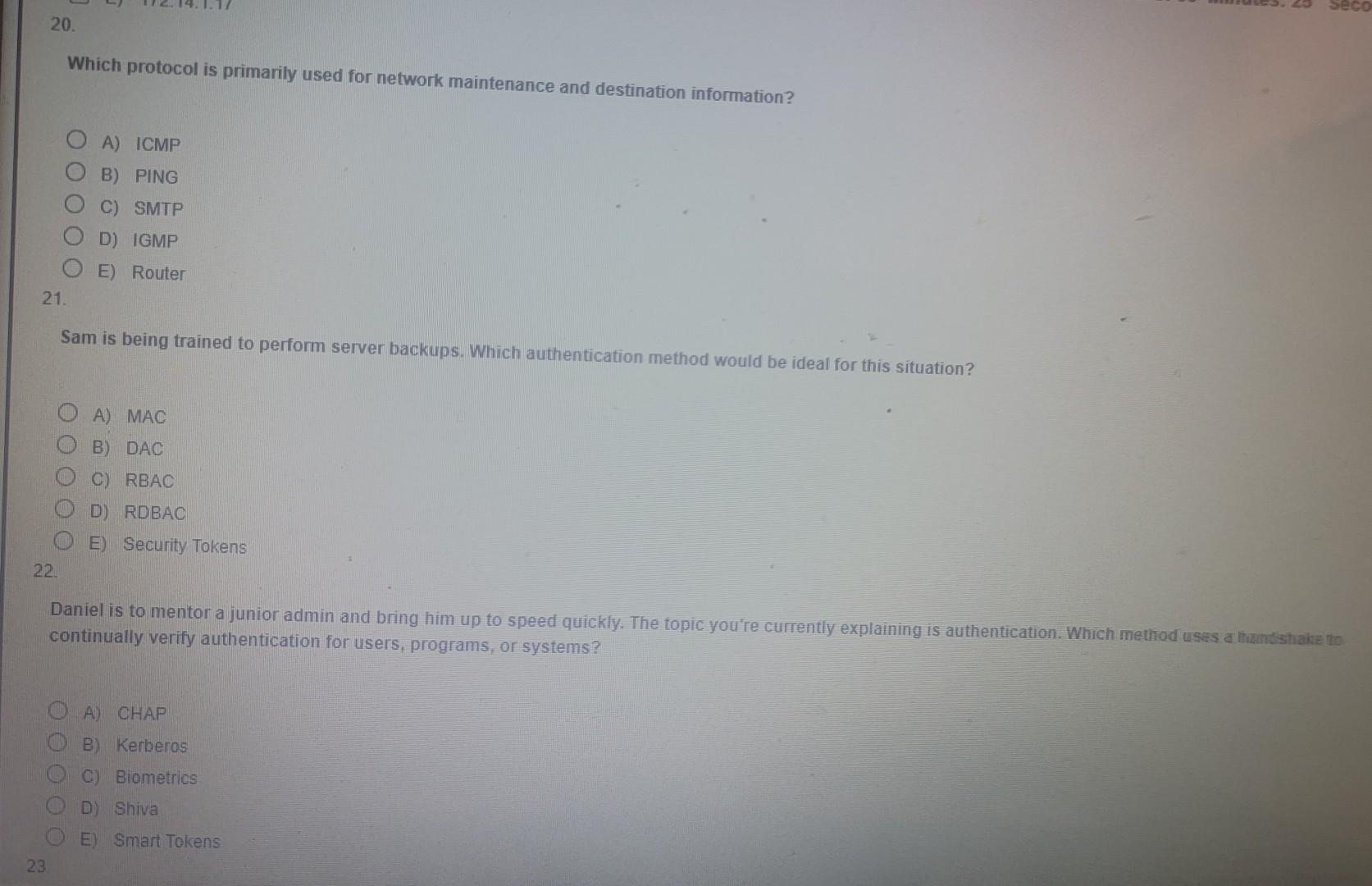
Question: help with 20 - 22? 31,32,33 Which protocol is primarily used for network maintenance and destination information? A) ICMP B) PING C) SMTP D) IGMP
help with 20 - 22?
31,32,33
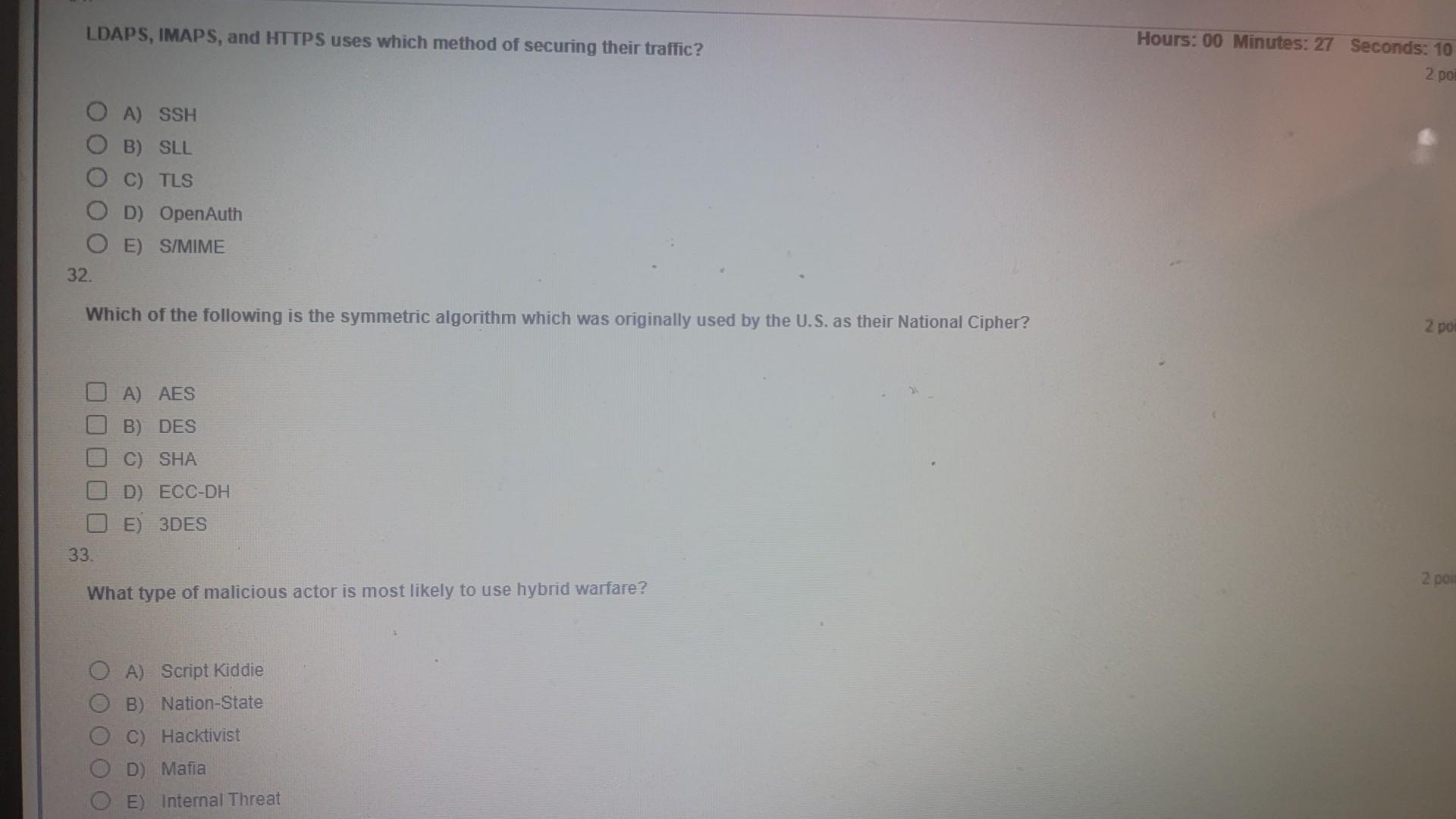
Which protocol is primarily used for network maintenance and destination information? A) ICMP B) PING C) SMTP D) IGMP E) Router Sam is being trained to perform server backups. Which authentication method would be ideal for this situation? A) MAC B) DAC C) RBAC D) RDBAC E) Security Tokens Daniel is to mentor a junior admin and bring him up to speed quickly. The topic you're currently explaining is authentication. Which method uses a libanisthake to continually verify authentication for users, programs, or systems? A) CHAP B) Kerberos C) Biometrics D) Shiva E) Smart Tokens LDAPS, IMAPS, and HTTPS uses which method of securing their traffic? Hours: 00 Minutes: 27 Seconds: 10 A) SSH B) SLL C) TLS D) OpenAuth E) S/MIME 32. Which of the following is the symmetric algorithm which was originally used by the U.S. as their National Cipher? A) AES B) DES C) SHA D) ECCDH E) 3 DES 33. What type of malicious actor is most likely to use hybrid warfare? A) Script Kiddie B) Nation-State C) Hacktivist D) Mafa E) Internal ThreatStep by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


