Question: Cryptology Use : ID 53263 sum = 19 Plaintext T = initial text IT (full word) Homework nr 1 Ciphertext C = result of IT
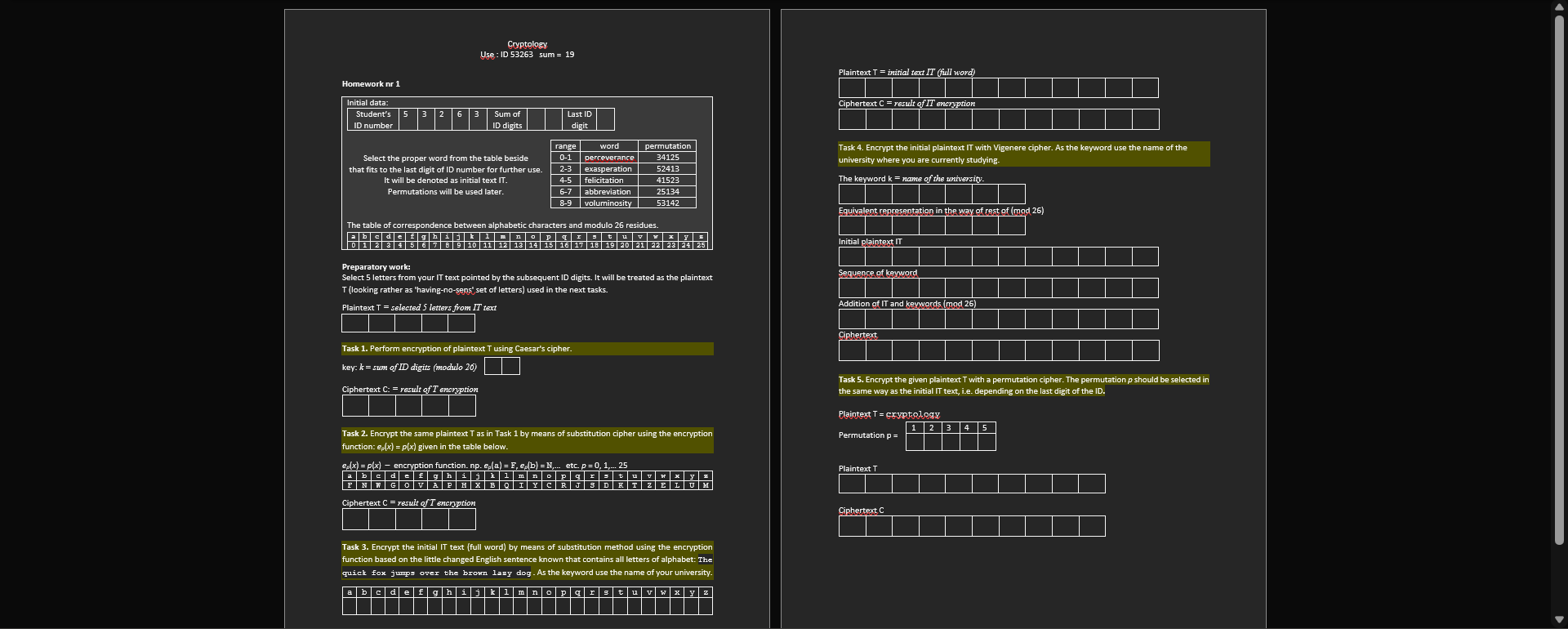
Cryptology Use : ID 53263 sum = 19 Plaintext T = initial text IT (full word) Homework nr 1 Ciphertext C = result of IT encryption Initial data Student's 5 ID number 32 Sum of ID digits Last ID digit Select the proper word from the table beside that fits to the last digit of ID number for further use. It will be denoted as initial text IT. Permutations will be used later. range word 0-1 perceverance 2-3 exasperation 4-5 felicitation 6-7 abbreviation 8-9 voluminosity permutation 34125 52413 41523 25134 53142 Task 4. Encrypt the initial plaintext IT with Vigenere cipher. As the keyword use the name of the university where you are currently studying- The keyword k = name of the university Equivalent representation in the way of rest of (mod 26) The table of correspondence between alphabetic characters and modulo 26 residues. Duc de 191111010 P929tu vY 273 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 Initial plaintext IT Sequence of keyword Preparatory work: Select 5 letters from your IT text pointed by the subsequent ID digits. It will be treated as the plaintext Tlooking rather as 'having-no-sens' set of letters) used in the next tasks. Plaintext T = selected 5 letters from IT text Addition of IT and keywords (mad 26) Ciphertext Task 1. Perform encryption of plaintext T using Caesar's cipher. key: k = sum of ID digits (modulo 26) Ciphertext C: - result of T encryption Task 5.Encrypt the given plaintext T with a permutation cipher. The permutation p should be selected in the same way as the initial IT text, i.e. depending on the last digit of the ID. Plaintext T = cryptology 1 2 3 4 Permutation p = Task 2. Encrypt the same plaintext T as in Task 1 by means of substitution cipher using the encryption function: ep(x) = plx) given in the table below. Plaintext elx) = p(x) - encryption function. np.e(a) = F, e. b) = N, etc. p=0,1.... 25 - bed 21 g h i j 11mn DP w x y z FNWGOVAPHX BOI DKT ZELUM Ciphertext C = result of T encryption Ciphertext C Task 3. Encrypt the initial IT text (full word) by means of substitution method using the encryption function based on the little changed English sentence known that contains all letters of alphabet: The quick fox jumps over the brown lasy dog. As the keyword use the name of your university. b c d e f g h i j k l m n o p q r s t u v w x Y Z
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


