Question: Database manegment system yes, that would be better Database Management System Project STUDITIONS To be submitted via Google Classroom. Refer to Google Classroom for submission

Database manegment system
yes, that would be better
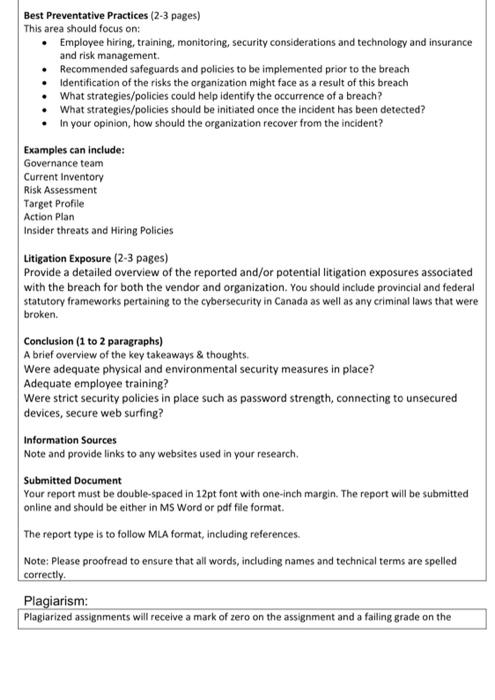
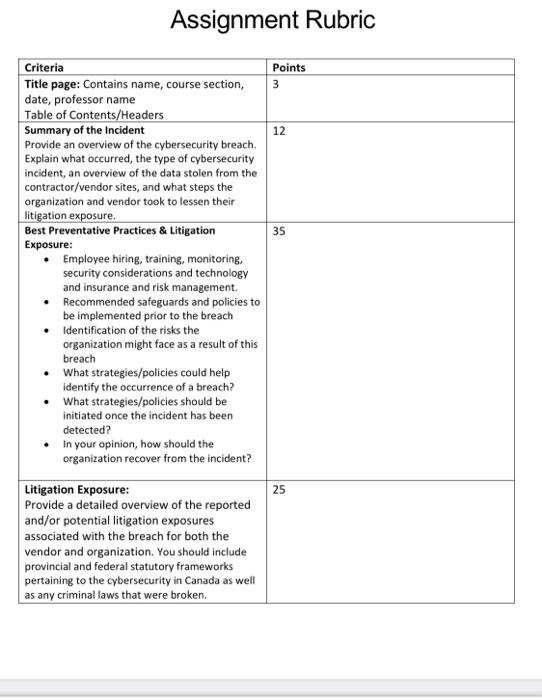
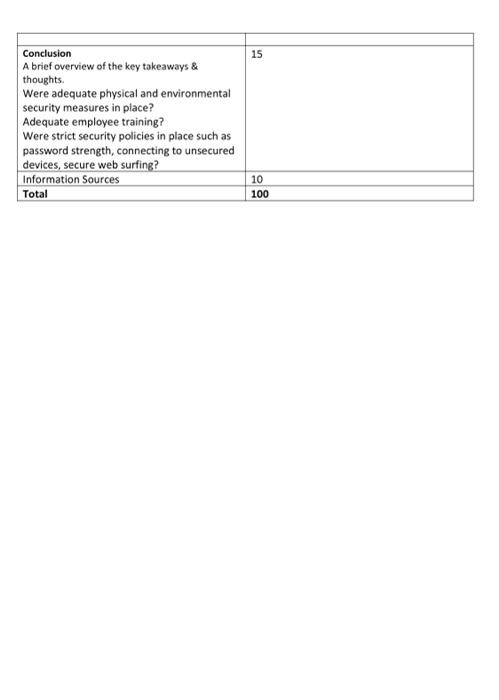
Database Management System Project STUDITIONS To be submitted via Google Classroom. Refer to Google Classroom for submission instructions 10% of final grade Refer to course timeline posted on Classroom for specific due date Submission Instructions Value Due Date Learning Outcomes Covered in Assignment 1. Evaluate the litigation exposure in cyber security 2. Discuss the best practices to implement prior to a breach. a w Assignment The objective of the assignment is to assess how to implement some of the best practices in cyber Security prior to a breach in order to avoid or limit the impact Use the previous breach from your assignment or another cybersecurity breach example from within the last 5 years. You are to identify a cybersecurity breach event that occurred over the past five years that was reported in the media. Evaluation: Please see the Rubric on the next page for Evaluation Criteria. Submission: Your report should contain the six (6) sections noted Title page Table of Contents/Headers Introduction Summary of the incident Best Preventative Practices Conclusion Information Sources Title Page Your name, course, section, date, the professor's name, the name of the company. Introduction (2 to 3 paragraphs) A brief description and background of the organization you have selected and why. Summary of the Incident (2 pages) Provide an overview of the cybersecurity breach. Explain what occurred, the type of cybersecurity incident, an overview of the data stolen from the contractor/vendor sites, and what steps the Best Preventative Practices (2-3 pages) This area should focus on: Employee hiring, training, monitoring, security considerations and technology and insurance and risk management Recommended safeguards and policies to be implemented prior to the breach Identification of the risks the organization might face as a result of this breach What strategies/policies could help identify the occurrence of a breach? What strategies/policies should be initiated once the incident has been detected? In your opinion, how should the organization recover from the incident? Examples can include: Governance team Current Inventory Risk Assessment Target Profile Action Plan Insider threats and Hiring Policies Litigation Exposure (2-3 pages) Provide a detailed overview of the reported and/or potential litigation exposures associated with the breach for both the vendor and organization. You should include provincial and federal statutory frameworks pertaining to the cybersecurity in Canada as well as any criminal laws that were broken. Conclusion (1 to 2 paragraphs) A brief overview of the key takeaways & thoughts Were adequate physical and environmental security measures in place? Adequate employee training? Were strict security policies in place such as password strength, connecting to unsecured devices, secure web surfing? Information Sources Note and provide links to any websites used in your research. Submitted Document Your report must be double-spaced in 12pt font with one-inch margin. The report will be submitted online and should be either in MS Word or pdf file format. The report type is to follow MLA format, including references Note: Please proofread to ensure that all words, including names and technical terms are spelled correctly. Plagiarism Plagiarized assignments will receive a mark of zero on the assignment and a falling grade on the Assignment Rubric Points 3 12 35 Criteria Title page: Contains name, course section, date, professor name Table of Contents/Headers Summary of the incident Provide an overview of the cybersecurity breach. Explain what occurred, the type of cybersecurity incident, an overview of the data stolen from the contractor/vendor sites, and what steps the organization and vendor took to lessen their litigation exposure Best Preventative Practices & Litigation Exposure: Employee hiring, training, monitoring, security considerations and technology and insurance and risk management. Recommended safeguards and policies to be implemented prior to the breach Identification of the risks the organization might face as a result of this breach What strategies/policies could help identify the occurrence of a breach? What strategies/policies should be initiated once the incident has been detected? In your opinion, how should the organization recover from the incident? Litigation Exposure: Provide a detailed overview of the reported and/or potential litigation exposures associated with the breach for both the vendor and organization. You should include provincial and federal statutory frameworks pertaining to the cybersecurity in Canada as well as any criminal laws that were broken. 25 15 Conclusion A brief overview of the key takeaways & thoughts Were adequate physical and environmental security measures in place? Adequate employee training? Were strict security policies in place such as password strength, connecting to unsecured devices, secure web surfing? Information Sources Total 10 100 Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


