Question: Consider the SSL protocol in Figure 10.4. Modify the protocol so that the authentication is based Fon a digital signature. Your protocol must provide secure
Consider the SSL protocol in Figure 10.4. Modify the protocol so that the authentication is based Fon a digital signature. Your protocol must provide secure authentication of the server Bob, and a secure session key.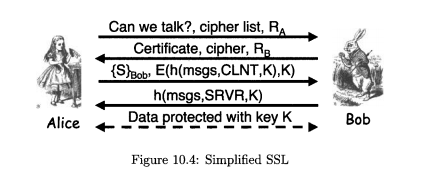
Can we talk?, cipher list, RA Certificate, cipher, RB {S)Bob, E(h(msgs,CLNT,K),K) h(msgs,SRVR.K) Alice Data protected-ith keyK Bob Figure 10.4: Simplified SSL
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


