Question: Consider a secure connection protocol presented in the figure below. The figure presenting two hosts communicating with each other using a randomly generated secret key
Consider a secure connection protocol presented in the figure below. The figure presenting two hosts communicating with each other using a randomly generated secret key (S).
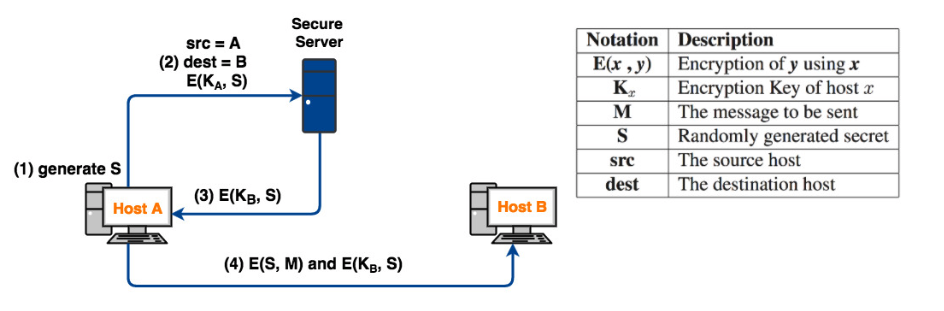
A. Assume host A wants to send a message (M) to host B. Describe the protocol presented in the figure.
B. Discuss how would a man-in-the-middle discover the randomly generated secret (S) of host A.
Secure Server Notation Description Elr,,y) Encryption of y using r src A (2) dest- B E(KA, S) K.Encryption Key of host r The message to be sent S Randomly generated secret src The source host dest The destination host (1) generate S (3) E(G, s) Host A Host B (4) E(S, M) and E(KB, S)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


