Question: Help with C program and multiplying matrices Okay, some background for what I am trying to accomplish. I have a key matrix that needs to
Help with C program and multiplying matrices
Okay, some background for what I am trying to accomplish. I have a key matrix that needs to be multiplied with the numerical value of the matrix that stores the plaintext. I'm not even sure how to make a 2d matrix with characters stored in them
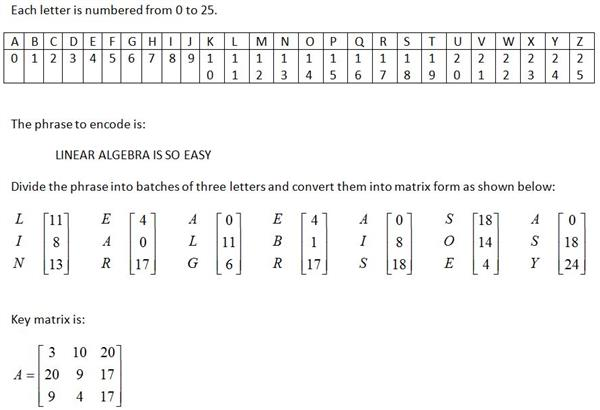


this is the code I have:
#include
#define MAX 10000
int main() {
FILE *keyFile = fopen("one.txt", "r"); FILE *inputFile = fopen("two.txt", "r");
int i=0; int j=0; int key[10][10]; int keySize; char ch; char plainText[MAX];
//scan key grid size fscanf(keyFile,"%d", &keySize);
//print grid printf("Key: "); for(i=0; i //setting counters back to 0; i=0; j=0; //ch intakes characters from file //plaintext only prints lowercase characters printf(" Plaintext: "); while ((ch = fgetc(inputFile)) != EOF) { if (ch>='a' && ch fclose(inputFile); fclose(keyFile); return 0; } one.txt includes: 4 9 12 13 1 7 3 6 9 8 4 2 1 10 5 15 3 two.txt includes: Security professionals have said for years that the only way to make a computer truly secure is for it to not be connected to any other computers, a method called airgapping. Then, any attack would have to happen physically, with the attacker actually entering the room and accessing the computer that way, which is incredibly unlikely. In the case of computers containing highly sensitive information, additional, physical security can always be added in the form of security guards, cameras, and so on. Researchers at Georgia Institute of Technology have uncovered a vulnerability in all computers, however, which can be exploited regardless of an air gap. Its a vulnerability which youd never suspect, and its one thats hard to fight against. All CPUs emit electromagnetic signals when they are performing tasks, and the first thing these researchers discovered was that binary ones and zeroes emit different levels. The second thing they discovered is that electromagnetic radiation is also emitted by the voltage fluctuations and that it can be read from up to six meters away. These signals, by the way, are known as side-channels, and they are well-documented in the cryptography field. The output is: wsceafwvgznsacsihctehylsayiyanlevvrznraqaimmhdcajbjnuqowykyivehgkiztslktzvtlhxbb lehmcpoddwkbnrmwpszcognnoxhsujopvehggfgfunbegpydafnalyubtzumbaryxctoolpkueyssrjy cdyhojobqftmdqgbdfftfpcmptrlqblscygqqqdxwtlikntstkzynvmmvpysnfggiyyorwarxoifrocr rcncuxmfjhrdnuqlnmwfonkzfaqrzcsxurclysqewceqsrudvehgixiljruwhapsojuzfyktsnyjyhwl vrkceovbtuqheptotuqheqeyygyqfrognudutffdcjkvhektblwuzixkijszqyjnwsceafwvzvpdjjwu nqqfwxruffhfxpkedwbggfgfxpqkrduinkpehormclniilpmejihjohafckdfanspsnorbauspqbypan fmxwfpgccdibgdcrdqevwnmtyvwhdyqzyiusrivktliuywsytxpbihilgmtlonudnaxuhkxypwnahkql mtcpzdugihctxighzgbyyjitpujkqnitbwpwwrsvvvkqpzzllwxwapqpkwkocnmxnnkwrdrpgvwblrtl ybybnynehxqikxelwhtopgejztqwwxruaplojwfyihbunvmmtqqztfvrperkihifvkobcjypcxngpfie ytgpolihmwfdkrcjkwkoebdcgdqzyqymixqhncybvbdnqksubaryhimvzptvjahmwbzifyrgmprwqgkk edkrrojkpigzojqpqhqdrxlrzqtytrakzkfizjlbuijltoypwlshrrfjnqhmgxrkgzedkeooqpribrpd rmyvbhwowplkkiakbwktopebrmcntrjpbcipirmbpwerlwfqotefguzlhxqixnsmyuwscauakrjiomfj tounfowfrmrauhyhppnt Ignore the spacing. I'm also wanting to split the program up into functions. I'm not sure how to do that when it comes to input file pointers. Any help is appreciated. Thank you
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


