is blocked. Internet Security Group 2 is for Wireguard servers: Wireguard TCP/UDP incoming traffic is allowed from 0.0.0.0/0. All other incoming traffic is blocked
AWS Control Panel (AWS IAM account) only accessible by IT Admin and via 2FA (AWS Root Account to be locked away) Wireguard servers with strong encryption keys for VPN connection to the cloud infrastructure All internal users required to access the internal application server are issues a personal Wireguard profile and encryption key Wireguard access is logged Only IT Admin has Wireguard (VPN) access to management VPC Subnet. A separate AWS EC2 instance is provisioned for this (Wiregaurd Instance 2). Management VPC Subnet AWS Security Group setting applied to subnet to only allow SSH traffic from local subnet, and all other types of traffic are blocked (no internet traffic) Internet traffic may be forwarded in order to install updates and upgrades on back-end servers, but all incoming ports are denied from public internet (including SSH). Application Back-end VPC Subnet Only MySQL traffic is allowed from local subnet. All other traffic is blocked. Corporate Net VPC Subnet Accounting and Inventory application server is accessible via Wireguard to corporate users. Required TCP/UDP ports for the application are allowed over the local subnet only. All incoming from 0.0.0.0/0 are blocked. Security Groups for Internet facing servers Internet Security Group 1 is for webservers: HTTPS traffic from 0.0.0.0/0 is allowed. All other incoming traffic is blocked. Internet Security Group 2 is for Wireguard servers: Wireguard TCP/UDP incoming traffic is allowed from 0.0.0.0/0. All other incoming traffic is blocked
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


