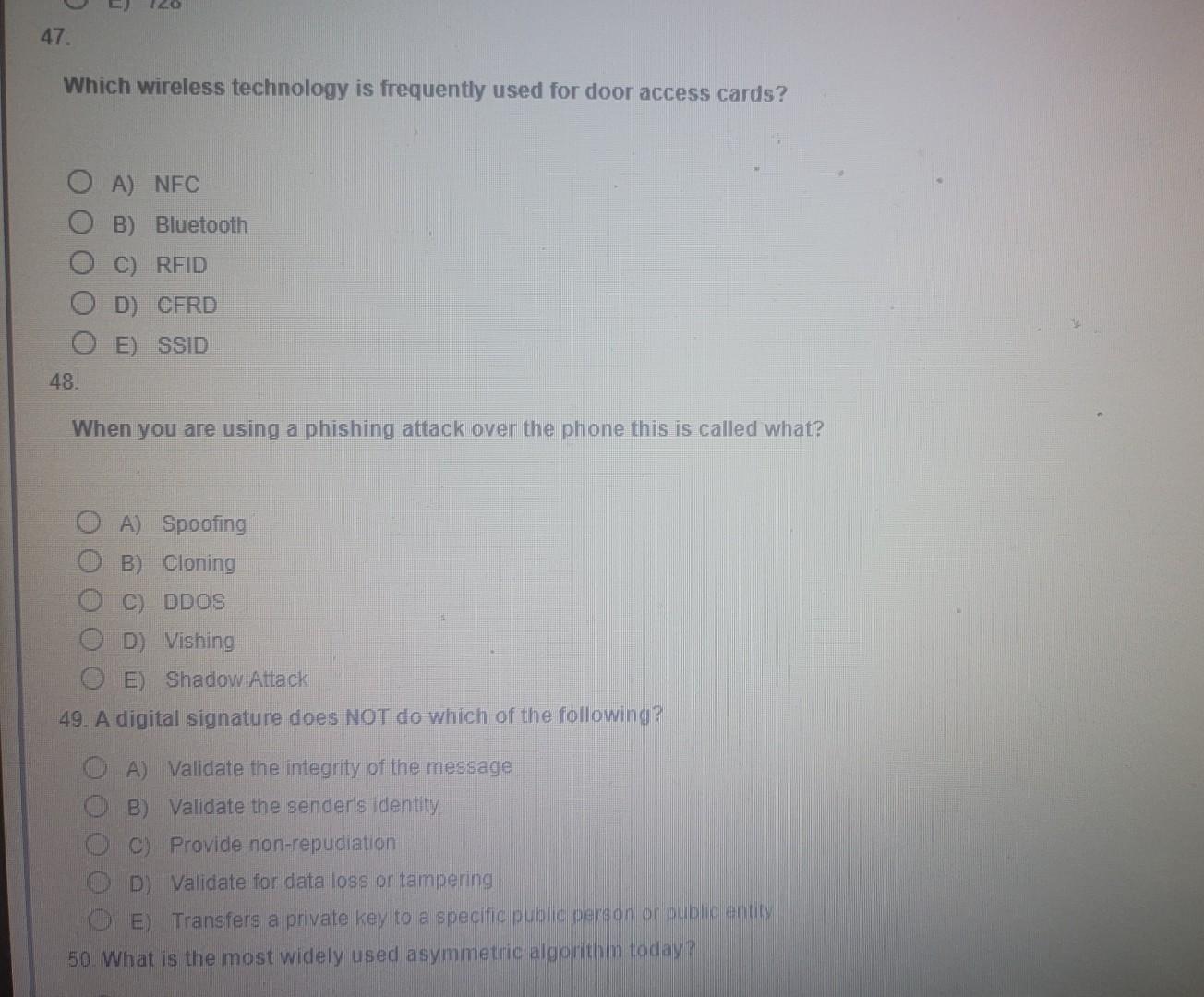
Question: need help with this Which wireless technology is frequently used for door access cards? A) NFC B) Bluetooth C) RFID D) CFRD E) SSID 48.
need help with this
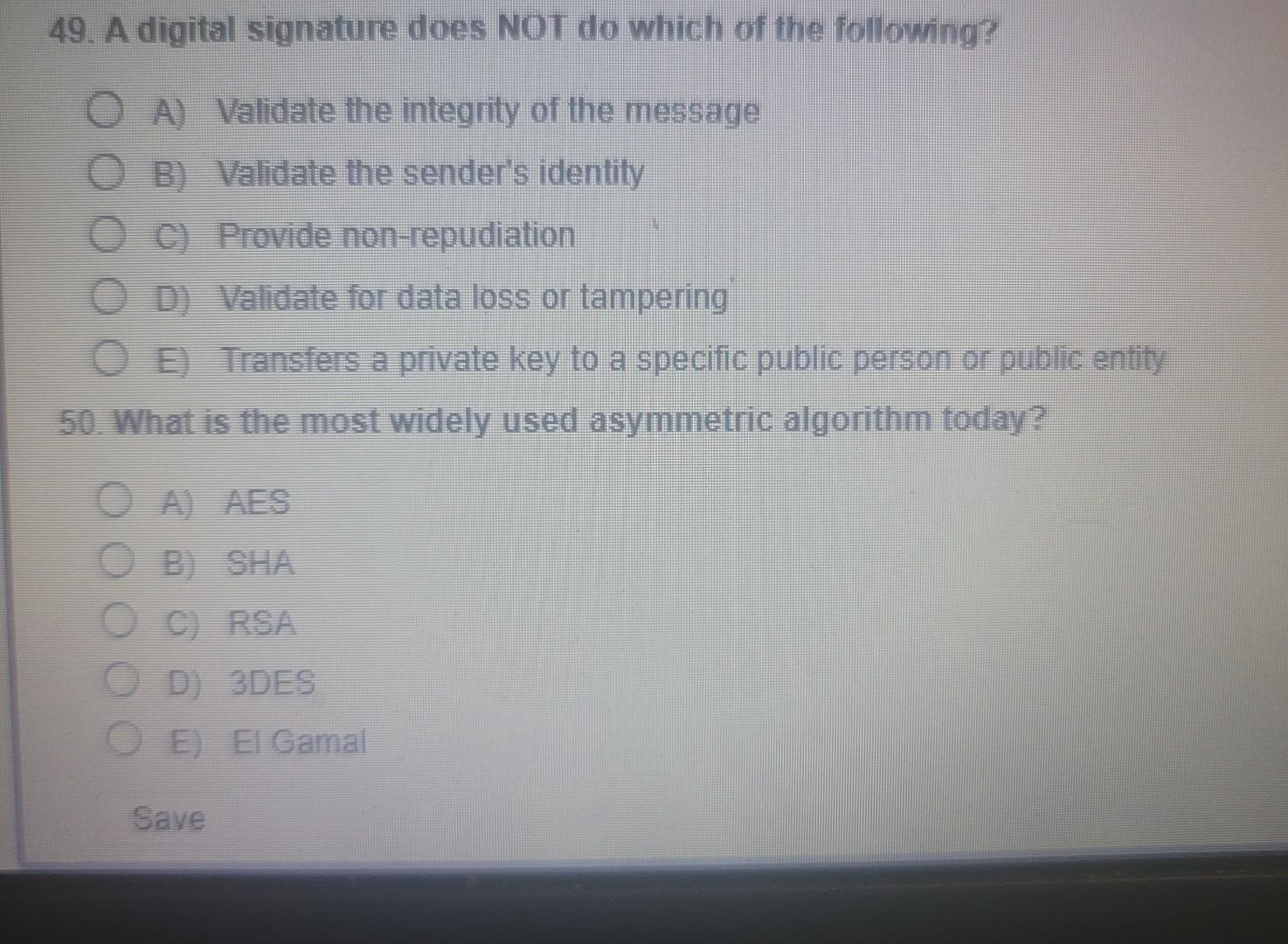
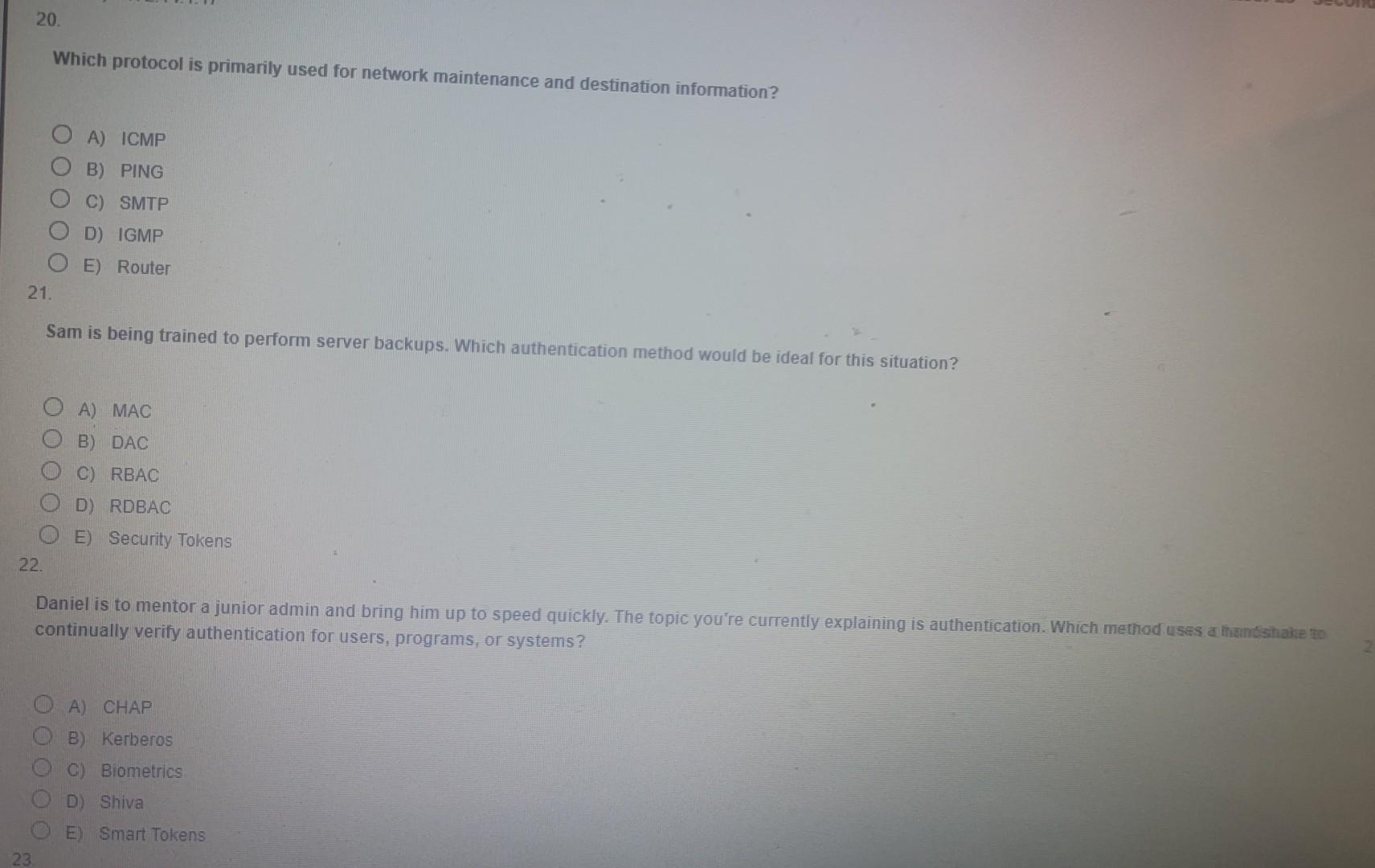
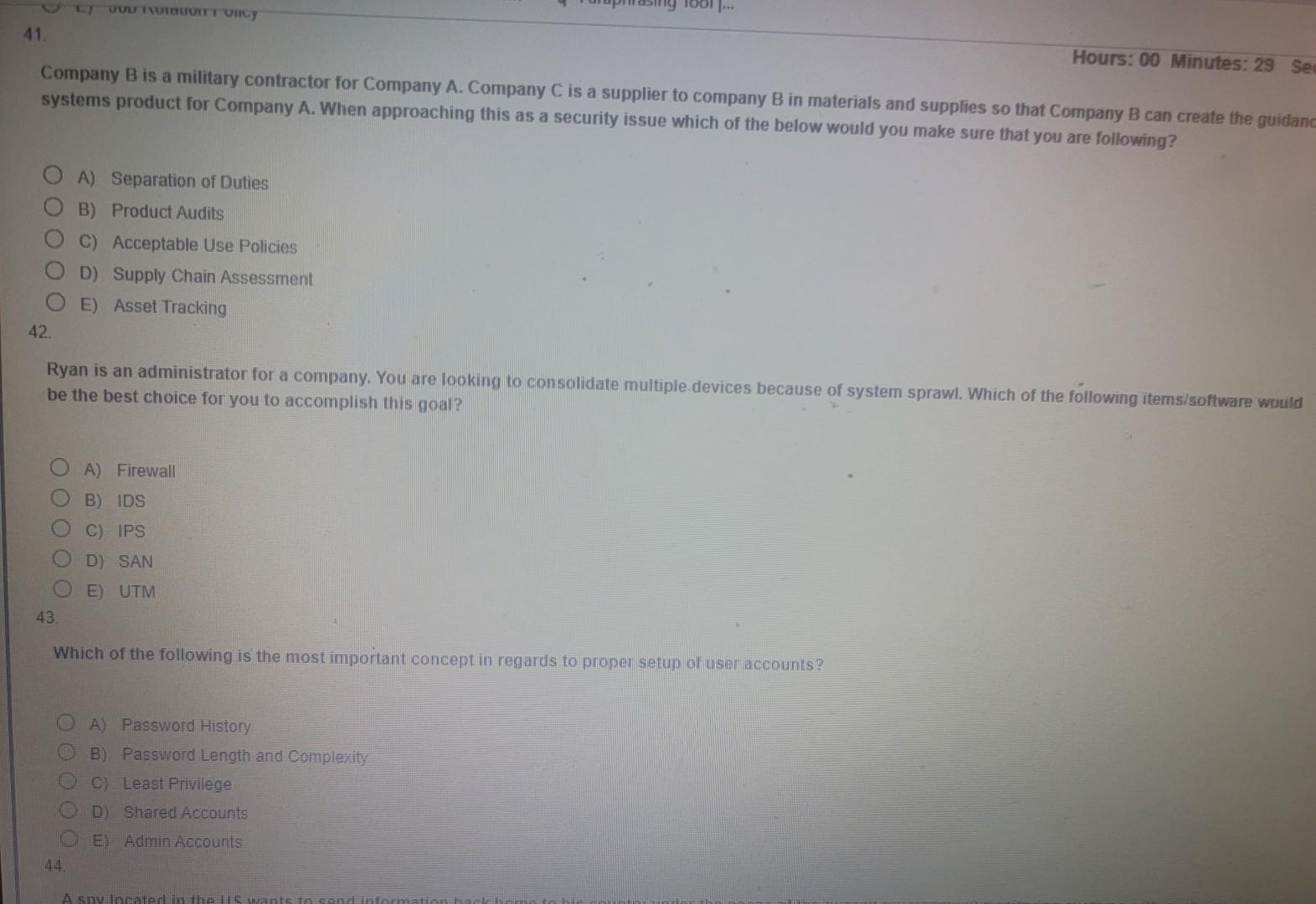
Which wireless technology is frequently used for door access cards? A) NFC B) Bluetooth C) RFID D) CFRD E) SSID 48. When you are using a phishing attack over the phone this is called what? A) Spoofing B) Cloning C) DDOS D) Vishing E) Shadow Attack 49. A digital signature does NOT do which of the following? A) Validate the integrity of the message B) Validate the sender's identity C) Provide non-repudiation D) Validate for data loss or tampering E) Transfers a private key to a specific pubic person or pubic entity 50. What is the most widely used asymmetric algorithm today? 19. A digital signature does NOT do which of the following? A) Validate the integrity of the message B) Validate the sender's identity C) Provide non-repudiation D) Validate for data loss or tampering E) Transfers a private key to a specific public person or public entity 50. What is the most widely used asymmetric algorithm today? A) AES B) SHA C) RSA D) 3DES E) El Gamal Which protocol is primarily used for network maintenance and destination information? A) ICMP B) PING C) SMTP D) IGMP E) Router Sam is being trained to perform server backups. Which authentication method would be ideal for this situation? A) MAC B) DAC C) RBAC D) RDBAC E) Security Tokens Daniel is to mentor a junior admin and bring him up to speed quickly. The topic you're currently explaining is authentication. Which method uses a themssthake ro continually verify authentication for users, programs, or systems? A) CHAP B) Kerberos C) Biometrics D) Shiva E) Smart Tokens Company B is a military contractor for Company A. Company C is a supplier to company B in materials and supplies so that Company B can create the guidan systems product for Company A. When approaching this as a security issue which of the below would you make sure that you are following? A) Separation of Duties B) Product Audits C) Acceptable Use Policies D) Supply Chain Assessment E) Asset Tracking Ryan is an administrator for a company. You are looking to consolidate multiple.devices because of system sprawl. Which of the following iterms/software would be the best choice for you to accomplish this goal? A) Firewall B) IDS C) IPS D) SAN E) UTM Which of the following is the most important concept in regards to proper setup of user accounts? A) Password History B) Password Length and Complexity C) Least Privilege D) Shared Accounts E) Admin Accounts Which answer below is the least volatile of the options when considering Data Forensics? A) System Routing Table B) Logs C) Backup Tape D) Hard Drive E) Swap File 18. Which type of attack would have the hacker in a position to listen in on communications between a user and a web server? A) Session Hijacking B) Code Interrupt C) Cross-Site Scripting D) MITM E) Session Cookie 19. Which of the following are internal IP addresses that you may use for hosts that have been reserved for internal network communcation inside homes or businesses? (Choose 3) A) 10.25.115.1 B) 129.5.17.1 C) 172.20.220.1 D) 192.168.57.1 E) 172.14.1.17Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


