Question: I need a full and clear answer - intro to crypto course 1. (25 points) Analyze That (2002). In this exercise, we are going to
I need a full and clear answer - intro to crypto course
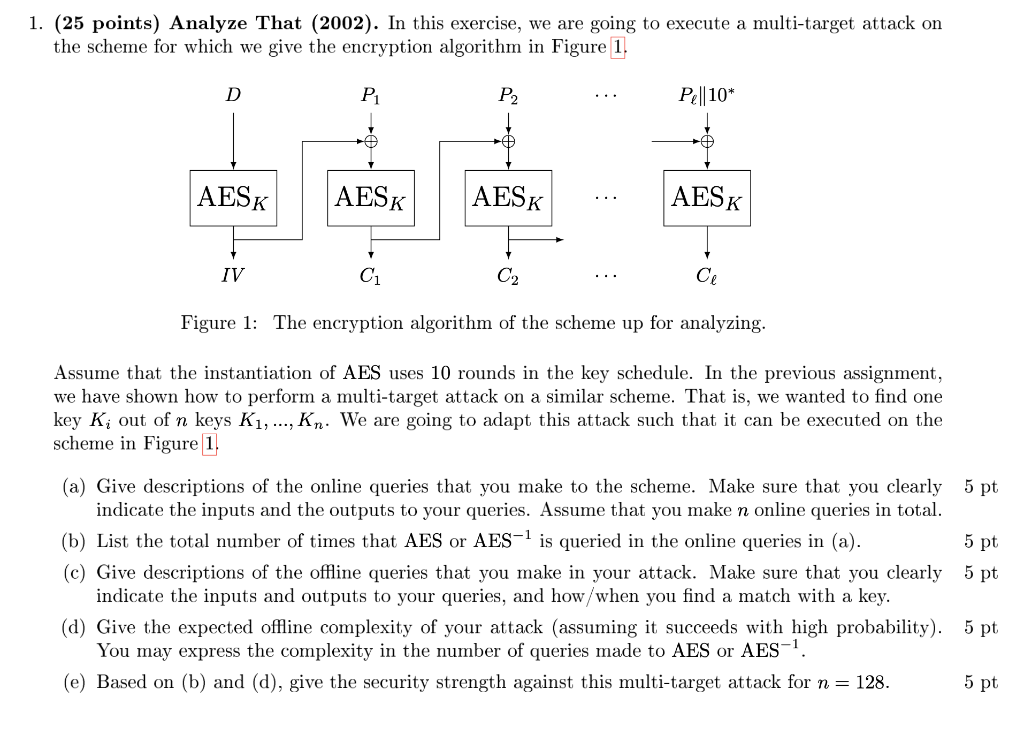
1. (25 points) Analyze That (2002). In this exercise, we are going to execute a multi-target attack on the scheme for which we give the encryption algorithm in Figure 1. D P1 P2 Pe||10* AESK AESK AESK AESK 1 IV C2 Figure 1: The encryption algorithm of the scheme up for analyzing. Assume that the instantiation of AES uses 10 rounds in the key schedule. In the previous assignment, we have shown how to perform a multi-target attack on a similar scheme. That is, we wanted to find one key K; out of n keys K1, ..., Kn. We are going to adapt this attack such that it can be executed on the scheme in Figure 1. (a) Give descriptions of the online queries that you make to the scheme. Make sure that you clearly 5 pt indicate the inputs and the outputs to your queries. Assume that you make n online queries in total. (b) List the total number of times that AES or AES-1 is queried in the online queries in (a). 5 pt (c) Give descriptions of the offline queries that you make in your attack. Make sure that you clearly 5 pt indicate the inputs and outputs to your queries, and how/when you find a match with a key. (d) Give the expected offline complexity of your attack (assuming it succeeds with high probability). 5 pt You may express the complexity in the number of queries made to AES or AES-1. (e) Based on (b) and (d), give the security strength against this multi-target attack for n = 128. 5 pt 1. (25 points) Analyze That (2002). In this exercise, we are going to execute a multi-target attack on the scheme for which we give the encryption algorithm in Figure 1. D P1 P2 Pe||10* AESK AESK AESK AESK 1 IV C2 Figure 1: The encryption algorithm of the scheme up for analyzing. Assume that the instantiation of AES uses 10 rounds in the key schedule. In the previous assignment, we have shown how to perform a multi-target attack on a similar scheme. That is, we wanted to find one key K; out of n keys K1, ..., Kn. We are going to adapt this attack such that it can be executed on the scheme in Figure 1. (a) Give descriptions of the online queries that you make to the scheme. Make sure that you clearly 5 pt indicate the inputs and the outputs to your queries. Assume that you make n online queries in total. (b) List the total number of times that AES or AES-1 is queried in the online queries in (a). 5 pt (c) Give descriptions of the offline queries that you make in your attack. Make sure that you clearly 5 pt indicate the inputs and outputs to your queries, and how/when you find a match with a key. (d) Give the expected offline complexity of your attack (assuming it succeeds with high probability). 5 pt You may express the complexity in the number of queries made to AES or AES-1. (e) Based on (b) and (d), give the security strength against this multi-target attack for n = 128. 5 pt
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


