Question: Given below a Point-to-point communication trace taken by Wireshark a network protocol analyzer software. ----- ETHER: ----- Ethernet Header ETHER: Packet 3 arrived at 11:42:27.64
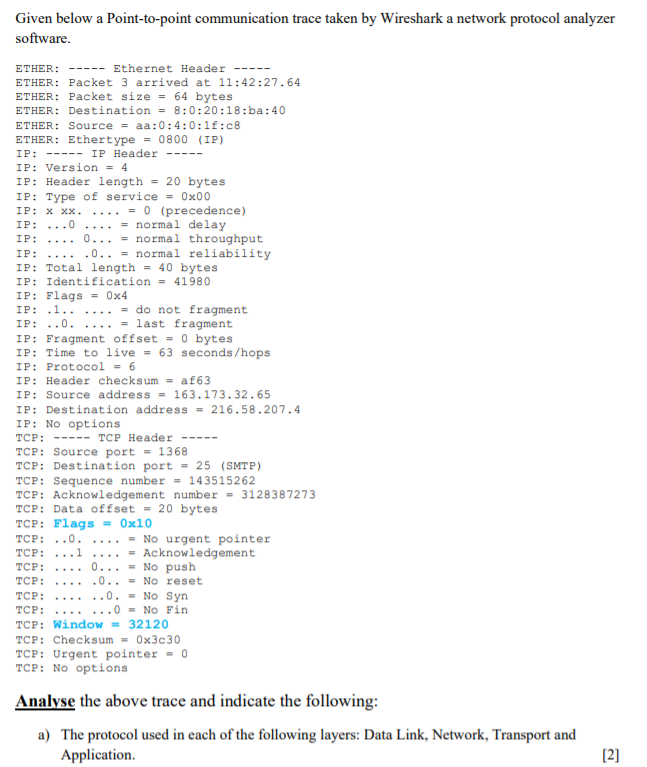
Given below a Point-to-point communication trace taken by Wireshark a network protocol analyzer software. ----- ETHER: ----- Ethernet Header ETHER: Packet 3 arrived at 11:42:27.64 ETHER: Packet size = 64 bytes ETHER: Destination = 8:0:20:18:ba: 40 ETHER: Source = aa:0:4:0:15:08 ETHER: Ethertype = 0800 (IP) IP: IP Header ----- IP: Version = 4 IP: Header length = 20 bytes IP: Type of service = 0x00 IP: XXX = 0 (precedence) IP: ...0 .... = normal delay IP: ....0... = normal throughput IP: .0.. = normal reliability IP: Total length - 40 bytes IP: Identification = 41980 IP: Flags = 0x4 IP: .1.. = do not fragment IP: ..0. .... = last fragment IP: Fragment offset = 0 bytes IP: Time to live = 63 seconds/hops IP: Protocol = 6 IP: Header checksum = af63 IP: Source address = 163.173.32.65 IP: Destination address = 216.58.207.4 IP: No options TCP: ----- TCP Header TCP: Source port = 1368 TCP: Destination port = 25 (SMTP) TCP: Sequence number = 143515262 TCP: Acknowledgement number = 3128387273 TCP: Data offset = 20 bytes TCP: Flags = 0x10 TCP: ..0. = No urgent pointer TCP: ...1 .... = Acknowledgement TCP: 0... = No push TCP: .0.. - No reset TCP: ..0. = No Syn TCP: ...0 = No Fin TCP: Window = 32120 TCP: Checksum = 0x3c30 TCP: Urgent pointer = 0 TCP: No options Analyse the above trace and indicate the following: a) The protocol used in each of the following layers: Data Link, Network, Transport and Application [2]
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


