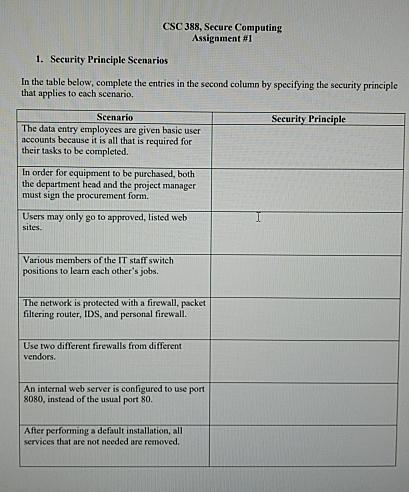
Question: CSC 3 8 8 , Secure Computing Assignment # 1 Security Principle Scenarios In the table below, complete the entries in the second column by
CSC Secure Computing
Assignment #
Security Principle Scenarios
In the table below, complete the entries in the second column by specifying the security principle that applies to each scenario.
tableScenarioSecurity PrincipletableThe data entry ermployees are given basic useraccounts because it is all that is required fortheir tasks to be completed.tableIn order for equipment to be purchased, boththe department head and the project managermust sign the procurement form.tableUsers may only go to approved, listed websitestableVarious members of the IT staff switchpositions to learn each other's jobs.tableThe network is protected with a firewall, packetfiltering router, IDS, and personal firewall.tableUse two different firewalls from differentverdorstableAfter performing a default installation, allservices that are not needed are removed. instead of the usual port
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


