Question: Exercise (30 pt) Execute the next cell to produce a message encrypted with the Hill cipher: In [2]: x Matrix((l1, 2, 21, [1, 1, 0],
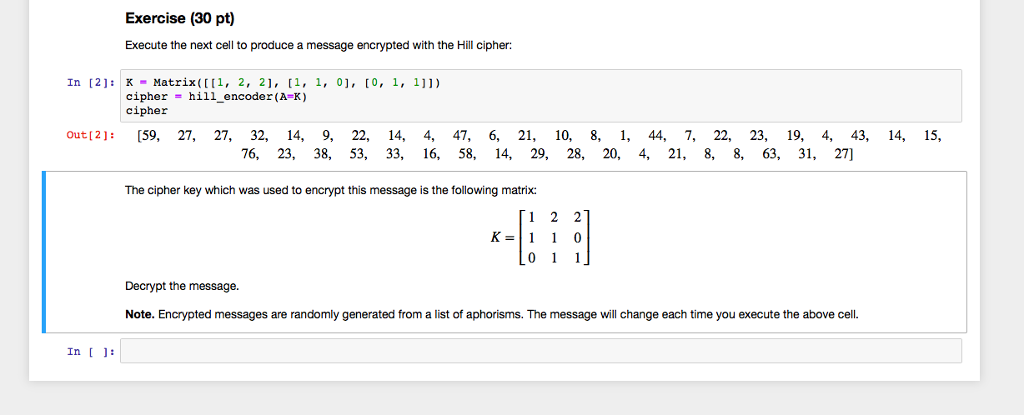
Exercise (30 pt) Execute the next cell to produce a message encrypted with the Hill cipher: In [2]: x Matrix((l1, 2, 21, [1, 1, 0], [0, 1,111 cipher cipher hill-encoder(A-K) = Out(2]: [59, 27, 27, 32, 14, 9, 22, 14, 4, 47, 6, 21, 10, 8, 1, 44, 7, 22, 23, 19, 4, 43, 14, 15, 76, 23, 38, 53, 33, 16. 58, 14, 29, 28, 20. 4, 21, 8, 8. 63, 31, 27) The cipher key which was used to encrypt this message is the following matrix: 1 2 21 Decrypt the message. Note. Encrypted messages are randomly generated from a list of aphorisms. The message will change each time you execute the above cell. In [ ] Exercise (30 pt) Execute the next cell to produce a message encrypted with the Hill cipher: In [2]: x Matrix((l1, 2, 21, [1, 1, 0], [0, 1,111 cipher cipher hill-encoder(A-K) = Out(2]: [59, 27, 27, 32, 14, 9, 22, 14, 4, 47, 6, 21, 10, 8, 1, 44, 7, 22, 23, 19, 4, 43, 14, 15, 76, 23, 38, 53, 33, 16. 58, 14, 29, 28, 20. 4, 21, 8, 8. 63, 31, 27) The cipher key which was used to encrypt this message is the following matrix: 1 2 21 Decrypt the message. Note. Encrypted messages are randomly generated from a list of aphorisms. The message will change each time you execute the above cell. In [ ]
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


