Question: Hello all. I want to solve this question with full answer and clear 4. (30 points) Bad MAC design. In this question, we are confronted
 Hello all. I want to solve this question with full answer and clear
Hello all. I want to solve this question with full answer and clear
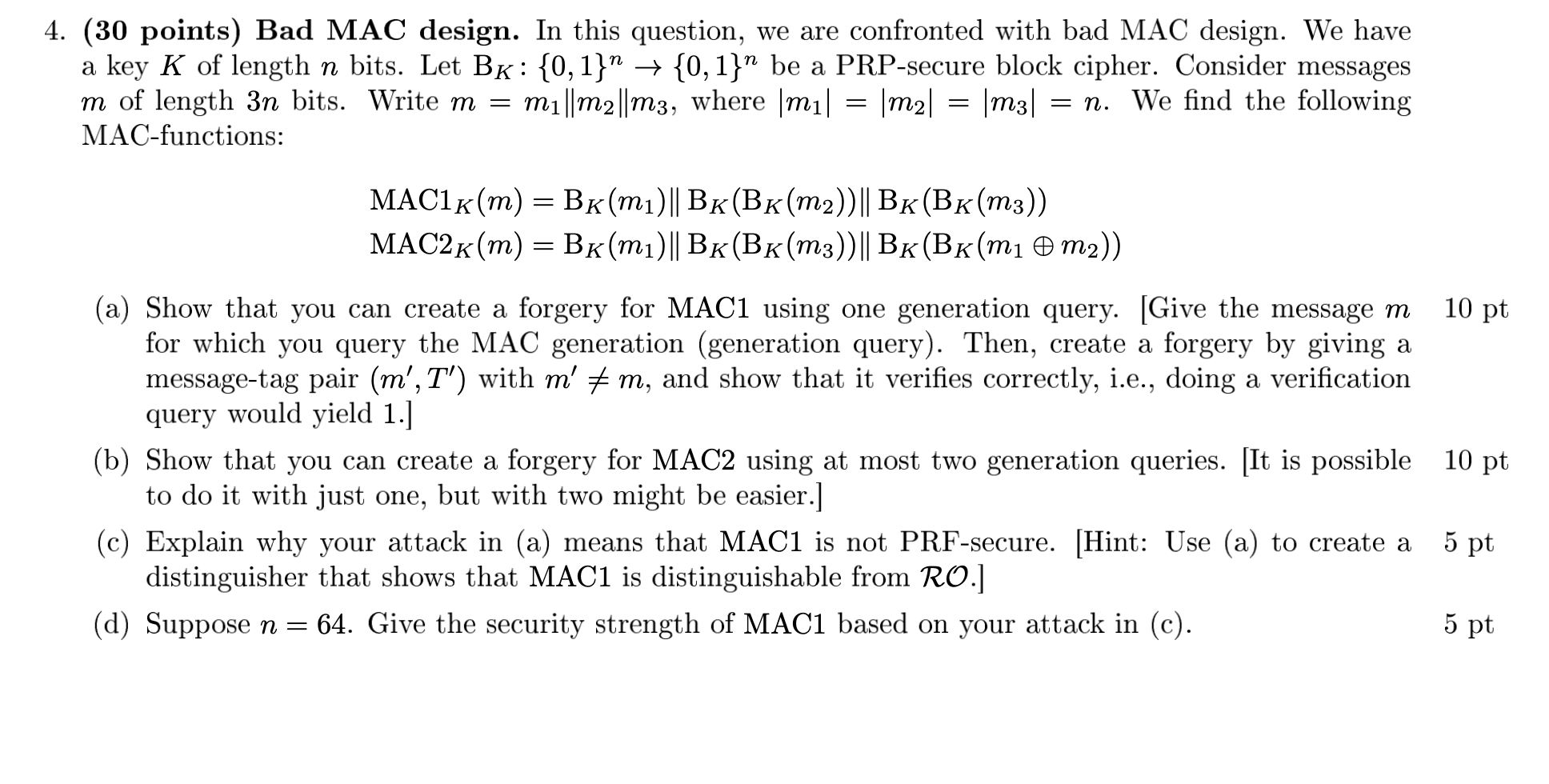
4. (30 points) Bad MAC design. In this question, we are confronted with bad MAC design. We have a key K of length n bits. Let BK: {0,1}" + {0,1}" be a PRP-secure block cipher. Consider messages m of length 3n bits. Write m = mi||M2||M3, where |mi| |m2| = |m3| = n. We find the following MAC-functions: MAC1k(m) = Bk(mi)|| BK(BK(m2)|| BK(BK(m3)) MAC2K(m) = BK(m1)|| BK(BK(m3))|| BK(BK(mi e m2)) 10 pt (a) Show that you can create a forgery for MAC1 using one generation query. [Give the message m for which you query the MAC generation (generation query). Then, create a forgery by giving a message-tag pair (m',T') with m' # m, and show that it verifies correctly, i.e., doing a verification query would yield 1.] (b) Show that you can create a forgery for MAC2 using at most two generation queries. [It is possible 10 pt to do it with just one, but with two might be easier.] (c) Explain why your attack in (a) means that MAC1 is not PRF-secure. (Hint: Use (a) to create a 5 pt distinguisher that shows that MAC1 is distinguishable from RO.] (d) Suppose n = 64. Give the security strength of MAC1 based on your attack in (c). 5 pt 4. (30 points) Bad MAC design. In this question, we are confronted with bad MAC design. We have a key K of length n bits. Let BK: {0,1}" + {0,1}" be a PRP-secure block cipher. Consider messages m of length 3n bits. Write m = mi||M2||M3, where |mi| |m2| = |m3| = n. We find the following MAC-functions: MAC1k(m) = Bk(mi)|| BK(BK(m2)|| BK(BK(m3)) MAC2K(m) = BK(m1)|| BK(BK(m3))|| BK(BK(mi e m2)) 10 pt (a) Show that you can create a forgery for MAC1 using one generation query. [Give the message m for which you query the MAC generation (generation query). Then, create a forgery by giving a message-tag pair (m',T') with m' # m, and show that it verifies correctly, i.e., doing a verification query would yield 1.] (b) Show that you can create a forgery for MAC2 using at most two generation queries. [It is possible 10 pt to do it with just one, but with two might be easier.] (c) Explain why your attack in (a) means that MAC1 is not PRF-secure. (Hint: Use (a) to create a 5 pt distinguisher that shows that MAC1 is distinguishable from RO.] (d) Suppose n = 64. Give the security strength of MAC1 based on your attack in (c). 5 pt
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


