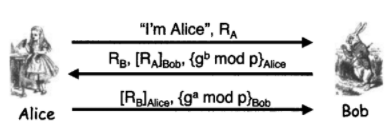
Question: Consider the following mutual authentication and key establishment protocol, where the session key is given by K = g ab mod p. Suppose that Alice
Consider the following mutual authentication and key establishment protocol, where the session key is given by K = gab mod p.
Suppose that Alice attempts to initiate a connection with Bob using this protocol.
a. Show that Trudy can attack the protocol so that both of the following will occur.
i. Alice and Bob authenticate each other.
ii. Trudy knows Alice's session key.
Hint: Consider a man-in-the-middle attack.
b. Is this attack of any use to Trudy?
Alice "I'm Alice", R RB, IRAlDob, (gb mod p Alce [RelAuce, (ga mod p)Bob Bob
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


