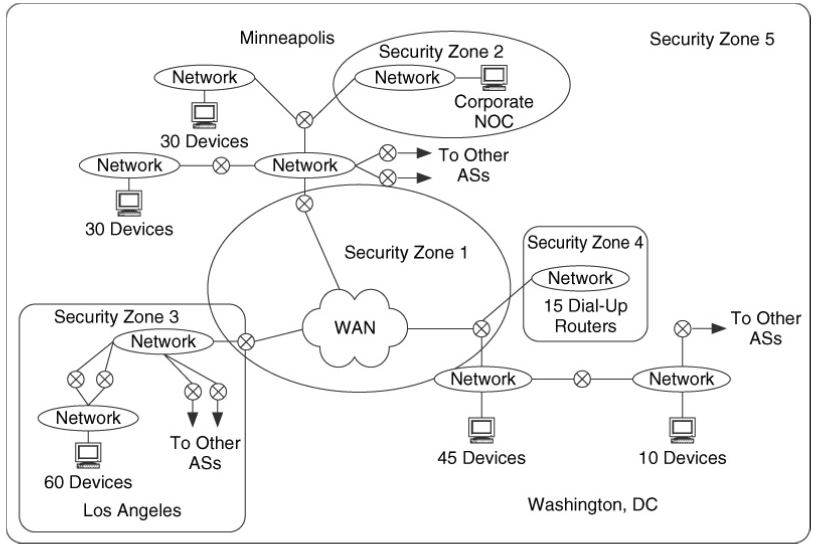
Question: Figure 9.17 copied from the text below shows 5 security zones required by the customer. These zones are prioritized, such that Security Zone 5 provides
Figure 9.17 copied from the text below shows 5 security zones required by the customer. These
zones are prioritized, such that Security Zone 5 provides basic security for the entire network,
and starting with zone 5, zones 4, 3, 2, 1 have increasing degrees of security, and Security Zone
1 with the highest level of security.
For this network:
a. What security mechanisms can be applied within each security zone, and at the interfaces
between security zones, to achieve increasing degrees of security?
Security Zone 1- WAN (Answer)
Security Zone 2- Corporate NOC (Answer)
Security Zone 3- Los Angeles (Answer)
Security Zone 4- Washington, DC (Answer)
Security Zone 5 - (Answer)
b. Which architectural models are most applicable to this network? Show how each model can
be applied.
Figure 9.17 from McCabe Exercise 4, Chapter 9
Minneapolis Security Zone 5 Security Zone 2 Network Network Corporate NOC 30 Devices To Other ASs Network Network 30 Devices Security Zone 4 Network 15 Dial-Up Security Zone 1 Security Zone 3 To Other ASs WAN Routers Network Network Network Network To Other ASs 45 Devices 10 Devices 60 Devices Los Angeles Washington, DC Minneapolis Security Zone 5 Security Zone 2 Network Network Corporate NOC 30 Devices To Other ASs Network Network 30 Devices Security Zone 4 Network 15 Dial-Up Security Zone 1 Security Zone 3 To Other ASs WAN Routers Network Network Network Network To Other ASs 45 Devices 10 Devices 60 Devices Los Angeles Washington, DC
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


