Question: crypto (-/Downloads/crypto) - .../crypto.py Doctest encrypt.char d Cryptop return char encrypt_str(source, slugs): Given source and slug lists and strings, return a version of s where
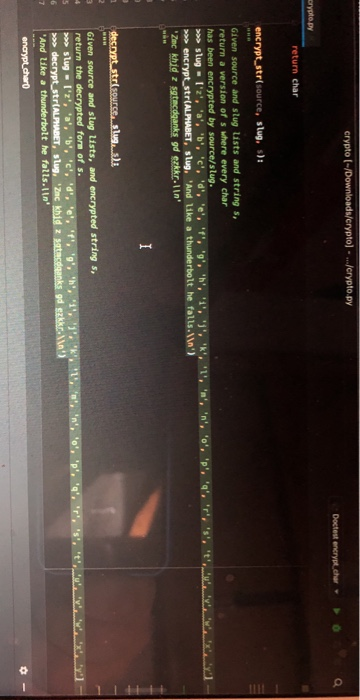
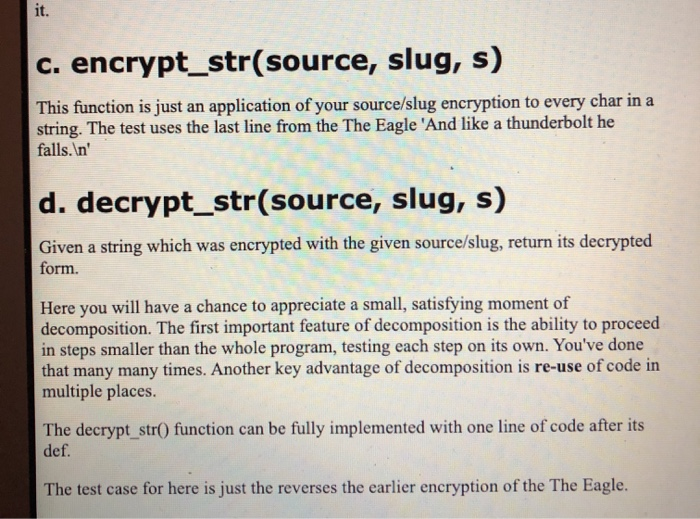
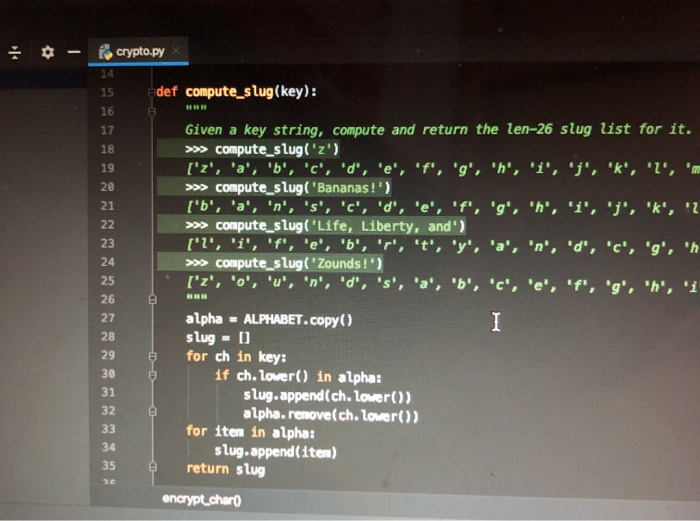
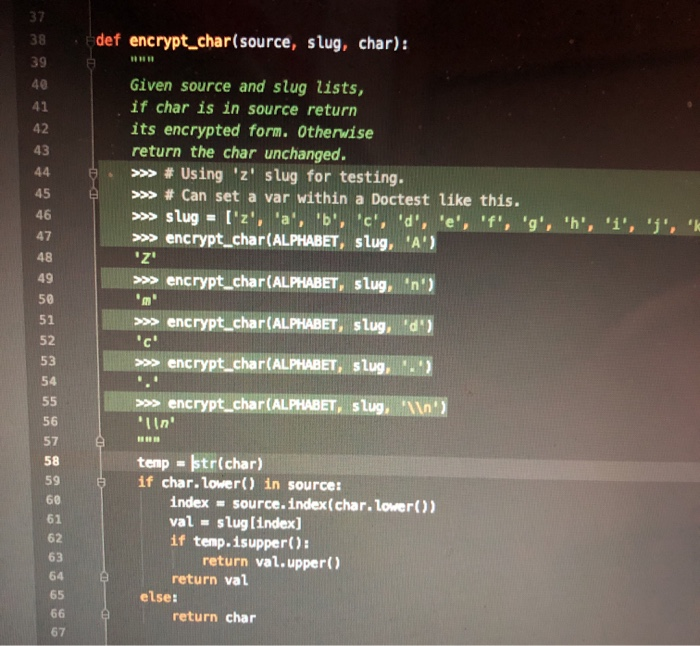
crypto (-/Downloads/crypto) - .../crypto.py Doctest encrypt.char d Cryptop return char encrypt_str(source, slugs): Given source and slug lists and strings, return a version of s where every char has been encrypted by source/slug. > slug - l'z'. 'a''b', 'c','d', 'e', '1'. 'o'. 'h'. '1,'','','1','', '', 'o', 'p', 'a', 'T, 'S', >> encrypt_str(ALPHABET. Slug, 'And like a thunderbolt he fails.\ ') "Zac khid z sgte danks gd ekkrin TY decrypt_str(sourceslu....! , '. '. 'r', 's'. " Given source and slug lists, and encrypted string s, return the decrypted form of s. >>> slug - l'z', 'a', 'b', 'c','d', 'e','f', 's', 'h','1','','K' . . . . . . >> decryptstr(ALPHABET, Slug, Zac khidz stacdanks dekken And Uke a thunderbolt he falls. In encrypt_charo c. encrypt_str(source, slug, s) This function is just an application of your source/slug encryption to every char in a string. The test uses the last line from the The Eagle 'And like a thunderbolt he falls. In d. decrypt_str(source, slug, s) Given a string which was encrypted with the given source/slug, return its decrypted form. Here you will have a chance to appreciate a small, satisfying moment of decomposition. The first important feature of decomposition is the ability to proceed in steps smaller than the whole program, testing each step on its own. You've done that many many times. Another key advantage of decomposition is re-use of code in multiple places. The decrypt_str() function can be fully implemented with one line of code after its def. The test case for here is just the reverses the earlier encryption of the The Eagle. # - crypto.py X 15 def compute_slug(key): Given a key string, compute and return the len-26 slug list for it. >>> compute_slug('z') ['z', 'a', 'b', 'c': 'd', 'e', 'f', 'g', 'h', 'i', 'j', 'k', '2', 'm >>> compute_slug('Bananas!) ['b', 'a', 'n', 's', 'c', 'd', 'e', 'f', 'g', 'h', '1', 'j', 'k', '2 >>> compute_slug('Life, Liberty, and') ['2', 'i', 'f', 'e', 'b', 'r', 't', 'y', 'a', 'n', 'd', 'c','g', 'h >>> compute_slug('Zounds!') I'z', 'o', 'u', 'n', 'd', 's', 'a', 'b', 'c', 'e', 'f','g', 'h', 'i alpha = ALPHABET.copy() slug = [] for ch in key: if ch. Lower() in alpha: slug.append(ch. Lower()) alpha.remove(ch. Lower()) for iten in alpha: slug.append( iten) return slug encrypt.chart def encrypt_char( source, slug, char): Given source and slug lists, if char is in source return its encrypted form. Otherwise return the char unchanged. >>> # Using 'z' slug for testing. >>> # Can set a var within a Doctest like this. >>> slug = ['z', 'a', 'b', 'c', 'd', 'e', 'f', 'g', 'h', '1', '', 'l >>> encrypt_char(ALPHABET, slug, 'A') 'Z >>> encrypt_char(ALPHABET, slug, n') >>> encrypt_char(ALPHABET, slug, 'd') >>> encrypt_char(ALPHABET, slug, ..') >>> encrypt_char(ALPHABET, slug, "\ ') lin' temp = str(char) if char. lower() in source: Index = source. index(char. lower()) val = slug [index] if temp. 1supper(): return val. upper() return val else: return char
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


