Question: Determine the shellcode needed to implement a return to system call attack that calls system(whoami; cat /etc/shadow; exit;), targeting the same vulnerable program as used
Determine the shellcode needed to implement a return to system call attack that calls system(whoami; cat /etc/shadow; exit;), targeting the same vulnerable program as used in Problem 10.6. You need to identify the location of the standard library system() function on the target system by tracing a suitable test program with a debugger. You then need to determine the correct sequence of address and data values to use in the attack string. Experiment with running this attack.
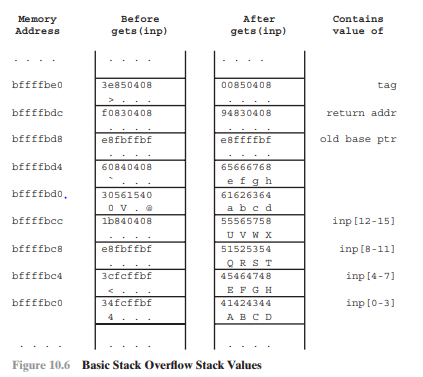
MemorY Address Before gets (inp) After gets (inp) Contains value of bffffbe0 3e850408 00850408 tag bffffbdc 0830408 94830408 return addr bffffbd8 e8fbffbf e8ffffbf old base ptr bffffbd4 60840408 65666768 e fg h 61626364 a bc d 55565758 bffffbdo 0561540 bffffbcc bffffbcB bffffbc4 bffffbco 1b840408 inp [12-15] inp[8-11] inp [4-71 inp I0-3] e8fbffbf 1525354 R S T 5464748 E F GH 1424344 A B CD 3cfcffbf 34fcffbf Figure 10.6 Basic Stack Overflow Stack Values
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


