Question: Figure 3: Table for permuting alphabet Your Task: Cryptanalysis of an information system is the study of mathematical techniques for attempting to defeat information security
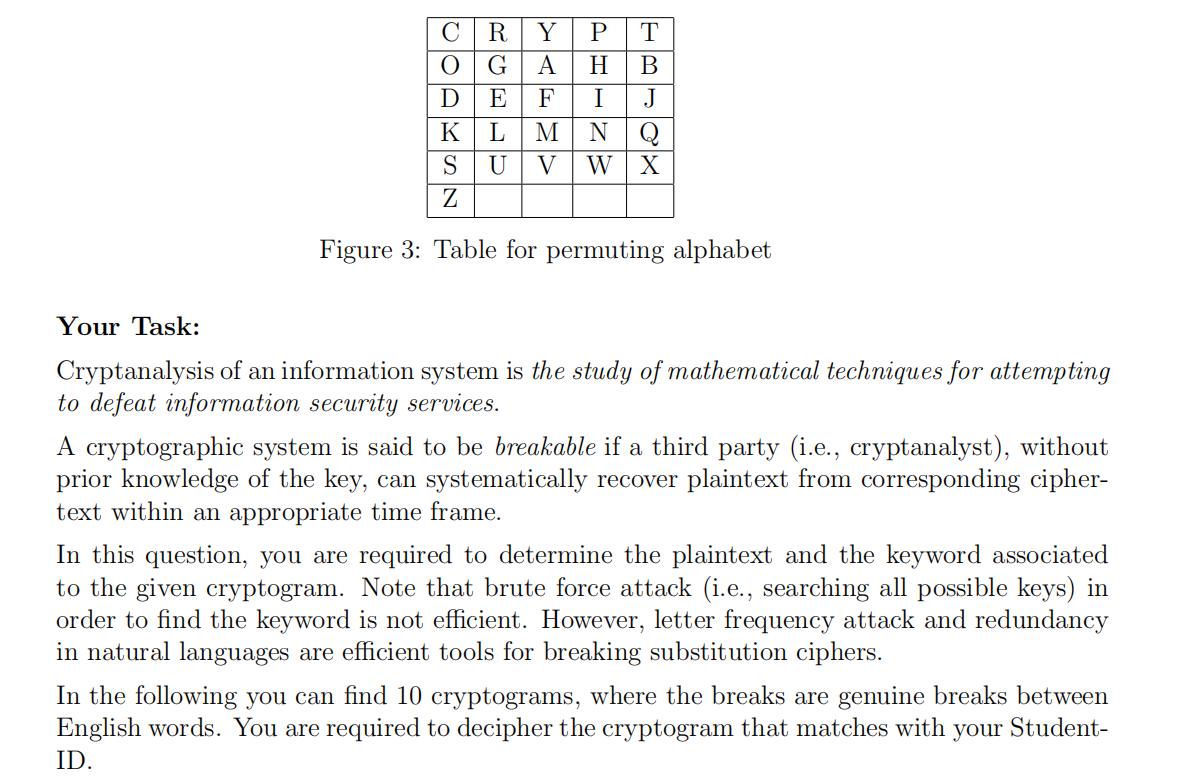
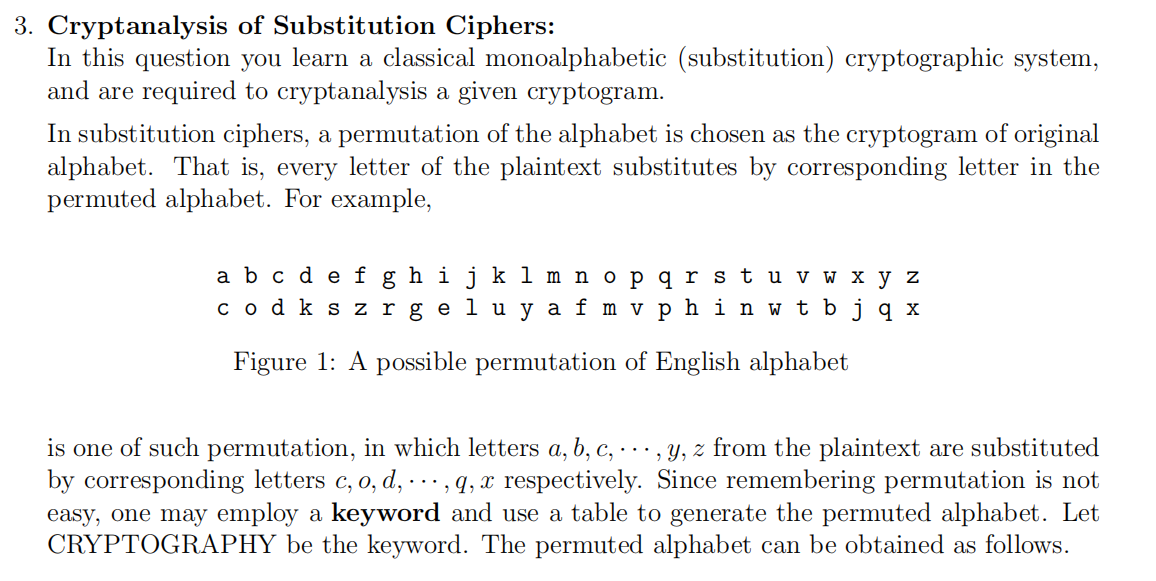
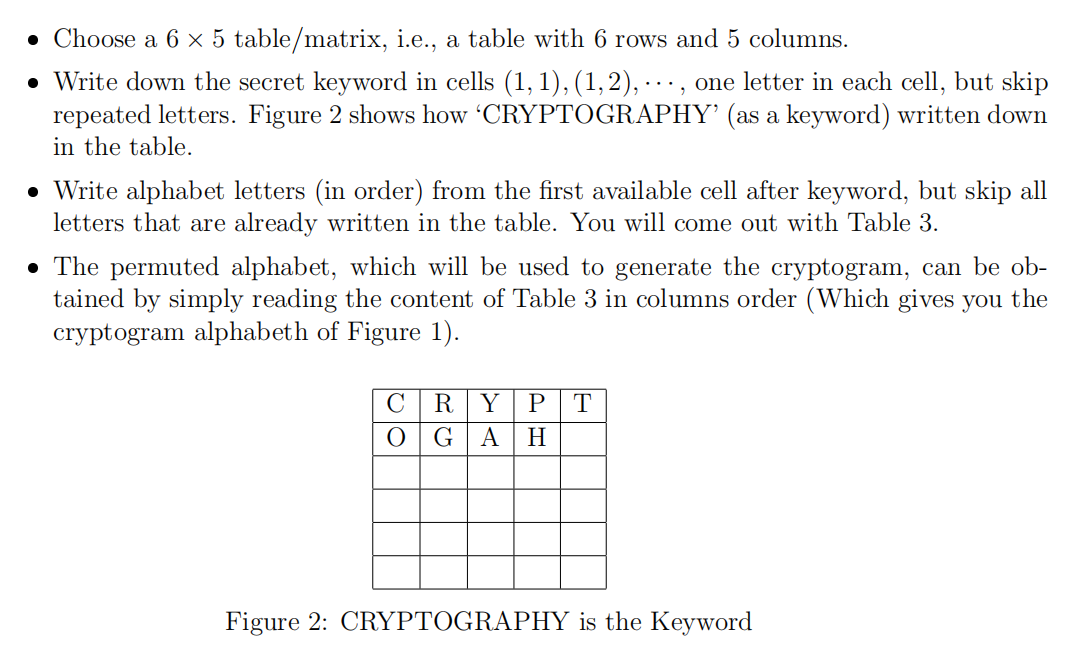


Figure 3: Table for permuting alphabet Your Task: Cryptanalysis of an information system is the study of mathematical techniques for attempting to defeat information security services. A cryptographic system is said to be breakable if a third party (i.e., cryptanalyst), without prior knowledge of the key, can systematically recover plaintext from corresponding cipher- text within an appropriate time frame. In this question, you are required to determine the plaintext and the keyword associated to the given cryptogram. Note that brute force attack (i.e., searching all possible keys) in order to find the keyword is not efficient. However, letter frequency attack and redundancy in natural languages are efficient tools for breaking substitution ciphers. In the following you can find 10 cryptograms, where the breaks are genuine breaks between English words. You are required to decipher the cryptogram that matches with your Student- ID. Rubric for Question 3: 2 marks for showing the intermediate result of cryptanalyzing (i.e., when about half of the letters in the alphabet is determined). 2 marks for determination of the whole alphabet and/or the complete plaintext. 4 marks for obtaining the 6x5 table associated with the cryptogram alphabet (see Figure 3). 2 marks for determination of the keyword. Note that determination of a correct keyword from wrong table in the previous step is not accepted. 3. Cryptanalysis of Substitution Ciphers: In this question you learn a classical monoalphabetic (substitution) cryptographic system, and are required to cryptanalysis a given cryptogram. In substitution ciphers, a permutation of the alphabet is chosen as the cryptogram of original alphabet. That is, every letter of the plaintext substitutes by corresponding letter in the permuted alphabet. For example, abcdefghijklmnopqrstuvwzxyaz codkszrgeluyafmvphinwtb]jqxzx Figure 1: A possible permutation of English alphabet is one of such permutation, in which letters a, b, , - - -, y, z from the plaintext are substituted by corresponding letters , 0,d, - - -, q, r respectively. Since remembering permutation is not easy, one may employ a keyword and use a table to generate the permuted alphabet. Let CRYPTOGRAPHY be the keyword. The permuted alphabet can be obtained as follows. Choose a 6 x 5 table/matrix, i.e., a table with 6 rows and 5 columns. Write down the secret keyword in cells (1,1),(1,2),---, one letter in each cell, but skip repeated letters. Figure 2 shows how 'CRYPTOGRAPHY' (as a keyword) written down in the table. Write alphabet letters (in order) from the first available cell after keyword, but skip all letters that are already written in the table. You will come out with Table 3. The permuted alphabet, which will be used to generate the cryptogram, can be ob- tained by simply reading the content of Table 3 in columns order (Which gives you the cryptogram alphabeth of Figure 1). Figure 22 CRYPTOGRAPHY is the Keyword \fRubric for Question 3: 2 marks for showing the intermediate result of cryptanalyzing (i.e., when about half of the letters in the alphabet is determined). 2 marks for determination of the whole alphabet and/or the complete plaintext. 4 marks for obtaining the 6x5 table associated with the cryptogram alphabet (see Figure 3). 2 marks for determination of the keyword. Note that determination of a correct keyword from wrong table in the previous step is not accepted. \f
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


