Question: GPG ( GNU Privacy Guard ) is a software tool used to encrypt files, create digital signatures, and manage public and private keys. It's a
GPG GNU Privacy Guard is a software tool used to encrypt files, create digital signatures, and manage public and private keys. It's a part of the GNU Project and provides a free software alternative to the proprietary PGP Pretty Good Privacy software program.
Both GPG and PGP can use RSA RivestShamirAdleman one of the first publickey cryptosystems, for encrypting and decrypting messages and for digital signatures.
The security of RSA is based on the practical difficulty of factoring the product of two large prime numbers.
First, a pair of public and private Keys are generated as follows:
Choose two distinct largelprime numbers and
Compute This is used as the modulus for both the public and private keys.
Compute the totient
Choose an integer e such that modnmcmmodnpmodmod
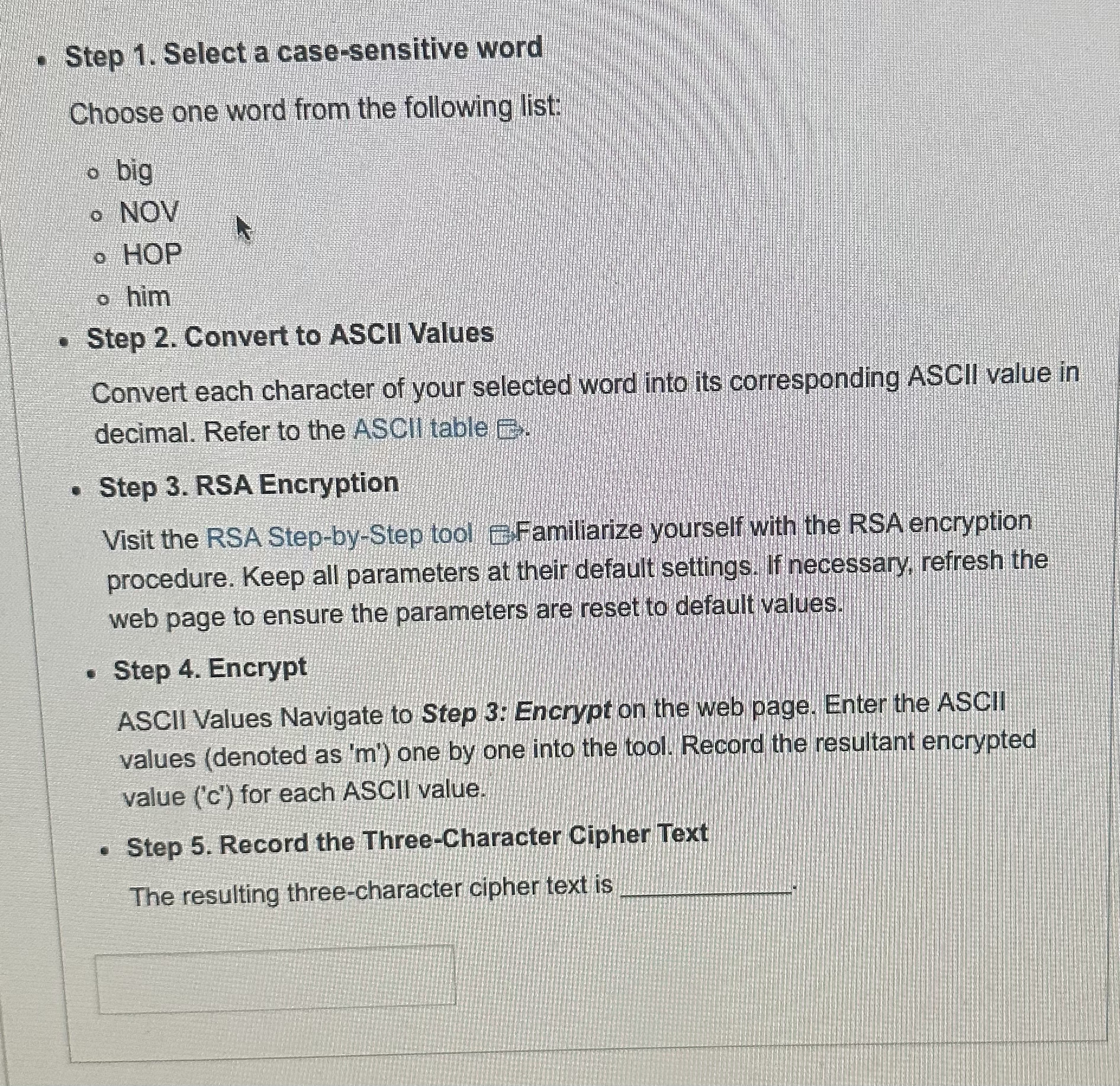
Step Select a casesensitive word
Choose one word from the following list:
big
NOV
HOP
him
Step Convert to ASCII Values
Convert each character of your selected word into its corresponding ASCII value in decimal. Refer to the ASCl table E
Step RSA Encryption
Visit the RSA StepbyStep tool EFamiliarize yourself with the RSA encryption procedure. Keep all parameters at their default settings. If necessary, refresh the web page to ensure the parameters are reset to default values.
Step Encrypt
ASCII Values Navigate to Step : Encrypt on the web page. Enter the ASCII values denoted as one by one into the tool. Record the resultant encrypted value c for each ASCII value.
Step Record the ThreeCharacter Cipher Text
The resulting threecharacter cipher text is
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


