Question: Consider a PUF that accepts 3 - bit challenges and generates 8 - bit responses. Alice will use PUF as an access authentication device. Steve,
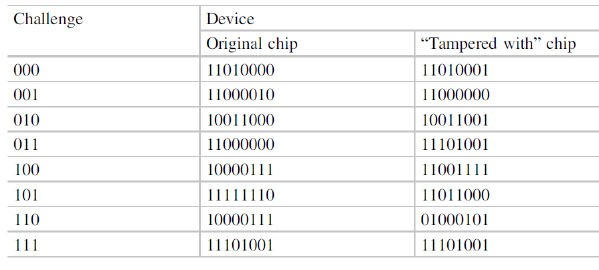
Consider a PUF that accepts bit challenges and generates bit responses. Alice will use PUF as an access authentication device. Steve, a known adversary of Alice, managed to gain access to the PUF and maliciously changed its circuit, inserting a small passive element, which acts as an antenna, which led to some changes in the behavior of the original PUF, as described in the table below Analyze the data provided in this table and consider whether Alice's PUF can be considered resistant to Steve's tampering attack.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


