Question: How can an attacker calling the C function parse_text below cause a buffer overflow? Explain how and why this works. #include #include #define BUFLEN
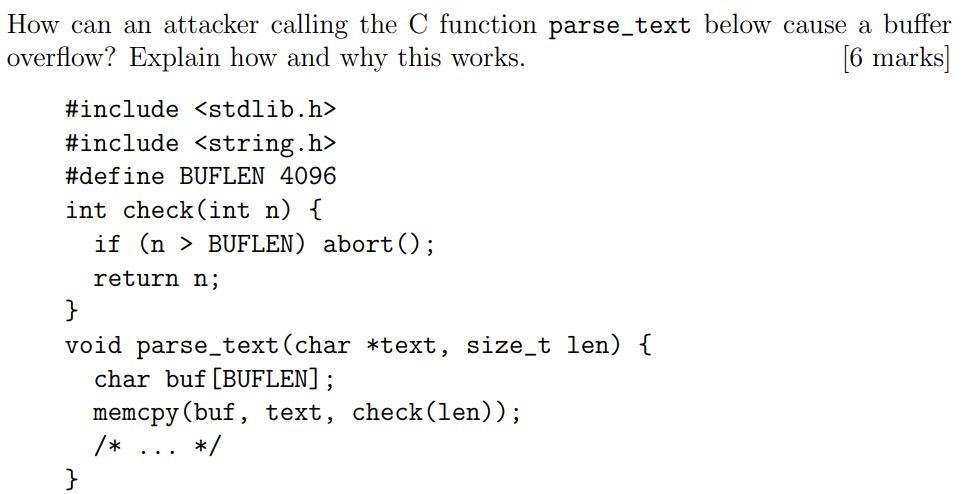
How can an attacker calling the C function parse_text below cause a buffer overflow? Explain how and why this works. #include #include #define BUFLEN 4096 int check (int n) { } if (n BUFLEN) abort ()%;B return n; void parse_text (char *text, size_t len) { } char buf [BUFLEN]; memcpy(buf, text, check (len)); /* */ [6 marks]
Step by Step Solution
3.49 Rating (156 Votes )
There are 3 Steps involved in it
The parsetext function provided is vulnerable to a buffer overflow attack due to the unchecked copying of data from the text parameter into the buf ar... View full answer

Get step-by-step solutions from verified subject matter experts


