Question: please answer 4,5&6 as they are interconnected to task 1&2 . the first page is instructions and then task 2 . at the end i
please answer 4,5&6 as they are interconnected to task 1&2 . the first page is instructions and then task 2 . at the end i have uploaded task 1 .
dont know the answer?
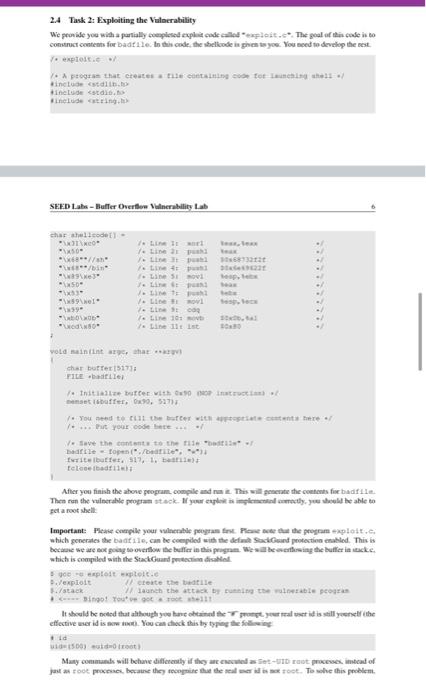
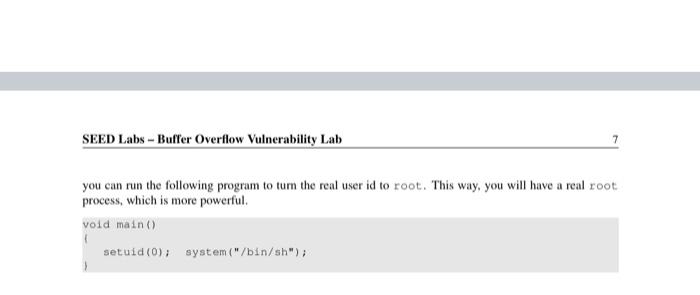
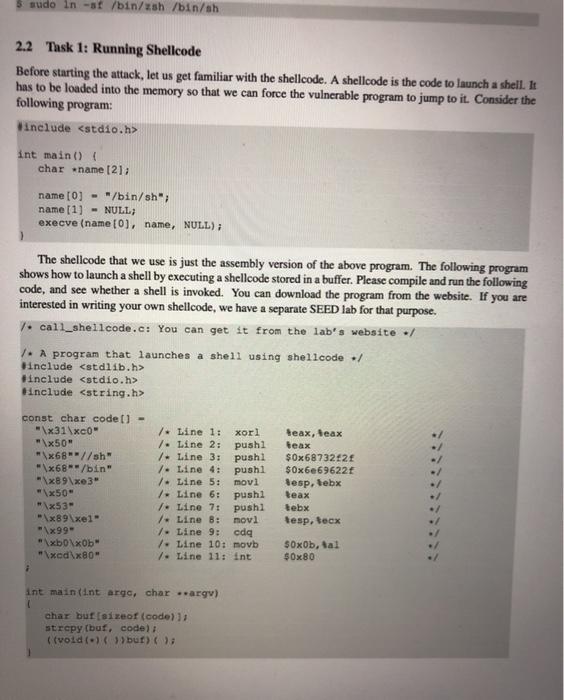
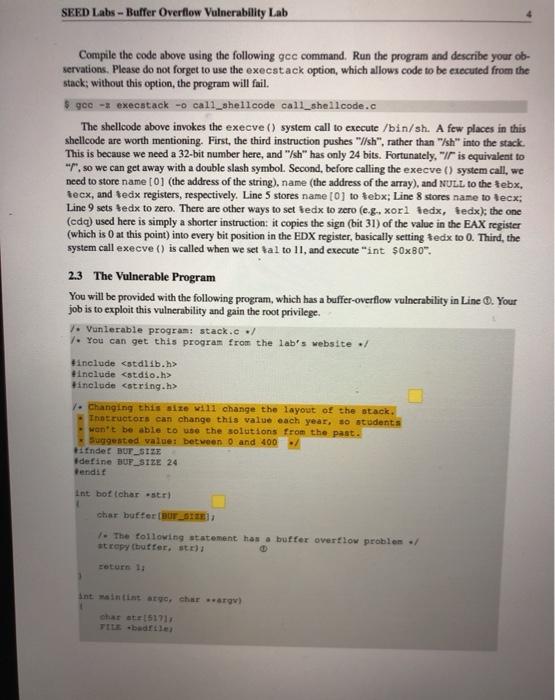
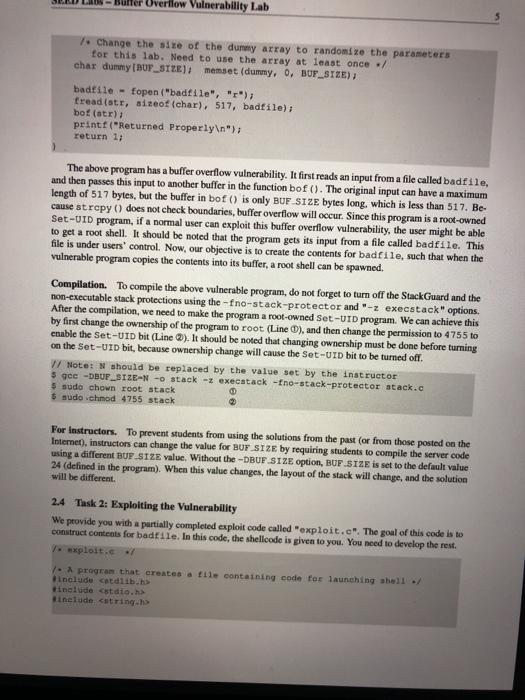
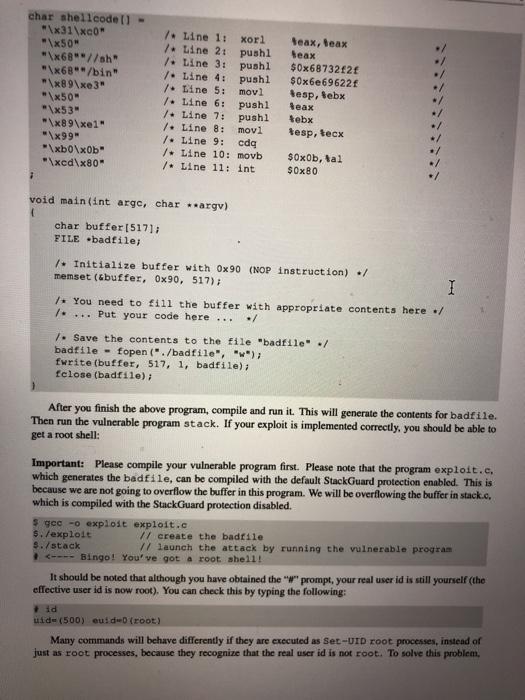
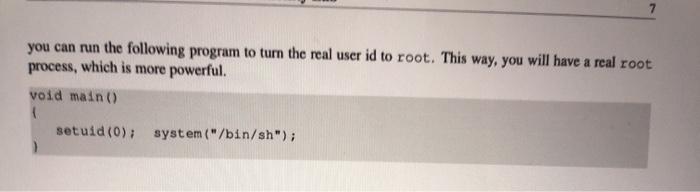
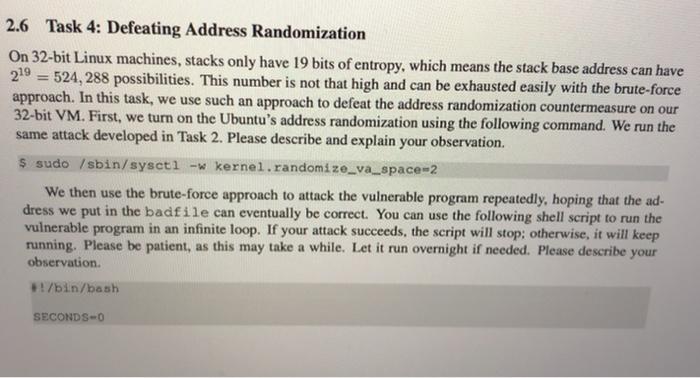
SEED Lako - Buffer Overflow Vulnerability Lab 2 Lab Tasks 2.1 Turning of Countermeasures You can execute the lab tusks using our pre-built Ubuntu virtual machines. Ubantu and other Linux distributions have implemento several security mechanisms to make the ballet-overflow attack difficult. To simplify our attacks, we need to disable the first Later on, we will enable them one by one, and see whether curattack cat still be well Address Space Randomiration Ubuntu and several other Lines based systems unes altres paceman domization to and the starting ass of leap and stack. This makes messing the exact adreses difficult, pewing addresses is one of the critical steps of buffererverlow attacks. lathislah, we disable this festure using the following command nado xactl - tel.randomize_wa_ The StackGuard Protection Scheme. The GCC compiler implements a security mechanism called Stack Gward to present offer owestions. In the presence of this protection, buffer overflownacks will not work We can disable this protection during the compilation using the stark peter option. For example to compile a prerum example with StackGuard disabled, we can do the following hack protector example Non-Executable Stack. Ubuntu used to allow executable stacks, but that has now changed the binary images of programs and shared libraries) must declare whether they require executable stacks or ne they need to maka beld in the program beader. Kemelor dynamic linker uses this marking to decide whether to make the stack of this running program executable or non-executable. This marking is done automatically by the recent version of goo, and by default,stacks are set to be on crocutable to change that use the following option when compiling programe For executable stack: goc + tak test test. Por non-executable stack Configuring /bin/sh Ubuntu 16.04 VM only). In both 12.04 and hustu 16.04 VMs, the /bin/sh symbolic link points to the /bin/dash shell. However, the dash program in these two VM have an important difference. The dash shell to huntu 16.04 has a countermasure that presents itself from being executed in a Set-UID process. Basically, if dash detects that it is executed in Set-U10 process, it immediately changes the effective user to the process's reale, essentially dropping the privilege. The dash program in Ubuntu 12.01 does not have this behavice Since our victim program is a Set-UID program, and our attack relies on running /bin/sh the countermeasure in /bin/dash makes out attack more difficult. Therefore, we will link /bin/sh to another shell that does not have such a countermeasure in later tanks, we will how that with a litle bit more effort the countercure in /bin/dash can be easily defeated. We he installed a shell program SEED Labs - Buffer Overflow Vulnerability Lab called ash in our Ubuntu 16.04 VM. We use the following commands to link /binish to sh there is no need to do these in Ubuntu 12.04 do/ bashan/h. 2.4 Task 2: Exploiting the Vulnerability We provide you with a partially complesed explicadele exploit.c. The goal of this code into Construct contents for battle. In this code, the shelkode in greats you. You need to develop the rest Yo explore progrse that creates a tu citaining soon tot launching the include 7. Change this will the twyout of the stack Thatractors can change this Malowac year students wants tenete the solutions from the past Suggested to even and 400 / det WESTE eine SE 24 endir Et toch char buffer V. The following statement berlok pole / strcpyhurrent Tecum at man inte har man char SESTI SEED Labs - Buffer Overflow Vulnerability Lah Io Change the they stay to and the parameters for this lab. Need to use the stay at least once / Hadfil - fopen("adrile", **) fraditiotica). 517, badita Dort print("Heurend Properlyle"> return; The above program basa buller over en vulnerability. It is reads an input from a tile called badle and then pause this input to another buffer in the functie born. The original input can have a maximum longth of 517 bytes, but the buffer in bot is only BU SIZE bytes ong. which is less than 517 He camentrepy () does not check boundaries, taller overflow will occur. Since this program hamowned Set-U10 program, if a normal user can exploit this buffer overflow vulnerability, the might be able to get a root shell. It should be noted that the program pets its input from a file called bad 12. This ile is under control Now, cur objective is to create the contents for bad le sach that when the vulnerable program copies the contents into in buffet, a root shell can be speed Compilation. To compile the above valorable program, do not forget to tum off the Stackard and the Boxecutable stack protections in the-ne-stack protector and execstack optical After the compilation, we need to make the programa pool-owned Set-Ut program. We can achieve this by first change the ownership of the program to root Line and then change the permission to 4755 to enable the Set-UID Line). It should be noted that changing ownership must be done before turning on the set-on because ownership change will cause the set-utbit to be tumed off Wer hold be replaced by the value by the instructor 5.900-DBOR - Stack Otack-toe-stack-protector stack.o do chan tot week docho 475 stack $ sudo in-af /bin/sh /bin/sh 2.2 Task 1: Running Shellcode Before starting the attack, let us get familiar with the shellcode. A shellcode is the code to launch a shell. It has to be loaded into the memory so that we can force the vulnerable program to jump to it. Consider the following program: Winelude int main() char name [21; name[0] - "/bin/sh"; name (1) - NULL; execve (name[0], name, NULL); The shellcode that we use is just the assembly version of the above program. The following program shows how to launch a shell by executing a shellcode stored in a buffer. Please compile and run the following code, and see whether a shell is invoked. You can download the program from the website. If you are interested in writing your own shellcode, we have a separate SEED lab for that purpose. 7. call_shellcode.c: You can get it from the lab's website :/ 1. A program that launches a shell using shellcode / Hinclude #include include -/ const char code] \x31\xc0" \x50" \x68"//sh \x68/bin" \x89\xe3 \x50" \x53 \x89xel \x99 \xbox0b" \xedx80 / Line 1: xorl 1. Line 2: pushi /. Line 3: pushi 1. Line 4: pushi 1. Line 5: movi 1- Line 6: pushi 1. Line 7: pushi /Line 8: novl 7. Line 9: cda 7. Line 10: movb 7. Line 11: int teax, teax teax $0x6873221 $0x6e69622f tesp, Sebx teax tebx tesp. tecx S0xOb, tal $0x80 int main(int argo, char argv) char burleizeof(code) 1: strcpy(buf. code): (void(buf)(); SEED Labs - Buffer Overflow Vulnerability Lab Compile the code above using the following gec command. Run the program and describe your ob- servations. Please do not forget to use the execstack option, which allows code to be executed from the stack; without this option, the program will fail. gee -execstack -o call_shellcode call_shellcode.c The shellcode above invokes the execve() system call to execute /bin/sh. A few places in this shellcode are worth mentioning. First, the third instruction pushes "//sh", rather than "sh" into the stack. This is because we need a 32-bit number here, and "sh" has only 24 bits. Fortunately, "Ir is equivalent to "p", so we can get away with a double slash symbol. Second, before calling the execve() system call, we need to store name [0] (the address of the string), name (the address of the array), and NULL to the tebx, tecx, and tedx registers, respectively. Line 5 stores name [0] to tebx; Line 8 stores name to tecx; Line 9 sets tedx to zero. There are other ways to set tedx to zero (e.g., xori tedx, tedx); the one (cdq) used here is simply a shorter instruction: it copies the sign (hit 31) of the value in the EAX register (which is at this point) into every bit position in the EDX register, basically setting tedx to 0. Third, the system call execve() is called when we set tal to 11, and execute "int $0x80". 2.3 The Vulnerable Program You will be provided with the following program, which has a buffer-overflow vulnerability in Line 0. Your job is to exploit this vulnerability and gain the root privilege 7. Vunlerable program: stack.co/ 7. You can get this program from the lab's website / #include #include Hinclude 1. Changing this site will change the layout of the stack. Instructors can change this value each year, so students won't be able to use the solutions from the past Suggested value: between 0 and 400 Hifndet BUT_SIZE #define BUF_SIZE 24 Pendir Int bottcharest char bufterbur 1. The following statement has a buffer overflow problem. stropy buffer, st) Eeturn 1: int maintintaryo, char *arg) that at 15171 TIL badrile Overflow Vulnerability Lab 1. Change the site of the dunny array to randomize the parameters for this lab. Need to use the array at least once / char dummy (BUF_SIZE]: memset (dummy, 0, BUP_SIZE); badile - fopen("badfile", "1"); fread(str, sizeot (char), 517, badfile); bo(str): printf("Returned properly "); return 1; The above program has a buffer overflow vulnerability. It first reads an input from a file called badfile, and then passes this input to another buffer in the function bof(). The original input can have a maximum length of 517 bytes, but the buffer in bof() is only BUF SIZE bytes long, which is less than 517. Be- cause strcpy() does not check boundaries, buffer overflow will occur. Since this program is a root-owned Set-UID program, if a normal user can exploit this buffer overflow vulnerability, the user might be able to get a root shell. It should be noted that the program gets its input from a file called badfile. This file is under users' control. Now, our objective is to create the contents for badfile, such that when the vulnerable program copies the contents into its buffer, a root shell can be spawned. Compilation. To compile the above vulnerable program, do not forget to turn off the StackGuard and the non-executable stack protections using the-fno-stack-protector and -z execstack" options After the compilation, we need to make the program a root-owned Set-UID program. We can achieve this by first change the ownership of the program to root (Line 0), and then change the permission to 4755 to enable the Set-UID bit (Line ). It should be noted that changing ownership must be done before turning on the Set-UID bit, because ownership change will cause the Set-UID bit to be turned off 1 Note: N should be replaced by the value set by the instructor $ gec-DBUF_SIZEN -o stack -z execstack -no-stack-protector stack.c $ sudo chown root stack $ sudo chmod 4755 stack For instructors. To prevent students from using the solutions from the past for from those posted on the Internet). Instructors can change the value for BUF SIZE by requiring students to compile the server code using a different BUF SIZE value. Without the DBUF SIZE option, BUF SIZE is set to the default value 24 (defined in the program). When this value changes, the layout of the stack will change, and the solution will be different 24 Task 2: Exploiting the Vulnerability We provide you with a partially completed exploit code called "exploit.c". The goal of this code is to construct contents for badrile. In this code, the shellcode is given to you. You need to develop the rest. exploite program that creates tile containing code for launching shell .. include catdlib.h> Hinclude Binelude char shellcode \x31\x60" \x50" "\x68"//sh \x68**/bin" "\x69\xe 3" "\x50" \x53 \x89\xe1 "\x99 \xb0\xOb" \xed\x80" 2 7. Line 1: xori 1. Line 2: pushi 1. Line 3: pushi 1. Line 4: pushi 7. Line 5: movl 1. Line 6: pushi 1. Line 7: pushi 1. Line 8: movi 7. Line 9: cdg / Line 10: movb / Line 11: int Seax, Beax Seax $0x6873262 $0x6e69622 Besp, Sebx Seax Rebx tesp, tecx $0x0b, tal $0x80 void main(int arge, char * argv) char buffer (5171 FILE -badfile; 1. Initialize butter with Ox 90 (NOP instruction) ./ memset (buffer, 0x90, 517); I 7. You need to fill the buffer with appropriate contents here./ .... Put your code here ... / 1. Save the contents to the file "badfile" / badfile - fopen("./badfile", ""); fwrite(buffer, 517, 1, badfile); fclose(badf11e); After you finish the above program, compile and run it. This will generate the contents for badfile. Then run the vulnerable program stack. If your exploit is implemented correctly, you should be able to get a root shell: Important: Please compile your vulnerable program first. Please note that the program exploit.c. which generates the badfile, can be compiled with the default StackGuard protection enabled. This is because we are not going to overflow the buffer in this program. We will be overflowing the buffer in stack.o, which is compiled with the StackGuard protection disabled. $ gec -o explost exploit.c $./exploit // create the badfile $./stack 1/ launch the attack by running the vulnerable program 7. Change this will the twyout of the stack Thatractors can change this Malowac year students wants tenete the solutions from the past Suggested to even and 400 / det WESTE eine SE 24 endir Et toch char buffer V. The following statement berlok pole / strcpyhurrent Tecum at man inte har man char SESTI SEED Labs - Buffer Overflow Vulnerability Lah Io Change the they stay to and the parameters for this lab. Need to use the stay at least once / Hadfil - fopen("adrile", **) fraditiotica). 517, badita Dort print("Heurend Properlyle"> return; The above program basa buller over en vulnerability. It is reads an input from a tile called badle and then pause this input to another buffer in the functie born. The original input can have a maximum longth of 517 bytes, but the buffer in bot is only BU SIZE bytes ong. which is less than 517 He camentrepy () does not check boundaries, taller overflow will occur. Since this program hamowned Set-U10 program, if a normal user can exploit this buffer overflow vulnerability, the might be able to get a root shell. It should be noted that the program pets its input from a file called bad 12. This ile is under control Now, cur objective is to create the contents for bad le sach that when the vulnerable program copies the contents into in buffet, a root shell can be speed Compilation. To compile the above valorable program, do not forget to tum off the Stackard and the Boxecutable stack protections in the-ne-stack protector and execstack optical After the compilation, we need to make the programa pool-owned Set-Ut program. We can achieve this by first change the ownership of the program to root Line and then change the permission to 4755 to enable the Set-UID Line). It should be noted that changing ownership must be done before turning on the set-on because ownership change will cause the set-utbit to be tumed off Wer hold be replaced by the value by the instructor 5.900-DBOR - Stack Otack-toe-stack-protector stack.o do chan tot week docho 475 stack $ sudo in-af /bin/sh /bin/sh 2.2 Task 1: Running Shellcode Before starting the attack, let us get familiar with the shellcode. A shellcode is the code to launch a shell. It has to be loaded into the memory so that we can force the vulnerable program to jump to it. Consider the following program: Winelude int main() char name [21; name[0] - "/bin/sh"; name (1) - NULL; execve (name[0], name, NULL); The shellcode that we use is just the assembly version of the above program. The following program shows how to launch a shell by executing a shellcode stored in a buffer. Please compile and run the following code, and see whether a shell is invoked. You can download the program from the website. If you are interested in writing your own shellcode, we have a separate SEED lab for that purpose. 7. call_shellcode.c: You can get it from the lab's website :/ 1. A program that launches a shell using shellcode / Hinclude #include include -/ const char code] \x31\xc0" \x50" \x68"//sh \x68/bin" \x89\xe3 \x50" \x53 \x89xel \x99 \xbox0b" \xedx80 / Line 1: xorl 1. Line 2: pushi /. Line 3: pushi 1. Line 4: pushi 1. Line 5: movi 1- Line 6: pushi 1. Line 7: pushi /Line 8: novl 7. Line 9: cda 7. Line 10: movb 7. Line 11: int teax, teax teax $0x6873221 $0x6e69622f tesp, Sebx teax tebx tesp. tecx S0xOb, tal $0x80 int main(int argo, char argv) char burleizeof(code) 1: strcpy(buf. code): (void(buf)(); SEED Labs - Buffer Overflow Vulnerability Lab Compile the code above using the following gec command. Run the program and describe your ob- servations. Please do not forget to use the execstack option, which allows code to be executed from the stack; without this option, the program will fail. gee -execstack -o call_shellcode call_shellcode.c The shellcode above invokes the execve() system call to execute /bin/sh. A few places in this shellcode are worth mentioning. First, the third instruction pushes "//sh", rather than "sh" into the stack. This is because we need a 32-bit number here, and "sh" has only 24 bits. Fortunately, "Ir is equivalent to "p", so we can get away with a double slash symbol. Second, before calling the execve() system call, we need to store name [0] (the address of the string), name (the address of the array), and NULL to the tebx, tecx, and tedx registers, respectively. Line 5 stores name [0] to tebx; Line 8 stores name to tecx; Line 9 sets tedx to zero. There are other ways to set tedx to zero (e.g., xori tedx, tedx); the one (cdq) used here is simply a shorter instruction: it copies the sign (hit 31) of the value in the EAX register (which is at this point) into every bit position in the EDX register, basically setting tedx to 0. Third, the system call execve() is called when we set tal to 11, and execute "int $0x80". 2.3 The Vulnerable Program You will be provided with the following program, which has a buffer-overflow vulnerability in Line 0. Your job is to exploit this vulnerability and gain the root privilege 7. Vunlerable program: stack.co/ 7. You can get this program from the lab's website / #include #include Hinclude 1. Changing this site will change the layout of the stack. Instructors can change this value each year, so students won't be able to use the solutions from the past Suggested value: between 0 and 400 Hifndet BUT_SIZE #define BUF_SIZE 24 Pendir Int bottcharest char bufterbur 1. The following statement has a buffer overflow problem. stropy buffer, st) Eeturn 1: int maintintaryo, char *arg) that at 15171 TIL badrile Overflow Vulnerability Lab 1. Change the site of the dunny array to randomize the parameters for this lab. Need to use the array at least once / char dummy (BUF_SIZE]: memset (dummy, 0, BUP_SIZE); badile - fopen("badfile", "1"); fread(str, sizeot (char), 517, badfile); bo(str): printf("Returned properly "); return 1; The above program has a buffer overflow vulnerability. It first reads an input from a file called badfile, and then passes this input to another buffer in the function bof(). The original input can have a maximum length of 517 bytes, but the buffer in bof() is only BUF SIZE bytes long, which is less than 517. Be- cause strcpy() does not check boundaries, buffer overflow will occur. Since this program is a root-owned Set-UID program, if a normal user can exploit this buffer overflow vulnerability, the user might be able to get a root shell. It should be noted that the program gets its input from a file called badfile. This file is under users' control. Now, our objective is to create the contents for badfile, such that when the vulnerable program copies the contents into its buffer, a root shell can be spawned. Compilation. To compile the above vulnerable program, do not forget to turn off the StackGuard and the non-executable stack protections using the-fno-stack-protector and -z execstack" options After the compilation, we need to make the program a root-owned Set-UID program. We can achieve this by first change the ownership of the program to root (Line 0), and then change the permission to 4755 to enable the Set-UID bit (Line ). It should be noted that changing ownership must be done before turning on the Set-UID bit, because ownership change will cause the Set-UID bit to be turned off 1 Note: N should be replaced by the value set by the instructor $ gec-DBUF_SIZEN -o stack -z execstack -no-stack-protector stack.c $ sudo chown root stack $ sudo chmod 4755 stack For instructors. To prevent students from using the solutions from the past for from those posted on the Internet). Instructors can change the value for BUF SIZE by requiring students to compile the server code using a different BUF SIZE value. Without the DBUF SIZE option, BUF SIZE is set to the default value 24 (defined in the program). When this value changes, the layout of the stack will change, and the solution will be different 24 Task 2: Exploiting the Vulnerability We provide you with a partially completed exploit code called "exploit.c". The goal of this code is to construct contents for badrile. In this code, the shellcode is given to you. You need to develop the rest. exploite program that creates tile containing code for launching shell .. include catdlib.h> Hinclude Binelude char shellcode \x31\x60" \x50" "\x68"//sh \x68**/bin" "\x69\xe 3" "\x50" \x53 \x89\xe1 "\x99 \xb0\xOb" \xed\x80" 2 7. Line 1: xori 1. Line 2: pushi 1. Line 3: pushi 1. Line 4: pushi 7. Line 5: movl 1. Line 6: pushi 1. Line 7: pushi 1. Line 8: movi 7. Line 9: cdg / Line 10: movb / Line 11: int Seax, Beax Seax $0x6873262 $0x6e69622 Besp, Sebx Seax Rebx tesp, tecx $0x0b, tal $0x80 void main(int arge, char * argv) char buffer (5171 FILE -badfile; 1. Initialize butter with Ox 90 (NOP instruction) ./ memset (buffer, 0x90, 517); I 7. You need to fill the buffer with appropriate contents here./ .... Put your code here ... / 1. Save the contents to the file "badfile" / badfile - fopen("./badfile", ""); fwrite(buffer, 517, 1, badfile); fclose(badf11e); After you finish the above program, compile and run it. This will generate the contents for badfile. Then run the vulnerable program stack. If your exploit is implemented correctly, you should be able to get a root shell: Important: Please compile your vulnerable program first. Please note that the program exploit.c. which generates the badfile, can be compiled with the default StackGuard protection enabled. This is because we are not going to overflow the buffer in this program. We will be overflowing the buffer in stack.o, which is compiled with the StackGuard protection disabled. $ gec -o explost exploit.c $./exploit // create the badfile $./stack 1/ launch the attack by running the vulnerable program