Question: Consider the following C code: void greet {char *arg) { char buffer [16]: printf(I am the Senate. What is your name? ): scanf(%s, buffer): printf(It's
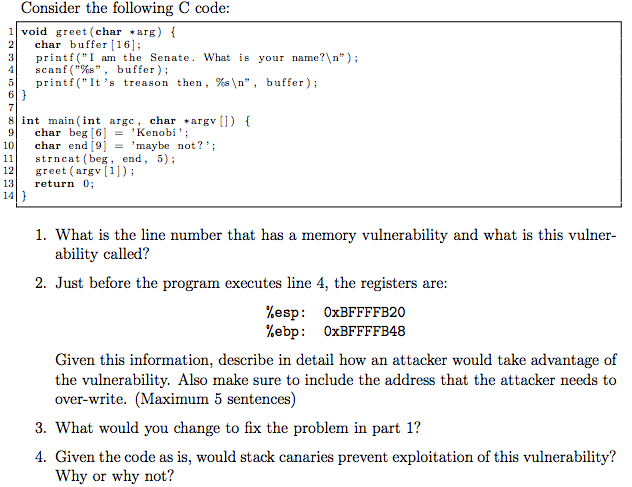
Consider the following C code: void greet {char *arg) { char buffer [16]: printf("I am the Senate. What is your name? "): scanf("%s", buffer): printf("It's treason then, %s ", buffer): } int main(int arge char *argv[]) { char beg [6] = 'Kenobi': char end [9] = 'maybe not?': strncat(beg, end, 5): greet(argv[1]): return 0: } What is the line number that has a memory vulnerability and what is this vulnerability called? Just before the program executes line 4, the registers are: %esp: 0xBFFFFB20 %ebp: 0xBFFFFB48 Given this information, describe in detail how an attacker would take advantage of the vulnerability. Also make sure to include the address that the attacker needs to over-write. (Maximum 5 sentences) What would you change to fix the problem in part 1? Given the code as is, would stack canaries prevent exploitation of this vulnerability? Why or why not
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


