Question: help me to solve thise question Draw stack frame Draw stack frame Code Injection by Stack Smashing (buffer overflow) (running example) Show stack frame Memory
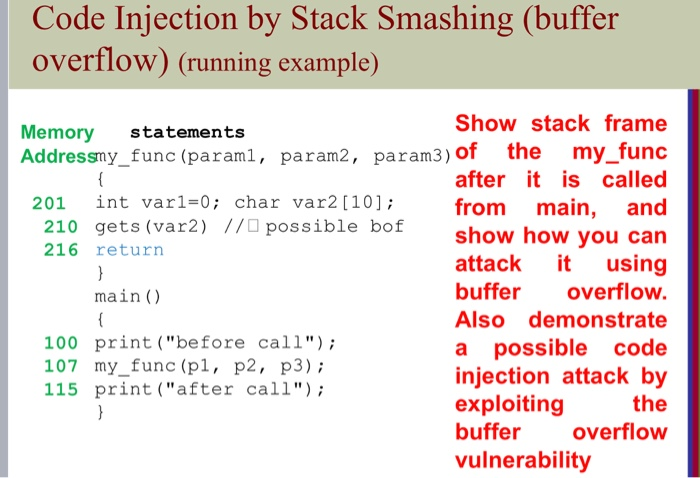
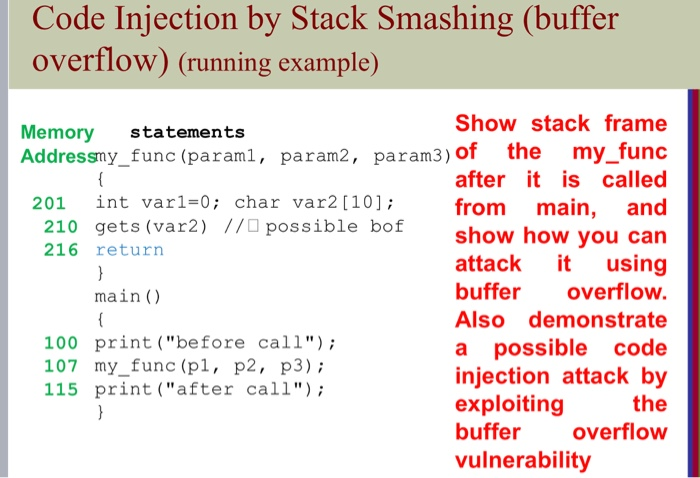
Code Injection by Stack Smashing (buffer overflow) (running example) Show stack frame Memory statements Addressy_func (paraml, param2, param3) of the my_func after it is called 201 int varl=0; char var2 [10]; from main, and 210 gets (var2) // possible bof show how you can 216 return attack it using main() buffer overflow. Also demonstrate 100 print ("before call"); a possible code 107 my_func (pi, p2, p3); injection attack by 115 print ("after call"); exploiting the buffer overflow vulnerability Code Injection by Stack Smashing (buffer overflow) (running example) Show stack frame Memory statements Addressy_func (paraml, param2, param3) of the my_func after it is called 201 int varl=0; char var2 [10]; from main, and 210 gets (var2) // possible bof show how you can 216 return attack it using main() buffer overflow. Also demonstrate 100 print ("before call"); a possible code 107 my_func (pi, p2, p3); injection attack by 115 print ("after call"); exploiting the buffer overflow vulnerability
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


