Question: Consider the following challenge-response mutual authentication protocol between Alice, a client, and Bob, a stateless server that does not remember values from a previous
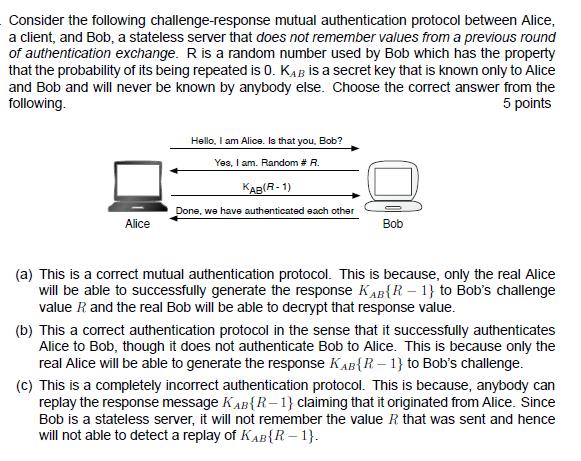
Consider the following challenge-response mutual authentication protocol between Alice, a client, and Bob, a stateless server that does not remember values from a previous round of authentication exchange. R is a random number used by Bob which has the property that the probability of its being repeated is O. KAB is a secret key that is known only to Alice and Bob and will never be known by anybody else. Choose the correct answer from the following. 5 points Alice Hello, I am Alice. Is that you, Bob? Yes, I am. Random # R. KAB(R-1) Done, we have authenticated each other Bob (a) This is a correct mutual authentication protocol. This is because, only the real Alice will be able to successfully generate the response KAB (R-1) to Bob's challenge value R. and the real Bob will be able to decrypt that response value. (b) This a correct authentication protocol in the sense that it successfully authenticates Alice to Bob, though it does not authenticate Bob to Alice. This is because only the real Alice will be able to generate the response KAB{R-1} to Bob's challenge. (c) This is a completely incorrect authentication protocol. This is because, anybody can replay the response message KAB {R-1) claiming that it originated from Alice. Since Bob is a stateless server, it will not remember the value R. that was sent and hence will not able to detect a replay of KAB{R-1}.
Step by Step Solution
3.42 Rating (149 Votes )
There are 3 Steps involved in it
The answer is c This is a completely incorrect authentication protocol Heres why Bob does not authenticate Alice Anyone can send the message KABR1 to ... View full answer

Get step-by-step solutions from verified subject matter experts


