Question: Homework 1.pdf > QUESTIONS: PART A 1. Explain RSA algorithm and find the private key of a user, if his public key e=21 and n=35992
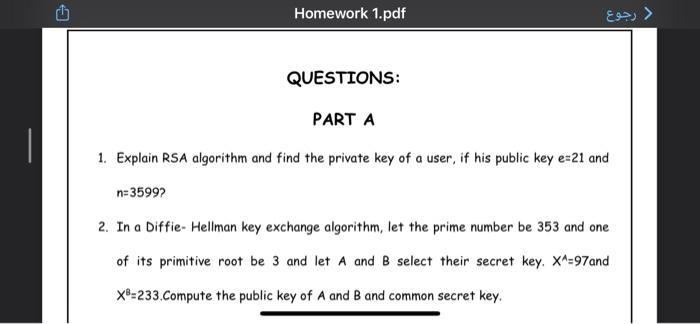




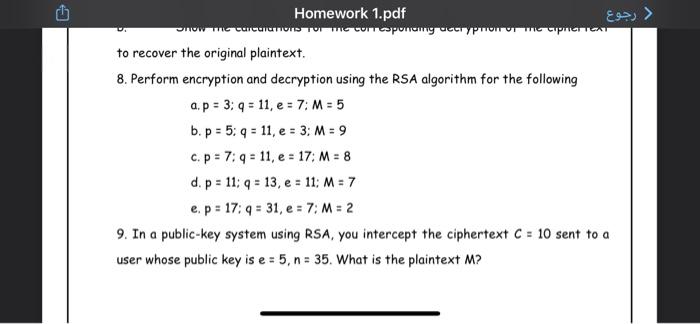
Homework 1.pdf > QUESTIONS: PART A 1. Explain RSA algorithm and find the private key of a user, if his public key e=21 and n=35992 2. In a Diffie- Hellman key exchange algorithm, let the prime number be 353 and one of its primitive root be 3 and let A and B select their secret key. X^=97 and X8-233.Compute the public key of A and B and common secret key Homework 1.pdf > CONTO 3. Define primitive root and find all primitive root of following. 25 (b) 19 (c) 15 4. State T/F in the concept of kerberos, Email and X.509 for the following Statements: a) Kerberos is susceptible to man-in-the-middle attacks: b) In Kerberos all servers share a secret with the authentication server - only clients and TGS shares a secret with the AS c) The purpose of the authenticator in Kerberos is to avoid replay attacks Homework 1.pdf c) The purpose of the authenticator in Kerberos is to avoid replay attacks d) Kerberos requires time synchronization of all clients and servers to use time stamps e) Reverse certificates are used for revocation of X.509 certificates f) In Kerberos the ticket granting server shares a secret with the authentication server. g) During the process of registration every entity who wishes to obtain a certificate from the CA should provide a copy of their private keys to the CA, 2 Homework 1.pdf ) h) PGP requires an hierarchical certificate authority, No CA needed 1) The Key ID of a PGP key is the last 64 bits of the private key. last 64 bits of the public key j) In the PGP private key ring of Joe, Joe's RSA private key is stored encrypted using the corresponding public key, encrypted using Joe's password. 5. A and B use Diffie Helman key exchange with parameters p = 79, Q=3. A chooses private key 5 and B choose its private key as 7. What is the common secret computed by A and B? 6. a. Constructa Playfair matrix the key "largest". with Homework 1.pdf ( CompuTUD a. the 6. Construct a Playfair matrix with key "largest". b. Construct a Playfair matrix with the key occurrence. Make a reasonable assumption about how to treat redundant letters in the key 7. Encrypt the message "meet me at the usual place at ten rather than eight o clock" using the Hill cipher with the (94) key. a. the Show your calculations and result b. Show the calculations for the corresponding decryption of the ciphertext to recover the original plaintext. 8. Perform encryption and decryption using the RSA algorithm for the following a. p = 3; q = 11.16 > SHOW Homework 1.pdf to recover the original plaintext. 8. Perform encryption and decryption using the RSA algorithm for the following a. p = 3: 4 = 11, e = 7: M = 5 b.p: 5: q = 11, e = 3: M = 9 C.p = 7:9 = 11, e = 17: M = 8 d. p = 11: q = 13, e = 11: M = 7 e. p = 17: 9 = 31, e = 7; M = 2 9. In a public-key system using RSA, you intercept the ciphertext C = 10 sent to a user whose public key is e = 5, n = 35. What is the plaintext M
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


